Transcription
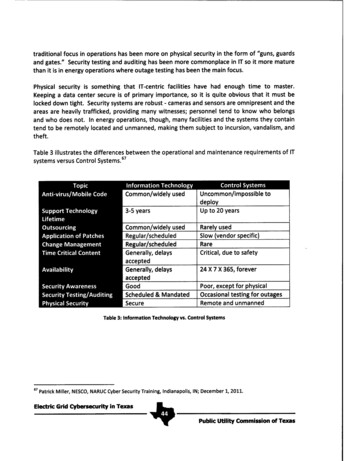
traditional focus in operations has been more on physical security in the form of "guns, guardsand gates." Security testing and auditing has been more commonplace in IT so it more maturethan it is in energy operations where outage testing has been the main focus.Physical security is something that IT-centric facilities have had enough time to master.Keeping a data center secure is of primary importance, so it is quite obvious that it must belocked down tight. Security systems are robust - cameras and sensors are omnipresent and theareas are heavily trafficked, providing many witnesses; personnel tend to know who belongsand who does not. In energy operations, though, many facilities and the systems they containtend to be remotely located and unmanned, making them subject to incursion, vandalism, andtheft.Table 3 illustrates the differences between the operational and maintenance requirements of ITsystems versus Control Systems.67. - . u. . .Common/wide(y used. I 14 .Uncommon/impossible todeploy3-5 yearsUp to 20 yearsCommon/widely usedRegular/scheduledRegular/scheduledGenerally, delaysacceptedGenerally, delaysacceptedGoodScheduled & MandatedSecureRarely usedSlow (vendor specific)RareCritical, due to safety24 X 7 X 365, foreverPoor, except for physicalOccasional testing for outagesRemote and unmannedTable 3: Information Technology vs. Control Systems67 Patrick Miller, NESCO, NARUC Cyber Security Training, Indianapolis, IN; December 1, 2011.Electric Grid Gybersecurity in Texas,.Public Utility Commission of Texas
i rEf;x.wE KE .("" i "t4WFB' EM4 f -.j GVI'EAN.EE.55s.FE4M!Ki 1Uc{ ) !l mi w carr r .J- . ltr. -- scvwar;srRr:n- r -i7 . .,. OG rWV L (. i ' wzc nr.c.e.,.y.„ 41tMSEF E Y1.Y.m. Clftt .GNUaCe' CE%.,.r.CFSKQPI Uamn.n.Damon MMd wr. ,,.v.,.i So.w.50{ Sxrw 4n1/.c.mef 6G5 xJe912Y1IX17Er an Qe ISeroa J', .y,w . , Figure 13: Example of a typical IT network.Figure 13 depicts a simplified version of a typical IT-only network. Most devices on the networkare servers or networking equipment.6869 Source: 10/network-diagram.jpg .Electric Grid Cybersecurity in Texas40 Public Utility Commission of Texas
MW. «oseSCADANetwork.I.caftwmw." «Oan,.SOFV"FieldDevicesLocal eny"Figure 14: Simplified Example of Electric Utility Control System Network,Source: ure 14 shows a simplified example of an electric utility's control system network.69 Thecloud in the upper left labeled "Corporate LAN" is a typical IT-only network, as seen in Figure13. This diagram differs in that it also has representations of field devices such as PLCs, RTUs,70and IEDs" on a segregated SCADA network. Some of these field devices sense things in thephysical domain (providing sensory inputs), while others perform computational functions, andthe remaining devices direct equipment to perform physical actions.Rather than employing existing standard security practices that are put in place to protect theIT infrastructure of the business portion of an enterprise, these practices must be altered toaccommodate the unique characteristics of the electrical infrastructure and tailored so thatthey will not cause a disruption in energy operations.69 Source: http://eioc.pnnl.gov/research/cybersecurity.stm .70 Remote Terminal Unit.71 Intelligent Electronic Device.Electric Grid Gy/bersecurity in TexasPublic Utility Commission of Texas
Challenge: Cultural Differences between IT and OTAnother challenge of implementing cybersecurity in utilities is related to the industry's culture.Utility operations have traditionally been dominated by engineers, who are educated andtrained to understand the underlying science behind electricity, as well as the systems andinstrumentation used to measure, control, and direct it. Over the years, the engineeringenvironment has incorporated an increasing amount of computer systems, and work processeshave also been adapted to accommodate the use of IT. Many utility operations people typicallyhave years of experience in the field, many having come into the industry at some point duringthe 1970s or 1980s with long tenure at the same utility.It has been widely acknowledged in the United States that qualified engineers are increasinglydifficult to come by. Finding the kind of engineers that either already have or would developspecialized knowledge to potentially become a utility operator is arguably even more difficult.Students of the past few decades have had a diminished interest in pursuing science- andengineering-based courses of study, while other career paths generally have become moreattractive to them. Exacerbating the problem is the fact that many utilities typically havefacilities scattered across rural territories that are sparsely populated. A graduating studentpursuing employment would likely be required to relocate to such an area or commute longdistances, which may be a deterrent to accepting a job offer.Information Technology, on the other hand, has a broader appeal, as evidenced by increasedstudent enrollments in college IT and Computer Science programs over the past two decades.IT has become more pervasive in general, thereby offering what has been perceived by newstudents as more opportunities upon graduation. Further, web-based technologies haveenabled the workforce to be more mobile - not just for the users of the technology, but forthose who create it. A programmer can relocate to a community which he thinks is his mostdesired place to live and then work remotely. In many cases, an IT worker can eventelecommute and work from his home. An IT worker has many choices compared to a typicalutility worker. Therefore, the tenure of a typical IT staff member at any given company isrelatively short and IT staff turnover at firms is rather high.The distinctions between the OT and IT workforces are important to note, because as OTcontinues to automate, it is taking on more of the characteristics of IT. As a result of thisconvergence, management at utilities leans on their IT staffs for support in functions that wouldbe ideally handled by someone with operational (i.e. OT) knowledge and experience. Theproblem with this is that IT staffers tend to be computer-focused in approach and do notpossess the understanding of real-world processes that an engineer would have. Further,whereas IT security has developed in conjunction with business process automation over thepast couple decades, OT Security is a relatively new concept. Solutions devised for an ITElectric Grid Gy/bersecurity in Texas/Public Utility Commission of Texas
environment cannot just be plugged into the OT environment without the possibility of adverseconsequences.Challenge: Security versus ComplianceWhen it comes to security considerations, the threat of fines that may be imposed upon utilitiesby NERC for noncompliance with its CIP standards can potentially take center stage in a dialogabout security. This is only natural since fines can be readily defined in terms of dollars takenfrom the company's bottom line; money is the lingua franca of all business functions.One of the primary goals of the PUC is to ensure that the grid remains safe and reliable. Toaccomplish this goal, commission Staff encourages utilities to promote a culture of security.The PUC is aware that one of the traps that a utility can fall into is having a mindset that isfocused more on compliance than on security, in which the utility is doing the minimumnecessary to meet an audit or to achieve regulatory compliance. In contrast, the pursuit ofsecurity is doing what is necessary, often within the compliance or audit structure, to reduceBeing able torisk to an acceptable level as defined by the requirements of the business.discern the difference is important because mandating a compliance-based approach can beviewed as only an interim step that comes with the caveat that this alone may not save onefrom an attack.Once the tenets of security are wholly embraced by an organization, compliance will followmore easily. One must avoid the notion that security can be merely "bolted on" rather than"built-in" to the organizational culture, just as the concept applies to any equipment that autility may want to acquire. The topic of capital equipment procurement will be discussed in asubsequent section of this report.Staff also encourages utilities to consider looking into the possibility of acquiring compliancereporting automation solutions to lessen the administrative burden of NERC CIP audits. Thatway, instead of committing substantial resources to dealing with the paperwork associated withdemonstrating compliance, utilities' subject matter experts can instead concentrate on theirsecurity activities.Electric Grid Cy6ersecurity in Texas,,Public Utility Commission of Texas
Roles: Who Is Protecting Us?Figure 15 shows the many federal legislative committees and agencies of the executive branchthat are involved in cybersecurity for the electric sector.72Ymite HDVSEConqessHOu5 tWnOSecurrtYDepaRn401 ofEnergrFeGerat EnergyReqJaioryCorrmr sunHouse Energy8 CommerceIHoase&pectCOMM" OnINall0na11nGtSeutWreAO SOry COUnNIMEII1qenCeSenate Homelano5