Transcription
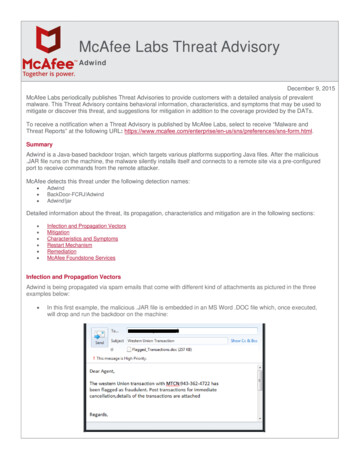
McAfee Labs Threat AdvisoryAdwindDecember 9, 2015McAfee Labs periodically publishes Threat Advisories to provide customers with a detailed analysis of prevalentmalware. This Threat Advisory contains behavioral information, characteristics, and symptoms that may be used tomitigate or discover this threat, and suggestions for mitigation in addition to the coverage provided by the DATs.To receive a notification when a Threat Advisory is published by McAfee Labs, select to receive “Malware andThreat Reports” at the following URL: ences/sns-form.html.SummaryAdwind is a Java-based backdoor trojan, which targets various platforms supporting Java files. After the malicious.JAR file runs on the machine, the malware silently installs itself and connects to a remote site via a pre-configuredport to receive commands from the remote attacker.McAfee detects this threat under the following detection names: AdwindBackDoor-FCRJ!AdwindAdwind!jarDetailed information about the threat, its propagation, characteristics and mitigation are in the following sections: Infection and Propagation VectorsMitigationCharacteristics and SymptomsRestart MechanismRemediationMcAfee Foundstone ServicesInfection and Propagation VectorsAdwind is being propagated via spam emails that come with different kind of attachments as pictured in the threeexamples below: In this first example, the malicious .JAR file is embedded in an MS Word .DOC file which, once executed,will drop and run the backdoor on the machine:
The malicious .JAR file comes as a single attachment or as one of the multiple files attached to the email.We can see that it came with a separate PDF file in this second example:
In this third example, the malicious .JAR file was a single attachment:The subjects can be various (non-exhaustive list): ***SPAM*** Re: Payment/TR COPY-Urgentcredit note for outstanding payment of InvoiceFwd: //Top Urgent// COPY DOCSRe:Re: Re:Re:Re TT copy & PIs with Amendments very urgent.PO#939423Western Union TransactionAnd the .JAR filenames as well (non-exhaustive list): Shipment copies (2).jarFUD FIle.jarPO 8324979(1).jarShipping Documents.jarTelex Copy.jarINSTRUCTIONCZ121.jarOrder939423.jarPayment TT COPY.jarSCAN DRAFT COPY BL,PL,CI.jarEnquiries&Sample Catalog CME-Trade.jarTransaction reciept for forma Invoice.jarTT APPLICATION COPY FORM.jarDec.PO.jarCredit Status 0964093 docx.jarMitigationMitigating the threat at multiple levels like file, Registry & URL could be achieved at various layers of McAfeeproducts. Browse the product guidelines available here to mitigate the threats based on the behavior describedbelow in the Characteristics and symptoms section.Refer the following KB articles to configure Access Protection rules in VirusScan Enterprise: KB81095 - How to create a user-defined Access Protection Rule from a VSE 8.x or ePO 5.x console KB54812 - How to use wildcards when creating exclusions in VirusScan Enterprise 8.x
Basic rules on handling emails:Email from unknown senders should be treated with caution. If an email looks strange, do the following: ignore it,delete it, and never open attachments or click on URLs. Opening file attachments, especially from unknownsenders, harbors risks.Never click links in emails without checking the URL. Many email programs permit the actual target of the link to beseen by hovering the mouse over the visible link without actually clicking on it (called the mouse-over function).Never respond to spam emails. A response lets the fraudsters know that the address they wrote to is valid.Access Protection rule:Prevent .JAR files from launching in %AppData%\[random folder name]\, and prevent new .JAR files from beingcreated at this location.McAfee also recommends that you select and test the Files being executed option for the above folders, andadd only known legitimate programs under the Application Data folder to Processes to exclude.Characteristics and SymptomsSeveral variants of Adwind exist, which means that the contents of the Java archives can vary.However, some of the most frequently seen internal file structures are similar to the following: Variant 1
Variant 2
Variant 3 Variant 4 Variant 5
Variant 6On execution, Adwind copies itself at the following location:%AppData%\[random folder name]\[random filename].jarDepending on the variants of Adwind, the Java archive copied in the %AppData% folder may use a different fileextension than “.jar”:%AppData%\[random folder name]\[random filename].[random file extension]It then changes the folder and file attributes to system, hidden and read-only, as shown below:
Finally, it executes the copy of itself located in the %AppData% folder and adds the following registry key, whichwill enable the Java backdoor trojan to run at startup:HKEY CURRENT ] "[random value name" "[JavaRuntime Environment directory]\jawaw.exe” – jar “%AppData%\[random folder name]\[random filename].jar”The Adwind Java backdoor comes in an obfuscated form to hide its malicious intent. Its payload and itsconfiguration file (which serves as an installation file) are encrypted, either with the DES cipher, the RC4 one, orthe RC6 one, depending on the variants.The Adwind backdoor will decrypt itself on-the-fly during execution.For instance, an analysis of an Adwind variant similar to the variant 1 mentioned above, will reveal the followingpieces of information.The first class that will be executed is the one named Adwind.class, as shown in the META-INF/MANIFEST.MFfile:Manifest-Version: 1.0Ant-Version: Apache Ant 1.8.4X-COMMENT: Main-Class will be added automatically by buildClass-Path:Created-By: 1.7.0 09-b05 (Oracle Corporation)Main-Class: Adwind
This class file will first read the file “ID” (the strings are obfuscated in the piece of code pictured above) and willstore its content in a variable named “pass”. The second encrypted string located at the end of the class actuallyturns into “Principal” after it is decrypted. Then, ClassLoaderMod is loaded with the variable named “pass” and thestring “Principal”.The content of the variable “pass” retrieved from the “ID” file is an 8-character string:The ClassLoaderMod class concatenates “.adwind” to the string “Principal” to create a new string“Principal.adwind”, which actually is another resource file located in the Java archive.However, this file looks encrypted:Then, the 8-character string previously retrieved and the “Principal.adwind” file name are passed to the methodConstantion located in the Constante.class file.This method is in charge of the decompression (using a GZIP method) of the Principal.adwind resource file and ofits decryption, thanks to the DES cipher:After it is decrypted, Principal.adwind appears to be another class file. This one contains a hardcoded key that willbe used to decrypt the file config.xml (DES decryption again), and will act as the backdoor installer by reading thedecrypted config.xml file.
Here is the config.xml file in its encrypted form:Its content, after decrypted, consists of: ?xml version "1.0" encoding "UTF-8" standalone "no"? !DOCTYPE properties SYSTEM "http://java.sun.com/dtd/properties.dtd" properties comment Adwind RAT v1.0 /comment entry key "nombreCarpeta" Evsfqcvs /entry entry key "prefijo" Nawjslrh /entry entry key "delay" 14 /entry entry key "puerto2" 101 /entry entry key "dns" msrtcse.noip.me /entry entry key "keyClase" KG5YeHbO /entry entry key "jarname" Mewloyse /entry entry key "puerto1" 100 /entry entry key "instalar" true /entry entry key "password" 645fe9b711cceeb51ec356def13e8b2a396f40b8 /entry entry key "regname" Psyajrgr /entry /properties This decrypted config.xml file contains the folder name that will be created in %AppData% (under the entry"nombreCarpeta"), the file name that will be used to create the copy of the backdoor in %AppData% (under theentry “jarname”), the registry value name that will be added to the HKCU Run key (under the entry “regname”), theserver that will be contacted (under the entry “dns”) and the port numbers that will be used to communicate with theremote attacker (under the entries “puerto1” and “puerto2”).These pieces of information are customized though, and will vary from one Adwind sample to another.All the other files ending with “.adwind” in the Java archive will be decrypted on-the-fly in the same way.Also, depending on the plugins used (additional class files), the backdoor will have more or less functionalities.Some plugins can allow the attacker to: Take screenshots Download some additional files and execute them Modify and delete some files Retrieve some files located on the victim’s machine Log keystrokes Access the webcam Control the mouse and keyboard Update itself
The variants 2,3,4,5,6 are newer variants, and are decrypted differently: Variant 2The Main entry specified in MANIFEST.MF is Start.class.config.perl: this is a XOR encrypted text file.Here is its content after it is decrypted:We can see that it contains the randomly chosen path and filename for the embedded and encrypted maliciousJAR file, and half of the RC6 key that will be used to decrypt it.The other half of the RC6 key will be retrieved from the other available class files.QL1sv1aEo: as seen above, this is the RC6 encrypted malicious .JAR file containing the Adwind backdoor.After this embedded and RC6 encrypted Java archive is decrypted, we eventually gain access to the Adwindbackdoor class files and resources.The “config.json” file shown below is the configuration file (in plain text) of the backdoor, containing thedefined port numbers, servers, the installation path, and so on:
Variant 3The Main entry specified in MANIFEST.MF is Start.class.password.txt: this text file (plain text) contains half of the RC6 key that will be used to decrypt the embeddedmalicious JAR file.The other half of the RC6 key will be retrieved from the other available class files.server.dll: this is the RC6 encrypted malicious JAR file containing the Adwind backdoor. Variant 4The Main entry specified in MANIFEST.MF is Main.class.a.txt: this text file (plain text) contains half of the part of the RC4 key that will be used to decrypt the embeddedmalicious JAR file.The other half of the RC4 key will be retrieved from the other available class files.b.txt: this is the RC4 encrypted malicious JAR file containing the Adwind backdoor. Variant 5The Main entry specified in MANIFEST.MF is Start.class.stubcito.opp: this is the RC6 encrypted malicious JAR file containing the Adwind backdoor.textito.isn: this text file (plain text) contains half of the RC6 key that will be used to decrypt the embeddedmalicious JAR file.The other half of the RC6 key will be retrieved from the other available class files. Variant 6The Main entry specified in MANIFEST.MF is Start.class.
resource.xsx: this is the RC6 encrypted malicious JAR file containing the Adwind backdoor.textito.text: this text file (plain text) contains half of the RC6 key that will be used to decrypt the embeddedmalicious JAR file.The other half of the RC6 key will be retrieved from the other available class files.Notes: %AppData% - C:\Users\[UserName]\AppData\Roaming\Restart MechanismThe following registry entry confirms that the backdoor trojan will start every time when Windows starts:HKEY CURRENT ] "[random value name" "[JavaRuntime Environment directory]\jawaw.exe” – jar “%AppData%\[random folder name]\[random filename].jar”Or, for newer variants, using a random Java archive file extension:HKEY CURRENT ] "[random value name" "[JavaRuntime Environment directory]\jawaw.exe” – jar “%AppData%\[random folder name]\[random filename].[randomextension name]”RemediationThe detection for this malware family is added to the database and would be available from DAT #7899. A FullScan with updated DATS can remove the infection from the machine.Getting Help from the McAfee Foundstone Services teamThis document is intended to provide a summary of current intelligence and best practices to ensure the highestlevel of protection from your McAfee security solution. The McAfee Foundstone Services team offers a full range ofstrategic and technical consulting services that can further help to ensure you identify security risk and buildeffective solutions to remediate security vulnerabilities.You can reach them here: oundstone-services.htmlThis Advisory is for the education and convenience of McAfee customers. We try to ensure the accuracy,relevance, and timeliness of the information and events described; they are subject to change without notice.Copyright 2014 McAfee, Inc. All rights reserved.
McAfee Labs periodically publishes Threat Advisories to provide customers with a detailed analysis of prevalent . The malicious .JAR file comes as a single attachment or as one of the multiple files attached to the email. . the Java archive copied in the %AppDat











