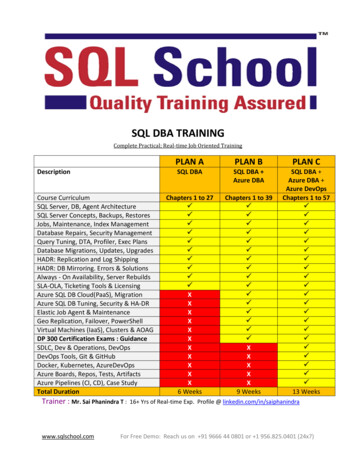
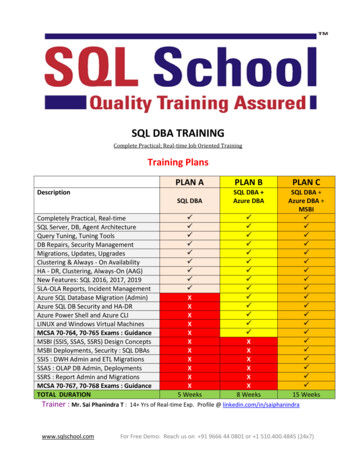
Transcription
Data Masking: The Ultimate DBA Survival Tool in the Modern WorldJagan R. AthreyaOracle CorporationRavi MedaQualcomm, Inc.
The following is intended to outline our generalproduct direction. It is intended for informationpurposes only, and may not be incorporated into anycontract. It is not a commitment to deliver anymaterial, code, or functionality, and should not berelied upon in making purchasing decisions.The development, release, and timing of anyfeatures or functionality described for Oracle’sproducts remains at the sole discretion of Oracle.
Oracle Enterprise ManagerTop-Down, Integrated Application Management Complete, Open, IntegratedManagement for Oracle Technologies– Deep, Optimized, Best of Breed– Database, Middleware, PackagedApplications, Physical and VirtualInfrastructure Business Centric, Top DownApplication Management Complete Lifecycle Management Scalable Grid and Cloud Management– Manage many as one
Agenda Cost of Data Privacy Breaches Implementing Oracle Data Masking Customer Case studies Insert Picture Here
More data than ever GrowthDoublesYearly1,800 Exabytes20062011Source: IDC, 20085
More breaches then ever Data BreachOnce exposed, the data is out there – the bell can’t be un-rungPUBLICLY REPORTED DATA BREACHES400300630%Increase200100Total PersonallyIdentifying InformationRecords Exposed(Millions)02005200620072008Source: DataLossDB, 20096
More threats than ever 7
More Regulations Than Ever UK/PROPIPEDASarbanes-OxleyEU Data DirectivesGLBAPCIBreach DisclosureBasel IIFISMAEuro SOXHIPAAK SOXJ SOXISO 17799SAS 70COBITAUS/PRO90% Companies behind in complianceSource: IT Policy Compliance Group, 2007.8
89% of companies use production customer data - oftenexceeding 10M records - for testing, development, support,training, etc. 74% use consumer data, 24% use credit card numbers!!! Only 23% do anything to suppress sensitive informationand 81% relied on contractual clauses to protect live datatransferred to outsourcers and other third parties 23% said live data used for development or testing hadbeen lost or stolen and 50% had no way of knowing
Ccre ustodit meca rrdsSocial SecurityNumbersBusiness Drivers for Data MaskingSarbanesOxleyPCI-DSSerat gorp tinCo ouncacHIPAAGLBAPatientda heata ltheyeolp esEm alarisCaliforniaDataSecurityBreachBank a/cnumbersEU DataProtectionDirectiveApplicationDevelopers3rd party inicalResearch
What is Data Masking?ProductionNon-ProductionLAST NAMESSNSALARYLAST 4540,000What The act of anonymizing customer,financial, or company confidentialdata to create new, legible datawhich retains the data'sproperties, such as its width, type,and format.SALARYWhy To protect confidential data innon-production environmentswhen the data is shared with nonproduction users without revealingsensitive information
Agenda Cost of Data Privacy Breaches Implementing Oracle Data Masking Customer Case studies Insert Picture Here
Data Masking Methodology1. Find2. Assess3. Secure4. Test
Data Masking Methodology1. Find2. Assess3. Secure4. Test
Find and Catalog Sensitive DataData Finder tool1.Data Finder PatternsTable Name: “EMP*”Column Name “*SSN*”Data Format ### - ## - #### Define pattern match rules for Tables,columns and dataData Privacy Catalog4.PERSON SSN,EMP SSN,SOC SEC NUM New database fields added and thenprotected2.Enterprise Data Sources Search against selected OracleDatabases3.Data Finder ReportsDataFinderResults Results rendered by confidence factor Relevant database fields imported intothe Data Privacy Catalog
Data Masking Methodology1. Find2. Assess3. Secure4. Test
Define Mask Formats and Register in Library Mask Format Library– Mask formats for commonly masked data such as Credit Cardnumber, Social Security Numbers, etc. Mask Primitives to extend Format Library––––––Random NumberRandom StringRandom Date within rangeShuffleSub string of original valueTable Column
Leverage User-defined Mask FormatsEmail notification testing
Extend with Sophisticated Masking Techniques Compound Masks– Sets of related columns masked togethere.g. Address, City, State, Zip, Phone Condition-based Masking– Specify separate mask format for each condition,e.g. driver’s license format for each state Deterministic Masking– Consistent repeatable maskinge.g. John always masks to Joe across multiple databases
Ensure Referential Integrity for the DataDatabase-enforcedApplication-enforced
Data Masking Methodology1. Find2. Assess3. Secure4. Test
AppAdminSeparate Duties between App Admin and DBAIdentifySensitiveInformationAssociatemask formatwith sensitiveinformationDBAMaskDefinitionClone Prodto StagingExecuteMaskFormatLibrary
Integrate with Data Center Processes Secure Clone-and-Mask workflow– Integrated process to create test databases from production– After cloning DB in RESTRICTED mode till masking complete Privilege Delegation Support– Allows mask execution using sudo or PowerBroker Masking script directory specification– Allows DBAs to specify directory location when masking scriptshould be generated
Data Masking Methodology1. Find2. Assess3. Secure4. Test
Customize Mask and Test Post-Mask SQL– for LOBs, attachments, summary values Comparing before & after values– To save the mapping tables to compare before and aftervalues after a mask run during testing REDO log generation– To allow FLASHBACK to pre-masked state when testingmasking routines.
Masking Process – InternalsCapture anddisableConstraints on“sensitive”tableRecreate maskedtable from originaltable replacingsensitive withmasked valuesfrom mappingtables using CTASBuild mapping tablecontaining originalsensitive andmasked valuesusing maskingroutinesDropRenamedtable atisticsRestoreconstraintsbased onoriginal table
High Performance Execution Linux x86 4 CPU: Single core Pentium 4 (Northwood)[D1]) Memory: 5.7G Column scalability– 215 columns masked across 100 tables– 60GB Database– 20 minutes Rows scalability– 100 million row table, 6 columns masked– Random Number– 1.3 hours
Specify Execution Options Statistics Refresh– To enable DBAs to run their own custom statistics generationroutine Degree of Parallelism– To optimize the performance of the mask execution based onthe number of processors available
Validate Mask and Generate Script Ensure uniqueness can bemaintained Ensure formats match columndata types Check Space availability Warn about Check Constraints Check presence of defaultPartitions Generate PL/SQL-basedmasking script uponsuccessful validation
HighLowApplication ComplexityData Masking Implementation Continuum Privacy CatalogApplication DiscoveryMask DevelopmentTest System AutomationApplication TestingPrivacy CatalogMask TemplatesMask DevelopmentTest System AutomationApplication Testing Privacy CatalogApplication DiscoveryMask DevelopmentTest System automationApplication Testing Privacy CatalogMask TemplatesMask DevelopmentTest System AutomationApplication TestingHighPrivacy AwarenessLow
Agenda Cost of Data Privacy Breaches Implementing Oracle Data Masking Customer Case study Insert Picture Here
UK-based Government AgencyData Masking Pack delivered rapid compliance of non-productioneBusiness Suite environmentsBusiness Challenges Internal audit assessment indicated noncompliance with established privacy standards Personnel information at risk of being exposed tonon-production users Needed to bring all their Oracle eBusiness Suitenon-production environments compliant within shortremediation period to pass the auditSolution Data Masking Pack provided flexible routines tomask various types of sensitive data IT team leveraged the extensibility to add userdefine masking routines to meet their needsBusiness Results Successfully met the audit requirements within 4weeks of identifying non-compliance Enabled personnel data in eBusiness Suiteapplication to be shared with non-production usersin line with established standards Provided a successful proof-point for maskingOracle eBusiness Suite applications
EMEA-based Real Estate CompanyData Masking Pack accelerated availability of production data fortesting while improving DBA productivityBusiness Challenges Custom scripts to mask sensitive data were notable to scale to meet growing data volumes DBA team under increasing pressure to makeproduction data available to for application testingwithin short time framesSolution Data Masking Pack delivered an out-of-the-boxsolution to replace custom database scripts High performance masking capabilities acceleratedmasking process from 6 hours using databasescripts to 6 minutes using Data Masking PackBusiness Results 60 X performance improvement in masking processresulted in faster turnaround of test system creation Improved DBA productivity by eliminated therequirement to maintain custom scripts
Oracle Data Masking Solution UsingOracle Enterprise ManagerRavi MedaQualcomm Inc.
Database ServicesAgenda1. Overview of OEM Grid control Infrastructure2. Current Data Scrambling issues3. Oracle Data Masking Implementation4. Best Practices and Benefits
Database ServicesGrid Control Setup
Database ServicesOverview of OEM Grid control Infrastructure Currently using 10gR5 OMSOMS is an active-active cluster on LinuxHardwareRepository database is on 10.2.0.4 with RACHundreds of targets were configured in OMSDedicated OMS for Prod databases and NonProd Databases.
Database Services1. Overview of OEM Grid control Infrastructure2. Current Data Scrambling issues3. Oracle Data Masking Implementation4. Best Practices and Benefits
Database ServicesClone-and-mask processData is sent offshore for application testingScrambling is done via custom scripts afterrefreshDevelopers who wrote the scripts had access toproduction data before scrambling
Database ServicesCurrent Data Scrambling issues Manual scripts run by developerNot 100% compliant with industryNo referential integrity is maintainedData issues
Database Services1. Overview of OEM Grid control Infrastructure2. Current Data Scrambling issues3. Oracle Data Masking Implementation4. Best Practices and Benefits
Database ServicesMasking Implementation – Privacy AttributesEmployeePersonal dataDependent BenefitsEmployment detailsNon-employee workforceRecruitment candidateTemporary workforceRelocation
Database ServicesData Masking Process – By NumbersTables with Sensitive Data: 98 to 120 columnsMasking Formats:– Employee related– Non-employee workforceDatabase size: ½ TeraByteCustom database privileges granted for maskingMasking job execution: 30-40 minutes
Database ServicesLife after Oracle Data MaskingSeparation of duties– HR analyst defines the mask definition– Operator submits the job to clone Production toTest and mask.– DBA monitors the executionEasy to use and works great for referentialintegrityAutomatic alerts when– insufficient space in SYSTEM or TEMP or data– not enough privileges to do maskingCustom data masking script now RETIRED.
Database Services1. Overview of OEM Grid control Infrastructure2. Current Data Scrambling issues3. Oracle Data Masking Implementation4. Best Practices and Benefits
Database ServicesBest Practices and Benefits Leverage format libraries to store datamasking definitionsAll the scrambled data is 100% compliantRe-run the failed jobStill have the old data in the table forverification.
Oracle Database SecurityDefense-in-Depth for Security and ultTotalRecallAccess ControlDatabaseVaultLabelSecurityEncryption and MaskingAdvancedSecuritySecureBackupDataMasking
Oracle Helps You Maximize Customer ValueDeploys SOAinfrastructure 92%fasterSaves 80% time andeffort for managingDatabasesAvoids online revenuelosses up to 25%Improves ITproductivity by 25%Drives asset utilizationup by 70%Cuts configurationmanagement effort by90%Saves 1.9 millionwith Oracle EnterpriseManagerSaves 170,000 peryear with OracleEnterprise ManagerReplaces manualtools with automation;saves time by 50%Reduces Databasetesting time by 90%Reduces provisioningeffort by 75%Saves weeks onapplication testingtimeCuts applicationtesting from weeks tohoursReduces criticalpatching time by 80%Delivers 24/7 uptimewith Oracle EnterpriseManager
Oracle Data Masking Implementation 4. Best Practices and Benefits. Database Services Best Practices and Benefits Leverage format libraries to store data masking definitions All the scrambled data is 100% compliant Re-run the failed job Still have the old data in the table for