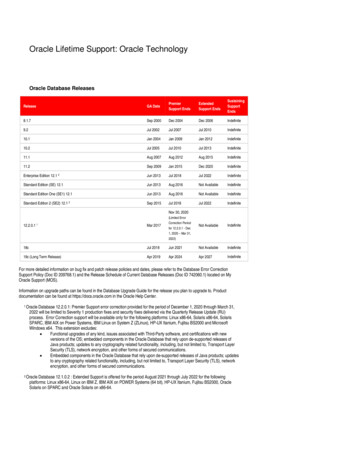
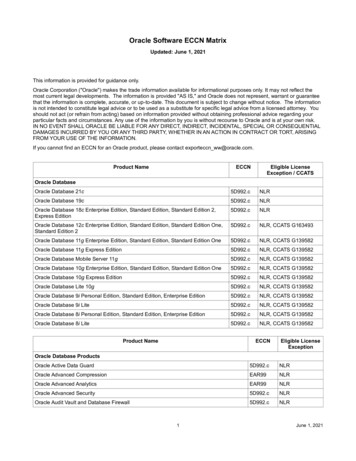
Transcription
1Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
The following is intended to outline our general product direction. It is intendedfor information purposes only, and may not be incorporated into any contract.It is not a commitment to deliver any material, code, or functionality, and shouldnot be relied upon in making purchasing decisions. The development, release,and timing of any features or functionality described for Oracle’s productsremains at the sole discretion of Oracle. Release timing for Oracle Database 12cis planned for Calendar Year 2013.2Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
Security Inside OutLatest Innovations in Oracle Database 12cJames OrrPrincipal Sales Consultant – Security SolutionsOracle
Over 1.1B Served4Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted%67Records breachedfrom servers%76Breached using weakor stolen credentials69%Discovered by anexternal party%97Preventable withbasic controls
Data Breaches are the Tip of the Iceberg Digital Security is the New Battle Ground“We are at the mercy of a new generation of spies whooperate remotely [that] have already shown theirability to penetrate our power plants, steal our latestsubmarine technology, rob our banks, and invade thePentagon’s secret communications systems.”Joel Brenner, former Inspector General of the National SecurityAgency and Chief of Counterintelligence for the Director of NationalIntelligence6Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
Targets Increasing as Attacks EvolveDBAs, OS Admins, Developers, Multiple Copies of the Data, etc.Anatomy of an Attack“You don’t bother to just simplyhack the organization and itsinfrastructure; you focus muchmore of your attention on hackingthe employees .”Uri RivnerCTO, RSA (Security Division of EMC)7Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
Why Are Databases So Vulnerable?80% of IT Security Programs Don’t Address Database SecurityForrester ResearchNetworkSecurity“Enterprises are taking on risksthat they may not even be awareAuthentication& User SecuritySIEMEmail SecurityEndpointSecurityof. Especially as more and moreattacks against databases exploitlegitimate opyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
Oracle Database Security SolutionsDefense-in-Depth for Maximum onActivity MonitoringPrivilege AnalysisRedaction and MaskingDatabase FirewallSensitive Data DiscoveryPrivileged User ControlsAuditing and ReportingConfiguration ManagementCopyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
Oracle Database Security SolutionsDefense-in-Depth for Maximum ionActivity MonitoringPrivilege AnalysisRedaction and MaskingDatabase FirewallSensitive Data DiscoveryPrivileged User ControlsAuditing and ReportingConfiguration ManagementCopyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
Encryption is the FoundationPreventive Control for Oracle DatabasesOracle Advanced SecurityDisk Transparent data encryptionBackups Prevents access to data at rest Requires no application changesExports Built-in two-tier key managementOff-SiteFacilities “Near Zero” overhead with hardware Integrations with Oracle technologies–11e.g. Exadata, Advanced Compression,ASM, Golden Gate, DataPump, etc.Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential RestrictedApplications
Redaction of Sensitive Data DisplayedPreventive Control for Oracle Database 12cOracle Advanced Security Real-time sensitive data redactionCredit Card 0032-0294-1827based on database session context Library of redaction policies and point-Redaction Policyand-click policy definition Consistent enforcement, policiesapplied to dataxxxx-xxxx-xxxx-43684451-2172-9841-4368 Transparent to applications, users, andoperational activitiesCall CenterApplication12Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential RestrictedBillingDepartment
Masking Data for Non-Production UsePreventive Control for Oracle DatabasesLAST NAMEOracle Data Masking Replace sensitive application 294360,000Production Referential integrity detected/preservedTest Extensible template library and formatsDev Application templates available Support for masking data in non-OracleNon-ProductiondatabasesLAST NAMEProduction13Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential HEIEDK252-34-134540,000
Privileged User ControlsPreventive Control for Oracle DatabasesOracle Database VaultSecurityDBA Limit DBA access to application dataProcurementApplicationDBA Multi-factor SQL command rulesHR Realms create protective zonesFinance Enforce enterprise data governance,least privilege, segregation of dutiesApplicationsselect * from finance.customers Out of the box application policiesDBA14Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
Label Based Access ControlPreventive Control for Oracle DatabasesOracle Label Security Virtual information partitioning for cloud,SensitiveSaaS, hosting environmentsTransactionsConfidential Classify users and data using labelsReport DataPublic Labels based on business drivers Automatically enforced row level accesscontrol, transparent to applications Labels can be factors in other policies15Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential RestrictedReportsConfidentialSensitive
Oracle Database Security SolutionsDefense-in-Depth for Maximum ionActivity MonitoringPrivilege AnalysisRedaction and MaskingDatabase FirewallSensitive Data DiscoveryPrivileged User ControlsAuditing and ReportingConfiguration ManagementCopyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
Database Activity Monitoring and FirewallDetective Control for Oracle and non-Oracle DatabasesOracle Audit Vault andDatabase Firewall Monitors network traffic, detect andblock unauthorized activity Highly accurate SQL grammar analysisUsersAllowLogAlertSubstituteBlockApps Can detect/stop SQL injection attacks Whitelist approach to enforce activity Blacklists for managing high risk activity Scalable secure software appliance17Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential st
Audit, Report, and Alert in Real-TimeDetective Control for Oracle and non-Oracle DatabasesOracle Audit Vault andDatabase FirewallAudit Data &Event Logs Centralized secure repository deliveredas secure, scalable software appliance Powerful alerting - thresholds, group-by Out-of-the box and custom reports Consolidated multi-source reporting Built-in fine grain segregation of dutiesOracleDatabaseFirewallSOC!AlertsOS abasesPoliciesCustomSecurityAnalyst18Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential RestrictedAuditor
Oracle Audit Vault and Database FirewallNew Solution for Oracle and Non-Oracle DatabasesDatabase ockFirewall EventsSOCAuditorSecurityAnalyst19Alerts!Audit DataBuilt-inReportsCustomReportsPoliciesCopyright 2013, Oracle and/or its affiliates. All rights reserved.Audit VaultOracle Confidential RestrictedOS, Directory, File System &Custom Audit Logs
Oracle Database Security SolutionsDefense-in-Depth for Maximum ionActivity MonitoringPrivilege AnalysisRedaction and MaskingDatabase FirewallSensitive Data DiscoveryPrivileged User ControlsAuditing and ReportingConfiguration ManagementCopyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
Discover Use of Privileges and RolesAdministrative Control for Oracle Database 12cOracle Database Vault Turn on privilege capture modeCreate Drop Modify DBA roleAPPADMIN role Report on actual privileges and rolesused in the database Helps revoke unnecessary privileges Enforce least privilege and reduce risks Increase security without disruption21Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential RestrictedPrivilege Analysis
Discover Sensitive Data and DatabasesAdministrative Control for Oracle Database 12cOracle Enterprise Manager 12c Scan Oracle for sensitive data Built-in, extensible data definitions Discover application data models Protect sensitive data appropriately:encrypt, redact, mask, audit 22Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
Configuration ManagementAdministrative Control for Oracle DatabasesOracle Database Lifecycle ManagementDiscover Discover and classify databases Scan for best practices, standards Detect unauthorized changes Automated remediationScan & Monitor Patching and provisioningPatch23Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
Oracle Database Security SolutionsDefense-in-Depth for Maximum ionActivity MonitoringPrivilege AnalysisRedaction and MaskingDatabase FirewallSensitive Data DiscoveryPrivileged User ControlsAuditing and ReportingConfiguration ManagementCopyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
Oracle Database SecurityCustomers Worldwide Rely on Oracle Database Security25Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
Oracle Database Security SolutionsSummarySecurity andComplianceSimple andFlexible26Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential RestrictedEnterpriseReadySpeed and Scale
Oracle Database Security Resourceswww.oracle.com/database/security Data Sheets Whitepapers Webcasts Case Studies Events News and more 27Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
Q&A28Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
29Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
The following is intended to outline our general product direction. It is intendedfor information purposes only, and may not be incorporated into any contract.It is not a commitment to deliver any material, code, or functionality, and shouldnot be relied upon in making purchasing decisions. The development, release,and timing of any features or functionality described for Oracle’s productsremains at the sole discretion of Oracle. Release timing for Oracle Database 12cis planned for Calendar Year 2013.30Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
31Copyright 2013, Oracle and/or its affiliates. All rights reserved.Oracle Confidential Restricted
Oracle Audit Vault and Database Firewall Audit, Report, and Alert in Real-Time Detective Control for Oracle and non-Oracle Databases Audit Data & Event Logs Policies Built-in Reports Alerts Custom Reports ! OS & Storage Directories Databases Oracle Database Firewall Custom Security Analyst Auditor SOC Centralized secure repository delivered