Transcription
Security OperationsMaturity ModelA practical guide to assessing and improving the maturity ofyour security operations
TABLE OF CONTENTSIntroduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3Understanding and measuring the capabilities of a security operations programme . . . . . . 4The LogRhythm Security Operations Maturity Model . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5Maturity model levels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6Conclusion . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10About LogRhythm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Security Operations Maturity ModelSecurity OperationsMaturity ModelIntroductionAs the threat landscape continues to evolve,your cybersecurity efforts must follow suit. Withyour security operations centre (SOC) at the coreof your offense against threats, you must ensurethat it can handle anything that comes its way.To be effective, you need to mature your SOC tostop threats early — before damage occurs.Whether your SOC is a virtual team of two tothree or a 24x7 operation, maturing yoursecurity operations capabilities will help youachieve a faster mean time to detect (MTTD)and mean time to respond (MTTR) tocyberthreats. This white paper exploresLogRhythm’s Security Operations MaturityModel (SOMM), which explains how to measurethe effectiveness of your security operations.Through the model, you can learn how to matureyour security operations capabilities, improvingyour resilience to cyberthreats.In this white paper, you will learn: How to understand and measure thecapabilities of your SOC Details about the LogRhythm SecurityOperations Maturity Model LogRhythm’s five levels of securityoperations maturity How to evaluate your organisation’smaturity levelIntroduction 3
Security Operations Maturity ModelUnderstanding and measuring thecapabilities of a security operationsprogrammeEnterprises should think of security operations as a critical business operation.Like any core business operation, organisations should want to measureoperational effectiveness to identify whether they are realising KPIs andSLAs and to help baseline and mature the function. That’s why understandingthe current status of your security posture is critical. It not only helps youunderstand your organisation’s security posture, but it enables you to improveyour cybersecurity efforts over the long term.Through constant monitoring and measuring mean time to detect (MTTD)and the mean time to respond (MTTR) — the primary metrics that indicate thematurity of a security operations program — you will be materially closer toyour goal to reduce your organisation’s cyber-incident risk.Enterprises shouldthink of security operationsas a critical business operation.Like any core business operation,organisations should want to measureoperational effectiveness to identifywhether they are realising KPIs andSLAs and to help baseline and maturethe function.4 Understanding and measuring the capabilities of a SOC
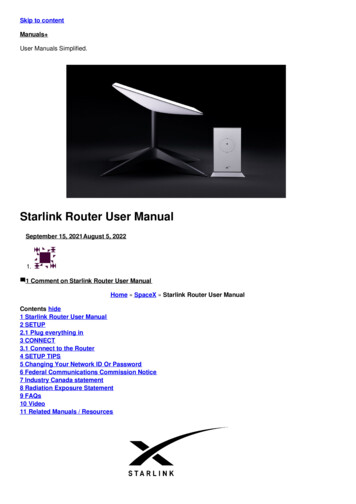
Security Operations Maturity ModelThe LogRhythm Security OperationsMaturity ModelLogRhythm developed the Security OperationsMaturity Model (SOMM) as a vendor-agnostictool to help you assess your current maturity andplan to improve it over time. As your securityoperations capabilities grow, you will realiseimproved effectiveness, resulting in faster MTTDand MTTR. Material reductions in MTTD/MTTRwill profoundly decrease the risk of experiencinghigh-impact cybersecurity incidents.LogRhythm’s model draws on a decade oforganisational experience serving enterpriseSOCs across the globe. It features five levels ofsecurity operations maturity. Each level buildson the prior, resulting in reduced MTTD/MTTRby strengthening capabilities through processand technology improvements. The followingfigure provides an illustrative example ofMTTD/MTTR reductions as maturity improves.Exposed to ThreatsResilient to ThreatsMTTD & MTTRMonthsWeeksDaysHoursMinutesLevel 0Level 1Level 2Level 3Level 4SECURITY OPERATIONS MATURITYFigure 1. Reduced time to detect and respond to cyberthreats is directly tied to security operations maturityScore your security maturitySee how the maturity of your security operations ranks.Take LogRhythm’s free self-assessment quiz to learnwhere your organisation’s capabilities turity-quiz/The LogRhythm SOMM 5
Security Operations Maturity ModelMaturity model levelsThe following table describes each SecurityOperations Maturity level in further detail,identifying the key technological and workflow/process capabilities that should be realised. Themanner in which you realise each capability willvary across your organisation. The importantthing is that you realise the intent of thecapability. For each level, LogRhythm has alsodescribed typical associated organisationalcharacteristics and risk characteristics. This isto provide additional context to support securityoperations maturity assessment and planning.You should use this model to evaluate yourorganisation’s current security operationsmaturity and develop a roadmap to achieve thelevel of maturity that is appropriate in light ofavailable resources, budget and risk tolerance. Minimal securityoperations capabilities No security operationscapabilities No process in place No formal incidentresponse process Compliance-driveinvestment Reactive processesLevel 06 Maturity model levelsLevel 1
Security Operations Maturity ModelReachingLevel 4 doesn’t meanyour organisation’s maturityhas peaked. Security maturityis an evolution and it requiresongoing monitoring to refineyour processes. Advanced anddocumented responseprocesses Basic securityoperations capabilities Reactive andmanual workflow Formal monitoring andresponse processes Automated threatqualification,investigation, andresponse processes Targeted automationof investigation andmitigation workflow Fully autonomousautomation — fromqualification to mitigation Consistent securityoperations practices Basic monitoring andresponse processesLevel 2Level 3Level 4Maturity model levels 7
SecurityMaturityoperationsSecurity OperationsModelcapabilities NoneOrganisationalcharacteristics Prevention-oriented(e.g., firewalls, antivirus,etc. in place) Isolated logging based ontechnology and functional silos; nocentral logging visibilityLEVEL0 Indicators of threat and compromiseexist, they are not visible andthreat hunting is not occurring tosurface themInitialRisk characteristics Non-compliance Unaware of insider threats Unaware of external threats Unaware of advanced persistentthreats (APTs) Potentially stolen IP (if of interest tonation-states or cybercriminals) No formal incident responseprocess; response due to individualheroic efforts Mandated log data and securityevent centralisationLEVEL1 Mandated compliance-centric serverforensics, such as file integritymonitoring and endpoint detectionresponse (EDR) Minimal compliance-mandatedmonitoring and responseMinimallycompliant Compliance-driven investment orhave identified a specific area ofenvironment requiring protection Compliance risks identified viareport review; process to manageviolations may or may not exist Improved visibility into threatstargeting the protected domain,but lacks people and process foreffective threat evaluation andprioritisation Significantly reduced compliance risk(depending on depth of audit) Unaware of most insider threats Unaware of most external threats Unaware of APTs Potentially stolen IP (if of interest tonation-states or cybercriminals) No formal incident responseprocess; response due to individualheroic efforts Targeted log data and securityevent centralisation Targeted server and endpointforensics Targeted environmental riskcharacterisationLEVEL2Securelycompliant Reactive and manual vulnerabilityintelligence workflow Reactive and manual threatintelligence workflow Basic machine analytics forcorrelation and alarm prioritisation Basic monitoring and responseprocesses established8 Maturity model levels Moving beyond minimal, ‘check box’compliance, seeking efficiencies andimproved assurance Have recognised organisationis effectively unaware of mostthreats; striving toward a materialimprovement that works to detectand respond to potential highimpact threats, focused on areasof highest risk Extremely resilient and highlyeffective compliance posture Good visibility to insider threats,with some blind spots Good visibility to external threats,with some blind spots Mostly unaware of APTs, but morelikely to detect indicators andevidence of APTs Have established formal processesand assigned responsibilities formonitoring and high-risk alarms More resilient to cybercriminals,except those leveraging APT-typeattacks or targeting blind spots Have established basic, yet formalprocess for incident response Highly vulnerable to nation-states
Security operations capabilities Holistic log data and security event centralisation Holistic server and endpoint forensics Targeted network forensics IOC-based threat intelligence integrated intoanalytics and workflow Holistic vulnerability integration with basiccorrelation and workflow integrationLEVEL3VigilantOrganisationalSecurity Operations Maturity ModelRisk characteristicscharacteristics Have recognised organisationis unaware of many high-impactthreats Have invested in theorganisational processes andheadcount to significantlyimprove ability to detect andrespond to all classes of threats Targeted machine analytics for anomalydetection (e.g., via behavioural analytics) Have invested in andestablished a formal securityoperations and incidentresponse centre (SOC) that isrunning effectively withtrained staff Formal and mature monitoring and responseprocess with standard playbooks for mostcommon threats Are effectively monitoringalarms and have progressedinto proactive threat hunting Functional physical or virtual SOC Are leveraging automationto improve the efficiencyand speed of threatinvestigation and incidentresponse processes Advanced machine analytics for IOC- andTTP-based scenario analytics for knownthreat detection Case management for threat investigationworkflow Targeted automation of investigation andmitigation workflow Extremely resilient and highlyeffective compliance posture Great visibility into, and quicklyresponding to insider threats Great visibility into, and quicklyresponding to external threats Good visibility to APTs, buthave blind spots Very resilient to cybercriminals,except those leveragingAPT-type attacks that targetblind spots Still vulnerable to nation-states,but much more likely to detectearly and respond quickly Basic MTTD/MTTR operational metrics Holistic log data and security event centralisation Holistic server and endpoint forensics Holistic network forensics Industry specific IOC- and TTP-based threatintelligence integrated into analytics andworkflows Holistic vulnerability intelligence with advancedcorrelation and automation workflow integration Advanced IOC- and TTP-based scenario machineanalytics for known threat detectionLEVEL4Resilient Advanced machine analytics for holistic anomalydetection (e.g., via multi-vector AI/ML-basedbehavioural analytics) Established, documented, and mature responseprocesses with standard playbooks for advancedthreats (e.g., APTs) Established, functional 24/7 physical or virtual SOC Cross-organisational case managementcollaboration and automation Extensive automation of investigation andmitigation workflow Fully autonomous automation, from qualificationto mitigation, for common threats Are a high-value target fornation-states, cyber terrorists,and organised crime Are continuously beingattacked across all potentialvectors: physical, logical, social A disruption of service orbreach is intolerable andrepresents organisationalfailure at the highest level Takes a proactive stancetoward threat management andsecurity in general Invests in best-in-class people,technology, and processes Extremely resilient and highlyefficient compliance posture Seeing and quickly respondingto all classes of threats Seeing evidence of APTs earlyin the Cyberattack Lifecycleand can strategically managetheir activities Extremely resilient to all classof cybercriminals Can withstand and defendagainst the most extremenation-state-level adversary Have 24/7 alarm monitoring withorganisational and operationalredundancies in place Have extensive proactivecapabilities for threat predictionand threat hunting Have automated threatqualification, investigation,and response processeswherever possible Advanced MTTD/MTTR operational metrics andhistorical trendingMaturity model levels 9
CONCLUSIONKnowing your organisation’s currentmaturity will help you grow and provethe value of your security programme.Threats will continue to target data and threatactors will be persistent and creative in theirefforts. To improve your security posture, youneed to understand your SOC’s strengths andweaknesses. Being able to monitor, measure,and communicate the state of your securitycapabilities is powerful. Measuring metricssuch as MTTD and MTTR plays a pivotal role inmaturing your SOC. Not only will you understandwhere growth opportunities exist, but you’ll bemore effective and will further reduce your riskto threats.LogRhythm’s Security Operations MaturityModel gives you a roadmap to achievesuccess. With this insight, you can presenthard evidence that you’re improving yourorganisation’s security stance and garneradditional support from your board. Whetheryou partner with LogRhythm or go a differentroute, this model will enable you to plan for thefuture and realise continuous improvement ofyour security operations maturity.Expert Tip:Determine your organisation’s current level of security operations maturity.Complete the self-assessment and learn how to build a use case10 Conclusionfor a stronger investment.
Security Operations Maturity ModelAbout LogRhythmLogRhythm is a world leader in NextGen SIEM,empowering thousands of enterprises on sixcontinents to successfully reduce cyber andoperational risk by rapidly detecting, respondingto and neutralising damaging cyberthreats. TheLogRhythm NextGen SIEM Platform combinesadvanced security analytics; user and entitybehaviour analytics (UEBA); network detectionand response (NDR); and security orchestration,automation, and response (SOAR) in a singleend-to-end solution. LogRhythm’s technologyserves as the foundation for the world’s mostmodern enterprise security operations centres(SOCs), helping customers measurably securetheir cloud, physical, and virtual infrastructuresfor both IT and OT environments. Built forsecurity professionals by security professionals,the LogRhythm NextGen SIEM Platform haswon countless customer and industry accolades.For more information, visit logrhythm.comAbout LogRhythm 11
44 (0)1628 918 330 // europe@logrhythm.comRegional HQ, Clarion House, Norreys Drive, Maidenhead, SL6 4FL, United Kingdom
The LogRhythm Security Operations Maturity Model LogRhythm's model draws on a decade of organisational experience serving enterprise SOCs across the globe. It features five levels of security operations maturity. Each level builds on the prior, resulting in reduced MTTD/MTTR by strengthening capabilities through process and technology .