Transcription
DoD EnterpriseDevSecOpsReference DesignCNCFKubernetesDoD EnterpriseDevSecOpsReference ybooksGuidebooks Executive SummaryGuiding PrinciplesGovernance Processes aybooksPlaybooksIndustry Recognized Best PracticesStandardized NomenclatureTechnology Tool & Activity MappingsSMART Performance Metrics Specific CNCF Kubernetes Tools & TechnologiesSpecific Architecture Requirements Additional Reference Designs DoD EnterpriseDevSecOpsReference DesignDoD EnterpriseDevSecOpsReference DesignDoD EnterpriseDevSecOpsReference DesignLow Code-No CodeLegacyModernization Future Reference Designs(Pending Interest, Time & Money)
DoD EnterpriseDevSecOpsReference DesignCNCFKubernetes Specific CNCF Kubernetes Tools & TechnologiesSpecific Architecture Requirements Additional Reference Designs(this document)DoD EnterpriseDevSecOpsReference ybooksGuidebooks Executive SummaryGuiding PrinciplesGovernance Processes aybooksPlaybooksIndustry Recognized Best PracticesStandardized NomenclatureTechnology Tool & Activity MappingsSMART Performance Metrics DoD EnterpriseDevSecOpsReference DesignDoD EnterpriseDevSecOpsReference DesignDoD EnterpriseDevSecOpsReference DesignLow Code-No CodeLegacyModernization Future Reference Designs(Pending Interest, Time & Money)
DoD EnterpriseDevSecOpsReference DesignCNCFKubernetes Specific CNCF Kubernetes Tools & TechnologiesSpecific Architecture Requirements Additional Reference Designs(this document)DoD EnterpriseDevSecOpsReference ybooksGuidebooks Executive SummaryGuiding PrinciplesGovernance Processes aybooksPlaybooksIndustry Recognized Best PracticesStandardized NomenclatureTechnology Tool & Activity MappingsSMART Performance Metrics DoD EnterpriseDevSecOpsReference DesignDoD EnterpriseDevSecOpsReference DesignDoD EnterpriseDevSecOpsReference DesignLow Code-No CodeLegacyModernization Future Reference Designs(Pending Interest, Time & Money)
DoD EnterpriseDevSecOpsReference DesignCNCFKubernetes DevSecOpsStrategyGuideIndustry Recognized Best PracticesStandardized NomenclatureTechnology Tool & Activity MappingsSMART Performance cSpecificSpecificPlaybooksPlaybooksGuidebooks Executive SummaryGuiding PrinciplesGovernance aybooksPlaybooksPlaybooksDoD EnterpriseDevSecOpsReference Design Specific CNCF Kubernetes Tools & TechnologiesSpecific Architecture Requirements Additional Reference Designs DoD EnterpriseDevSecOpsReference DesignDoD EnterpriseDevSecOpsReference DesignDoD EnterpriseDevSecOpsReference DesignLow Code-No CodeLegacyModernization Future Reference Designs(Pending Interest, Time & Money)(this document)
DoD EnterpriseDevSecOpsReference Design(this document)CNCFKubernetesDoD EnterpriseDevSecOpsReference ybooksGuidebooks Executive SummaryGuiding PrinciplesGovernance Processes aybooksPlaybooksIndustry Recognized Best PracticesStandardized NomenclatureTechnology Tool & Activity MappingsSMART Performance Metrics Specific CNCF Kubernetes Tools & TechnologiesSpecific Architecture Requirements Additional Reference Designs DoD EnterpriseDevSecOpsReference DesignDoD EnterpriseDevSecOpsReference DesignDoD EnterpriseDevSecOpsReference DesignLow Code-No CodeLegacyModernization Future Reference Designs(Pending Interest, Time & Money)
DoD EnterpriseDevSecOpsReference DesignCNCFKubernetes(this PlaybooksGuidebooks Executive SummaryGuiding PrinciplesGovernance Processes oksPlaybooksPlaybooksIndustry Recognized Best PracticesStandardized NomenclatureTechnology Tool & Activity MappingsSMART Performance MetricsDoD EnterpriseDevSecOpsReference DesignAWSManagedService Specific CNCF Kubernetes Tools & TechnologiesSpecific Architecture Requirements Utilization of AWS Managed ServicesSpecific Infrastructure as Code (IaC) Usage RequirementsDoD EnterpriseDevSecOpsReference DesignDoD EnterpriseDevSecOpsReference DesignDoD EnterpriseDevSecOpsReference DesignLow Code-No CodeLegacyModernization Future Reference Designs(Pending Interest, Time & Money)
DoD EnterpriseDevSecOpsReference DesignCNCFKubernetes(this PlaybooksGuidebooks Executive SummaryGuiding PrinciplesGovernance Processes oksPlaybooksPlaybooksIndustry Recognized Best PracticesStandardized NomenclatureTechnology Tool & Activity MappingsSMART Performance MetricsDoD EnterpriseDevSecOpsReference DesignMulti-ClusterCNCF K8s Specific CNCF Kubernetes Tools & TechnologiesSpecific Architecture Requirements Utilization of multiple Kubernetes clustersContinuous reconciliation across clustersDoD EnterpriseDevSecOpsReference DesignDoD EnterpriseDevSecOpsReference DesignDoD EnterpriseDevSecOpsReference DesignLow Code-No CodeLegacyModernization Future Reference Designs(Pending Interest, Time & Money)
Collection of DevSecOps CI/CD pipelines,where each pipeline is dedicated to unifyingpeople, automated processes, and relevanttools to create artifacts in support of a specificprogram(s) and/or mission set(s).An architectural approach that attempts toexploit the advantages of cloud architecture,on bare metal or in a Cloud agnostic manner; a consciousfocus on how the architecture is designed and deployed,over where it is deployed.SoftwareSupply ChainBOTH/ANDAn architectural approach that accepts CSP lock-in toexploit CSP managed services and technologiesto create cybersecurity hardened raw ingredients wherefurther value-add activities occur further down thesoftware supply chain.CSP ManagedServiceHARDWAREDoD DigitalModernization StrategyIAASSensorsCloudNativePAASIoTSAAS5GBig DataSoftwareFactoryTECH FORCEMULTIPLIERSAI/MLQuantumPROGRAM/MISSION
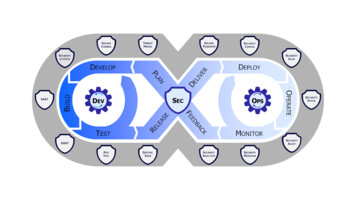
Continuous OperationsContinuous DeploymentContinuous DeliveryContinuous IntegrationContinuous BuildDevelopBuildTestRelease &DeliverDeployOperateCybersecurity Automation (Scanning, Testing, & Validating)MonitorLegendPlanControl GateRisk DeterminationFeedback LoopCompliance, Effectiveness, ThreatCon, Malicious Detection
Continuous BuildPlanDevelopBuildTestRelease &DeliverCyber Security Automation (Scanning, Testing, & Validating)MonitorDeployOperate
Continuous IntegrationPlanDevelopBuildTestRelease &DeliverCyber Security Automation (Scanning, Testing, & Validating)MonitorDeployOperate
Continuous DeliveryPlanDevelopBuildTestRelease &DeliverCyber Security Automation (Scanning, Testing, & Validating)MonitorDeployOperate
Continuous DeploymentPlanDevelopBuildTestRelease &DeliverCyber Security Automation (Scanning, Testing, & Validating)MonitorDeployOperate
Continuous OperationsPlanDevelopBuildTestRelease &DeliverCyber Security Automation (Scanning, Testing, & Validating)MonitorDeployOperate
PlanDevelopBuildTestRelease &DeliverCyber Security Automation (Scanning, Testing, & Validating)MonitorDeployOperate
ENTEST
STAGE:DEVELOPMENTCODE/SCRIPTSIDEIDEIDESTAGE:SYSTEM NVIRONMENTLOCALARTIFACTREPOPIPELINE nTESTENVIRONMENTINTEGRATION &PRE-PRODUCTIONENVIRONMENTRELEASEDARTIFACTREPO
CODE/SCRIPTSPIPELINE POIDEIDEIDEPIPELINE LINE 3TESTENVIRONMENTTESTENVIRONMENTS OFTWARE FACTORYKEY:PROCESS FLOWCONTROL GATEPIPELINE CONTROLINTEGRATION &PRE-PRODUCTIONENVIRONMENTRELEASEDARTIFACTREPO
ILIENCYREF MENTHOSTED INSOFTWAREFACTORYUSES1.*1ARTIFACTREPOSITORYREF DESIGNSPECIFIC1IS ANIS ANIS ANIS CYBERRESILIENCYREF DESIGNSPECIFIC
APPLICATIONSAPPLICATIONSAPP FRAMEWORKCONTINUOUS MONITORINGPLATFORM / SOFTWARE FACTORY Compliance, EffectivenessThreatCon, Malicious DetectLOGGING Log Aggregation & StorageLog Analysis & DisplayCI/CD PIPELINES IaC Defined SW FactoryDevSecOps ToolsENVIRONMENTSINFRASTRUCTURE Dev, Test, IntegrationHOSTING ENVIRONMENTS Cloud with DoD PA or ATOOther DoD Approved EnvREF DESIGNREF DESIGNSPECIFICINTERCONNECTREF DESIGNREF DESIGNSPECIFICINTERCONNECTREF DESIGNREF DESIGNSPECIFICINTERCONNECTREF DESIGNREF DESIGNSPECIFICINTERCONNECTREF DESIGNINTERCONNECTREF DESIGNSPECIFIC
APPLICATIONSDoD Enterprise DevSecOpsReference Design:CNCF Certified KubernetesAPPLICATIONSAPP FRAMEWORKCONTINUOUS MONITORING Compliance, EffectivenessThreatCon, Malicious DetectPLATFORM / SOFTWARE FACTORYREF DESIGNLOGGING INTERCONNECTLog Aggregation & StorageLog Analysis & DisplayREF DESIGNCI/CD PIPELINES REF DESIGN INFRASTRUCTURE Sidecar Container Security Stack (SCSS) Service Mesh MandateLocally Centralized Artifact Repository CNCF Certified Kubernetes (K8s) Cloud Native Access Point UtilizationREF DESIGNSPECIFICINTERCONNECTDev, Test, IntegrationREF DESIGNHOSTING ENVIRONMENTS REF DESIGNSPECIFICINTERCONNECTIaC Defined SW FactoryDevSecOps ToolsENVIRONMENTSREF DESIGNSPECIFICCloud with DoD PA or ATOOther DoD Approved EnvINTERCONNECTREF DESIGNSPECIFIC
VM11VM1nApplicationsApplicationsGuest OSGuest OSHypervisorx86 Server
CAC SOFTWAREDISA STIGANDCAC DEVELOPMENT PIPELINESTIG DEVELOPMENTPROCESSPRIORITIES CTREPO
Control Gate(s)Developmental Test(Dev, Test,Integration, & Pre-Production)Operational Test(Pre-Production, Production)GoalThe System Was Built RightThe Right System Was RightContinuous Monitoring
Sidecar Container Security Stack (SCSS)DoD Enterprise CloudSecurity Sidecar ContainerProgram Managed ServicesPolicy EnforcementArtifact RepositoryService Mesh ProxyService MeshLogging AgentLog Storage & RetrievalRuntime DefenseRuntime Behavior Analysis (AI)Security Sidecar Supportive DoDEnterprise ServicesDoD Centralized ArtifactRepository (DCAR)DoD Common Log & TelemetryAnalysis ServiceCVE Service/Host BasedSecurityVulnerability ManagementHostingEnvironmentLegendDoD CloudDoD Data Center(s)Bare Metal Server(s)DoD Provided Enterprise ServiceDoD Provided, Program Instantiated
Define CI/CD Processes & TasksSelect Tools Build the Software FactoryAutomate the Workflows Verify the Tool IntegrationsTest the Pipeline WorkflowsSoftware FactoryPhases Operate & Maintain theSoftware FactoryMonitor the Software FactoryTools & ProcessesGather Feedback for Improvement
lication N O D ionContainerApplicationEngine ApplicationLibrariesLibrariesNode Operating SystemLibrariesLibrariesNode Operating SystemContainer EngineNode Operating System
CONTAINER GROUP (POD)ApplicationContainerSidecarContainerShared StateStorageNetwork
Mission Program Application PlatformSubsystem 1ApplicationLoggingCompute & gregatedLogsContinuousImprovementMission ProgramChange ManagementLogAnalysisMission ProgramIncident stem nIncidentDetected?LogFilterYESIncidentDetected?DoD CommonSecurity Services(Logs/Telemetry Analysis)
ApplicationLifecycleYears or MonthsMonths or WeeksWeeks or oyment ctureServerData CenterCloudDataManagementSiloData WarehouseData LakeDataInterchangeProprietaryXMLJSONFirewall, SIEM, Zero Trust30-years ago15-years agoPresent DayCybersecurityPostureDays or HoursMulticloudFuture
To o l s(Based on DoD EnterpriseDevSecOps Hardened Containers)Wo r k f l o w sCM VCM CIDESoftware ublishArtifactsDev Environment Tests(Notional/Partial List)Run AutomatedTest SuiteBuildContainer ImageSecurityTest(s)ContainerSecurity ScanTestTool(s)Deploy toTest EnvDeploy toIntegration EnvRun AutomatedTest SuiteRelease & Deliver
TestEnvironmentTo o l sWorkflowsSoftware ScanUnitTestPublishArtifact(s)Deploy toTestDeploy toPre-ProdRelease &DeliverDeploy toProductionServicesDev Environment Tests(Notional/Partial stDeliverDevSecOps Services3rd PartyToolIntegrationCNCF KubernetesContainer ServicesDeployScaleLoggingMonitorOperations Services
ContinuousDelivery Use a source code repo for all production artifactsUse trunk-based development methodsShift left on securityImplement test automationImplement continuous integrationSupport test data managementImplement continuous deliveryAutomate the deployment processArchitecture Use loosely coupled architectureArchitect for empowered teamsCultural Adopt a Likert scale survey to measure cultural change progressEncourage and support continuous learning initiativesSupport and facilitate collaboration among and between teamsProvide resources and tools that make work meaningfulSupport or embody transformational leadershipProduct& Process Gather and implement customer feedbackMake the flow of work visible through the value streamWork in small batchesFoster and enable team experimentationmenting Have a lightweight change approval process
Option ACOTSContainer OrchestrationOption BDoD AuthorizedContainer ServiceApplicationsSoftware FactoryApplicationsSoftware Factory(DoD Enterprise DevSecOps Containers)(DoD Enterprise DevSecOps Containers)Container OrchestrationContainer Service (DoD PA)Hosting EnvironmentHosting Environment(OCI Compliant Containers,CNCF Certified Kubernetes)(DoD Cloud, Data Center, or Bare Metal)(OCI Compliant Containers,CNCF Certified Kubernetes)(DoD Cloud)Mission Program Responsibility & Managed ComponentsHosting Environment Provider Responsibility & Managed Components
Shared Responsibility ModelApplicationsSoftware Factory(DoD Enterprise DevSecOps Containers)Container Orchestration(OCI Compliant Containers,CNCF Certified Kubernetes)Hosting Environment(DoD Cloud, Data Center, or Bare Metal)Mission Program Responsibility & Managed ComponentsHosting Environment Provider Responsibility & Managed Components
WARFIGHTER A QUANTIFIED DEGREE OFCYBER SURVIVABILITYSecurityQualityProblemsSECURE SOFTWARE DETECTS AND RESISTSCYBERATTACKS, OFFERING THEResilientSoftwareStabilityQualityQUALITY SOFTWARE MAXIMIZES USERREQUESTED FEATURE SETS ANDMINIMIZES FUNCTIONAL DEFECTSSTABLE SOFTWARE PERFORMS WELLWITHOUT BREAKING OR CRASHING, &DYNAMICALLY SCALES TO MATCHDEMAND
SetDevSecOpsDocumentUpdate 22.0Strategy Guide2.12.0Fundamentals2.12.0Tools & Activities Guidebook2.12.0Reference Design: CNCF K8s2.1--Reference Design: AWS CSP w/IaC1.02.0Playbook - DevSecOps2.1
Industry Contribution“DoD should modify its processes to mimic industry’sbest practices rather than try to contract for andmaintain customized software.”(Defense Innovation Board, Software is Never Done, May 2019)
To o l s(Based on DoD Cloud IaC Baselines &DevSecOps Hardened Containers)Wo r k f l o w sCM VCM CIDESoftware ublishArtifactsDev Environment Tests(Notional/Partial List)Run AutomatedTest SuiteBuildContainer ImageSecurityTest(s)ContainerSecurity ScanTestTool(s)Deploy toTest EnvDeploy toIntegration EnvRun AutomatedTest SuiteRelease & Deliver
AWS Managed ServiceContainer OrchestrationApplicationsSoftware Factory(DoD Enterprise DevSecOps Containers)AWS EKS Control Plane(CNCF Certified Kubernetes)Amazon Web ServicesMission Program Responsibility & Managed ComponentsHosting Environment Provider Responsibility & IaC Provisioned Managed Components
APPLICATIONSDoD Enterprise DevSecOpsReference Design:AWS Managed ServicesAPPLICATIONSAPP FRAMEWORKCONTINUOUS MONITORING Compliance, EffectivenessThreatCon, Malicious DetectPLATFORM / SOFTWARE FACTORYREF DESIGNLOGGING INTERCONNECTLog Aggregation & StorageLog Analysis & DisplayREF DESIGNCI/CD PIPELINES REF DESIGN INFRASTRUCTUREREF DESIGNSPECIFICINTERCONNECT AWS EventBridgeAWS CloudEventsAWS Security Hub AWS App MeshAWS Elastic Container Registry (ECR) AWSAWSAWSAWS AWS CloudFormationCloud Native Access Point, and/orBCAP Connected VDSSElastic Kubernetes Service (EKS)CodePipelineCodeBuildCodeCommitDev, Test, IntegrationREF DESIGNHOSTING ENVIRONMENTS REF DESIGNSPECIFICINTERCONNECTIaC Defined SW FactoryDevSecOps ToolsENVIRONMENTSREF DESIGNSPECIFICCloud with DoD PA or ATOOther DoD Approved EnvINTERCONNECTREF DESIGNSPECIFIC
COCOM AppUserService Specific AppJoint App
ntProductionEnvironmentWorkflowsTo o l yScanUnitTestPublishArtifact(s)Deploy toTestDeploy toPre-ProdRelease &DeliverDeploy toProductionDev Environment Tests(Notional/Partial eControlTestDeliver3rd PartyToolIntegrationCNCF KubernetesDeployScaleLoggingMonitorCSPw/PACloud DevSecOps ServicesCloud Container ServicesCloud Operations Services
APPLICATIONSDoD Enterprise DevSecOpsReference Design:Multi-Cluster CNCF KubernetesAPPLICATIONSAPP FRAMEWORKCONTINUOUS MONITORING Compliance, EffectivenessThreatCon, Malicious DetectPLATFORM / SOFTWARE FACTORYREF DESIGNLOGGING INTERCONNECTLog Aggregation & StorageLog Analysis & DisplayREF DESIGNCI/CD PIPELINES REF DESIGN INFRASTRUCTUREImmutable Infrastructure via IaC Continuous Reconciliation Mandate Multi-Cluster CNCF Kubernetes Secure Supply Chain Provenance MandateREF DESIGNSPECIFICINTERCONNECTDev, Test, IntegrationREF DESIGNHOSTING ENVIRONMENTS REF DESIGNSPECIFICINTERCONNECTIaC Defined SW FactoryDevSecOps ToolsENVIRONMENTSREF DESIGNSPECIFICCloud with DoD PA or ATOOther DoD Approved EnvINTERCONNECTREF DESIGNSPECIFIC
CODE REPOSITORY(source of truth)ManifestsReconciliationLoopControlPlaneDay 2ReconciliationK8sClustersCluster Creation& Enforcement
Supply Chain ProcessGLOBAL CONTROL PLANEActiveConnectionsWorkloadK8s ClusterServicesREGIONAL MANAGEMENT CLUSTERActiveConnectionsWorkloadK8s ClusterServices
Pathway to DevSecOps Reference DesignEvaluation eInterconnectsApprovedRef DesignLessonsLearnedExecutePilotSW Mod SSGBriefing
Pathway to DevSecOps Reference DesignEvaluation eInterconnectsApprovedRef DesignLessonsLearnedExecutePilotSW Mod SSGBriefing
Guiding Principles Governance Processes Topic Specific Playbooks. Topic Specific Playbooks. Topic Specific Playbooks. Topic Specific Playbooks. Topic Specific Playbooks. Topic Specific Guidebooks Industry Recognized Best Practices Standardized Nomenclature Technology Tool & Activity Mappings SMART Performance Metrics DoD .











