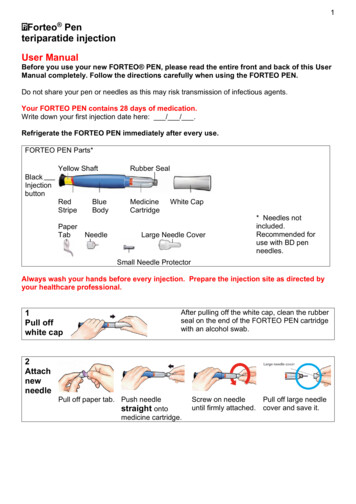
Transcription
Pen Testing ICS and Other HighlyRestricted EnvironmentsDon C. Weber - @cutawayPrincipal Consultant, Founder 2019 Cutaway Security, LLC. All Rights Reserved.Presented at SANS Pen Test HackFest Summit in Bethesda, MD on Nov. 19, 2019
Cutaway Security, LLC Don C. Weber - Jack of All Trades Security ManagementPenetration TestingSecurity AssessmentsSecurity ResearcherInstructor / PresenterIncident Response11/20/19 2018 Cutaway Security, LLC. All Rights Reserved.2
You don't knowInfosec about ICS 2019 Cutaway Security, LLC. All Rights Reserved.
Things to get over Clear Text Protocols Insecure Applications Vulnerable Firmware Brittle Services Legacy Software and Equipment 2019 Cutaway Security, LLC. All Rights Reserved.
Worst Case Scenario 2019 Cutaway Security, LLC. All Rights Reserved.
What are ICS Concerns? Safety to personnel, environment, andprocess. Sustained operations, availability andintegrity, of the process. Regulation, due to safety,environmental hazard, or publicimpact.Image Source: ploads/wp-content/uploads/2015/08/Cannisters After.jpg 2019 Cutaway Security, LLC. All Rights Reserved.
It's a network, why can't wepentest it? 2019 Cutaway Security, LLC. All Rights Reserved.
ICS Pen Test RoadblocksInfoSec Consultant: "We are hereto understand how the PLC acceptsuser input and determine."OT PLC Programmer: "Why don'tyou just go away and let us do ourjobs."InfoSec Consultant: " then we will do somesimple scanning to discover services "IT Security Director: "No. You can't scan."InfoSec Consultant: "Can I run an ARP scan todiscover ?"IT Security Director: "No. No scanning at all."InfoSec Consultant: "I'm going to run a PowerShellscript that only check system settings and writesit to a file."OT Lead: "But that means you are making changesto the system. "InfoSec Consultant: "No changes, just creatingone file with system configuration information."OT Lead: "You are changing the system." 2019 Cutaway Security, LLC. All Rights Reserved.
How did this happen?Situation 0: Nessus scan, in 2016, of an OTsubnet took over a week to fix the process.Situation 1: Changes to systems can triggerrigorous and expensive testing. They can alsovoid maintenance agreements.Situation 2: IT security team and OT haddifferent operational goals.Image Source: gif 2019 Cutaway Security, LLC. All Rights Reserved.
How do we overcome thismentality? 2019 Cutaway Security, LLC. All Rights Reserved.
White-Glove Treatment Make management comfortable Make process engineers and operators comfortable. Make IT personnel comfortable.Image Source: American Heritage Dictionary of the English Language, Fifth Edition. Copyright 2016 by Houghton MifflinHarcourt Publishing Company. Published by Houghton Mifflin Harcourt Publishing Company. All rights reserved. 2019 Cutaway Security, LLC. All Rights Reserved.
#1 Recommendation from ICS IT/ OT TeamsICS Security Teamneeds to spend timewith the OT Team tounderstand thepeople, processes,and operations.Image Source: Boyd Animation https://boydanimation.com/ 2019 Cutaway Security, LLC. All Rights Reserved.
How do we test? 2019 Cutaway Security, LLC. All Rights Reserved.
Purdue Level 4 - Plant's Business NetworkEnforcement between ICS DMZ and Business Networks (Business pulls from or pushes to iDMZ)ICS DMZ - ICS to BusnssICS DMZ - Busnss to ICSICS DMZ - Cloud AccessICS DMZ - Remote AccessEnforcement between Control Networks and ICS DMZ (Control pulls from or pushes to iDMZ)Purdue Level 3 Master Servers,Jump HostsWorkstationsTesting/StagingCyber SecurityPlantHistorian, and(per vendor or(per group/role) (per ment between Cell / Lines and Plant Supervisory (ACL on router / layer-3 switch or Firewall)Airgap / EnforcementSafety Systems0 - Field DevicesAirgap / EnforcementSafety Systems1 - Local Control0 - Field DevicesAirgap / EnforcementSafety SystemsImage Source: ControlThings.io Accessing and Exploiting Control Systems 2019 Cutaway Security, LLC. All Rights Reserved.2 - Local SupervisoryCell / Line / Process D0 - Field Devices1 - Local Control2 - Local SupervisoryCell / Line / Process C1 - Local Control2 - Local SupervisoryCell / Line / Process B2 - Local SupervisoryCell / Line / Process AControl NetworkPlant NetworksExpected Architecture – ICS410 Reference Model1 - Local Control0 - Field DevicesAirgap / EnforcementSafety Systems
IT / OT Security Effort Prioritization Separate policies for IT and OT environments Segmentation and Isolation Access Control Logging and Monitoring Asset Inventory Incident Response and Recovery 2019 Cutaway Security, LLC. All Rights Reserved.
Process Familiarization Architecture Review Site Walk Thru Physical Security Engineer / Operator Actions in Process Interviews ManagersEngineers / Operators / ProgrammersIT TeamIT Security Threat Modeling Configuration Analysis Source Code AnalysisImage Source: https://www.controlthings.io/ - Accessing and Exploiting Control Systems 2019 Cutaway Security, LLC. All Rights Reserved.
Passive Information Gathering Monitor network communications Hardware: tap, switch with span port Software: tcpdump, dumpcap,wireshark, zeek Scripts and Offline Analysis Configuration Hardening AssessmentPowerShell Script (CHAPS) https://github.com/cutawaysecurity/chaps Windows Exploit Suggester - NextGeneration https://github.com/bitsadmin/wesng 2019 Cutaway Security, LLC. All Rights Reserved.
Active Testing Understand the consequences of active testing couldimpact safety. Know how to rate limit at both the network andapplication levels. Select individual targets: hosts and services. Know your tool configurations and double check witha partner. Remember assessment goals and test to them. 2019 Cutaway Security, LLC. All Rights Reserved.Image Source: r/
In Conclusion 2019 Cutaway Security, LLC. All Rights Reserved.
Controlled Migration to Mature ICS Environment 2019 Cutaway Security, LLC. All Rights Reserved.
ICS Pen Testing is a Different Kind of Sexy Slow your roll and check your attitude. OT environment cannot live up to IT policies andbest practices. Get to know the OT teams and the processes. Start testing passively and escalate safely. Help identify issues and help the defenders protectthe process. 2019 Cutaway Security, LLC. All Rights Reserved.
Don C. Weber - @cutawayCutaway Security, LLCPrincipal Consultant, com/cutaway-security 2019 Cutaway Security, LLC. All Rights Reserved.
InfoSec Consultant: "I'm going to run a PowerShell script that only check system settings and writes it to a file." OT Lead: "But that means you are making changes to the system. "InfoSec Consultant: "No changes, just creating one file with system configuration information." OT Lead: "You are changing the system." InfoSec Consultant: "We are here