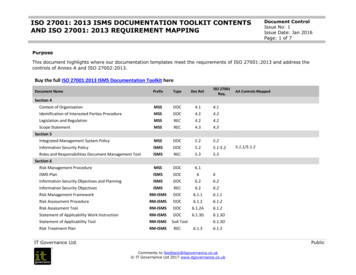
Transcription
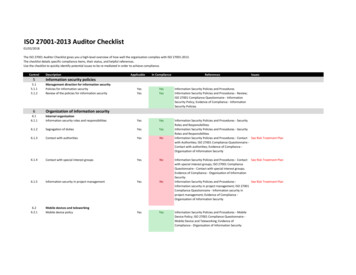
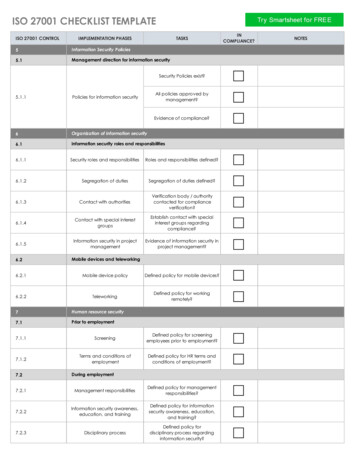
ISO 27001 CHECKLIST TEMPLATEISO 27001 CONTROLIMPLEMENTATION PHASESTASKS5Information Security Policies5.1Management direction for information securitySecurity Policies exist?5.1.1All policies approved bymanagement?Policies for information securityEvidence of compliance?6Organization of information security6.1information security roles and responsibilities6.1.1Security roles and responsibilitiesRoles and responsibilities defined?6.1.2Segregation of dutiesSegregation of duties defined?6.1.3Contact with authoritiesVerification body / authoritycontacted for complianceverification?6.1.4Contact with special interestgroupsEstablish contact with specialinterest groups regardingcompliance?6.1.5Information security in projectmanagementEvidence of information security inproject management?6.2Mobile devices and teleworking6.2.1Mobile device policyDefined policy for mobile devices?6.2.2TeleworkingDefined policy for workingremotely?7Human resource security7.1Prior to employment7.1.1ScreeningDefined policy for screeningemployees prior to employment?7.1.2Terms and conditions ofemploymentDefined policy for HR terms andconditions of employment?7.2During employment7.2.1Management responsibilitiesDefined policy for managementresponsibilities?7.2.2Information security awareness,education, and trainingDefined policy for informationsecurity awareness, education,and training?7.2.3Disciplinary processDefined policy fordisciplinary process regardinginformation security?INCOMPLIANCE?NOTES
7.37.3.1Termination and change of employmentTermination or change ofemployment responsibilities8Asset management8.1Responsibilities for assetsDefined policy for HR terminationor change-of-employment policyregarding information security?8.1.1Inventory of assetsComplete inventory list of assets?8.1.2Ownership of assetsComplete ownership list of assets8.1.3Acceptable use of assetsDefined "acceptable use" of assetspolicy8.1.4Return of assetsDefined return of assets policy?8.2Information classification8.2.1Classification of informationDefined policy for classificationof information?8.2.2Labeling of informationDefined policy for labelinginformation?8.2.3Handling of assetsDefined policy for handlingof assets?8.3Media handling8.3.1Management of removablemediaDefined policy for managementof removable media?8.3.2Disposal of mediaDefined policy for disposalof media?8.3.3.Physical media transferDefined policy for physicalmedia transfer?9Access control9.1Responsibilities for assets9.1.1Access policy controlDefined policy for accesscontrol policy?9.1.2Access to networks andnetwork servicesDefined policy for access tonetworks and network services?9.2Responsibilities for assets9.2.1User registration and deregistrationDefined policy for user assetregistration and de-registration?9.2.2User access provisioningDefined policy for user accessprovisioning?9.2.3Management of privilegedaccess rightsDefined policy for managementof privileged access rights?
9.2.4Management of secretauthentication information of usersDefined policy for managementof secret authenticationinformation of users?9.2.5Review of user access rightsDefined policy for review of useraccess rights?9.2.6Removal or adjustmentof access rightsDefined policy for removal oradjustment of access rights?9.39.3.19.4User responsibilitiesUse of secret authenticationinformationDefined policy for use of secretauthentication information?System and application access control9.4.1Information access restrictionsDefined policy for informationaccess restrictions?9.4.2Secure log-on proceduresDefined policy for secure log-inprocedures?9.4.3Password management systemDefined policy for passwordmanagement systems?9.4.4Use of privileged utility programsDefined policy for use ofprivileged utility programs?9.4.5Access control to program sourcecodeDefined policy for access controlto program source code?10Cryptography10.1Cryptographic controls10.1.1Policy on the use ofcryptographic controlsDefined policy for use ofcryptographic controls?10.1.2Key managementDefined policy for keymanagement?11Physical and environmental security11.1Secure areas11.1.1Physical security perimeterDefined policy for physical securityperimeter?11.1.2Physical entry controlsDefined policy for physical entrycontrols?11.1.3Securing offices, rooms andfacilitiesDefined policy for securing offices,rooms and facilities?11.1.4Protection against external andenvironmental threatsDefined policy for protectionagainst external andenvironmental threats?11.1.5Working in secure areasDefined policy for working insecure areas?11.1.6Delivery and loading areasDefined policy for delivery andloading areas?
11.2Equipment11.2.1Equipment siting and protectionDefined policy for equipment sitingand protection?11.2.2Supporting utilitiesDefined policy for supportingutilities?11.2.3Cabling securityDefined policy for cablingsecurity?11.2.4Equipment maintenanceDefined policy for equipmentmaintenance?11.2.5Removal of assetsDefined policy for removal ofassets?11.2.6Security of equipment and assetsoff-premisesDefined policy for security ofequipment and assets offpremises?11.2.7Secure disposal or re-use ofequipmentSecure disposal or re-use ofequipment?11.2.8Unattended user equipmentDefined policy for unattended userequipment?11.2.9Clear desk and clear screen policyDefined policy for clear desk andclear screen policy?12Operations security12.1Operational procedures and responsibilities12.1.1Documented operatingproceduresDefined policy for documentedoperating procedures?12.1.2Change managementDefined policy for changemanagement?12.1.3Capacity managementDefined policy for capacitymanagement?12.1.4Separation of development,testing and operationalenvironmentsDefined policy for separation ofdevelopment, testing andoperational environments?12.212.2.112.3Protection from malwareControls against malwareDefined policy for controls againstmalware?System Backup12.3.1BackupDefined policy for backing upsystems?12.3.2Information BackupDefined policy for informationbackup?12.412.4.1Logging and MonitoringEvent loggingDefined policy for event logging?
12.4.2Protection of log informationDefined policy for protection oflog information?12.4.3Administrator and operator logDefined policy for administratorand operator log?12.4.4Clock synchronizationDefined policy for clocksynchronization?12.512.5.112.6Control of operational softwareInstallation of software onoperational systemsDefined policy for installation ofsoftware on operational systems?Technical vulnerability management12.6.1Management of technicalvulnerabilitiesDefined policy for management oftechnical vulnerabilities?12.6.2Restriction on software installationDefined policy for restriction onsoftware installation?12.712.7.1Information systems audit considerationsInformation system audit control13Communications security13.1Network security managementDefined policy for informationsystem audit control?13.1.1Network controlsDefined policy for networkcontrols?13.1.2Security of network servicesDefined policy for security ofnetwork services?13.1.3Segregation in networksDefined policy for segregation innetworks?13.2Information transfer13.2.1Information transfer policies andproceduresDefined policy for informationtransfer policies and procedures?13.2.2Agreements on informationtransferDefined policy for agreements oninformation transfer?13.2.3Electronic messagingDefined policy for electronicmessaging?13.2.4Confidentiality or non-disclosureagreementsDefined policy for confidentialityor non-disclosure agreements?13.2.5System acquisition, developmentand maintenanceDefined policy for systemacquisition, development andmaintenance?14System acquisition, development and maintenance14.1Security requirements of information systems14.1.1Information security requirementsanalysis and specificationDefined policy for informationsecurity requirements analysis andspecification?
14.1.2Securing application services onpublic networksDefined policy for securingapplication services on publicnetworks?14.1.3Protecting application servicetransactionsDefined policy for protectingapplication service transactions?14.2Security in development and support processes14.2.11515.1.11616.1.1In-house developmentDefined policy for in-housedevelopment?Suppliers relationshipsSuppliers relationshipsDefined policy for supplierrelationships?Information security incident managementInformation security managementDefined policy for informationsecurity management?17Information security aspects of business continuity management17.1Information security continuity17.1.117.217.2.1Information security continuityDefined policy for informationsecurity continuity?RedundanciesRedundanciesDefined policy for redundancies?18Compliance18.1Compliance with legal and contractual requirements18.1.1Identification of applicablelegislation and contractualrequirementDefined policy for identification ofapplicable legislation andcontractual requirement?18.1.2Intellectual property rightsDefined policy for intellectualproperty rights?18.1.3Protection of recordsDefined policy for protection ofrecords?18.1.4Privacy and protection ofpersonally identifiable informationDefined policy for privacy andprotection of personallyidentifiable information?18.1.5Regulation of cryptographiccontrolDefined policy for regulation ofcryptographic control?18.1Independent review of information security18.1.1Compliance with security policiesand standardsDefined policy for compliancewith security policies andstandards?18.1.2Technical compliance reviewDefined policy for technicalcompliance review?
DISCLAIMERAny articles, templates, or information provided by Smartsheet on the website are forreference only. While we strive to keep the information up to date and correct, we make norepresentations or warranties of any kind, express or implied, about the completeness,accuracy, reliability, suitability, or availability with respect to the website or the information,articles, templates, or related graphics contained on the website. Any reliance you place onsuch information is therefore strictly at your own risk.This template is provided as a sample only. This template is in no way meant as legal orcompliance advice. Users of the template must determine what information is necessaryand needed to accomplish their objectives.
ISO 27001 CHECKLIST TEMPLATE ISO 27001 CONTROL IMPLEMENTATION PHASES TASKS IN COMPLIANCE? NOTES 5 5.1 Security Policies exist? 5.1.1 Policies for information security All policies approved by management? Evidence of compliance? 6 6.1 6.1.1 Security roles and responsibilities Roles and responsibilities defined?