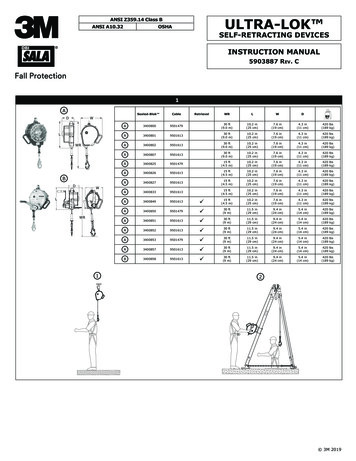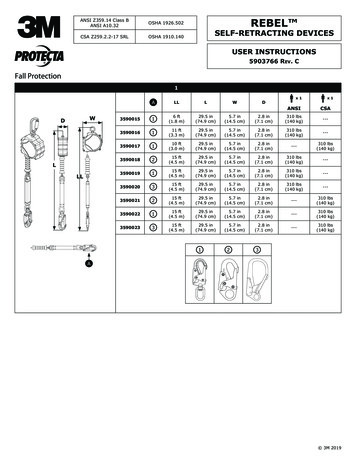
Transcription
DATASHEETTHUNDER SSLiREAL-TIME VISIBILITY INTO ENCRYPTED TRAFFICThe most comprehensive decryption solution, A10 Thunder PLATFORMSSLi (SSL Insight) decrypts traffic across all ports, enablingthird-party security devices to analyze all enterprise trafficwithout compromising performance.THUNDER SSLiPhysical ApplianceELIMINATE THEBLIND SPOTThunder SSLi eliminates the blind spotThunder SSLi boosts the performance of theintroduced by SSL encryption by offloadingsecurity infrastructure by decrypting trafficCPU-intensive SSL decryption and encryptionand forwarding it to one or more third-partyfunctions from third-party security devices,security devices, such as a firewall for deepwhile ensuring compliance with privacypacket inspection (DPI).standards.Thunder SSLi re-encrypts traffic andWhile dedicated security devices provideforwards it to the intended destination.in-depth inspection and analysis of networkResponse traffic is also inspected in thetraffic, they are not designed to decrypt andsame way.TALKWITH A10encrypt traffic at high speeds. In fact, manysecurity products do not have the ability toWEBdecrypt traffic at all.a10networks.com/SSLiCO NTACT USa10networks.com/contact1
BENEFITSGAIN FULLVISIBILITYSECUREKEY STORAGEINTO THE BLIND SPOTStoring encryption keys on manyThunder SSLi decrypts traffic across allappliances in the network can introduceports and multiple protocols, eliminatingserious vulnerabilities. Threat actors canthe encryption blind spot and enablingacquire keys from vulnerable points andthe security infrastructure to inspectuse them for encrypted attacks or datapreviously invisible traffic, detect hiddenextraction.threats and defend against them.With FIPS 140-2 Level 3-validated internaland external Hardware Security ModuleDECRYPT TRAFFICFOR ALL SECURITY DEVICES(HSM) support, Thunder SSLi reducesdecryption points so encryption keys arestored securely.To truly secure an enterprise network,from both internal and external threats,organizations require the help of a varietyof security devices.Thunder SSLi works with the majorsecurity vendors, which may be deployedin a number of ways, ensuring thatthe whole network is secure againstVALIDATECERTIFICATE STATUSAttackers can use invalid certificatesto infiltrate networks. If these attacksare not blocked, users can be at risk ofmultiple attacks.encrypted threats. Thunder SSLiThunder SSLi helps the system confirminteroperates with:the validity of certificates it receives Firewalls Secure Web Gateways (SWG) Intrusion Prevention Systems (IPS) Unified Threat Management (UTM)from the server by supporting CertificateRevocation Lists (CRL) and OnlineCertificate Status Protocol (OCSP). Theseprotocols help verify the origin certificateis valid.platforms Data Loss Prevention (DLP)products Threat Prevention platforms Network Forensics and WebMonitoring tools2
ENSUREREDUCECOMPLIANCE AND PRIVACYOPERATIONAL COSTSThunder SSLi allows for selectiveThunder SSLi offers a centralized pointdecryption, making sure thatto decrypt enterprise traffic, forwardingorganizations can keep up with industry,it to many inline and non-inline securitygovernment and other compliance anddevices. This eliminates the decryptionprivacy standards. For example, HIPAAoverhead of each security device,compliance may forbid the decryptionimproving performance while maintainingof private and sensitive healthcareproper security diligence. It alsoinformation.eliminates the need to purchase biggersecurity devices just to support resourceexhausting decryption and encryptionfunctions.SIMPLIFY OPERATIONSAND MANAGEMENTA wizard-based configuration, deployment and management tool, AppCentric Templates make Thunder SSLi theeasiest-to-use decryption solution in the industry. With informative dashboards, organizations can track theirnetwork with ease. Thunder SSLi also includes an industry-standard CLI, a web user interface and a RESTful API(aXAPI ), which integrates with third-party or custom management consoles.Good120 Kbps761947223System StatusSSL TrafficSSL CPSSSL SessionsCerts in Cache LegendSSL Inspection StatusSSL Traffic Legend 10 sSSL Traffic89 %11%DecryptedConn Rate0%BypassedErrors LegendKey Exchange MethodsDecrypted 60Access to Suspicious WebsitesECDHEDHE15:36:30Top Bypassed 30Top Accessed fofail-safeothersAppCentricTemplates helpusers manage theirencrypted trafficusing a dashboardto visualize SSLtraffic, decryptionand encryption,bypassing, trafficmanagement usingcategorization,and more.3
REFERENCE ARCHITECTURESDecrypt ZoneSecurity Device26 3147Client5A10 Thunder SSLiInternetRemote Server1Encrypted traffic from the client is interceptedby Thunder SSLi and decrypted.5The server processes the request and sends anencrypted response to Thunder SSLi.2Thunder SSLi sends the decrypted traffic to asecurity device, which inspects it in clear-text.63The security device, after inspection, sends thetraffic back to Thunder SSLi, which interceptsand re-encrypts it.Thunder SSLi decrypts the response traffic andforwards it to the same security device forinspection.7Thunder SSLi receives the traffic from thesecurity device, re-encrypts it and sends it to theclient.4Thunder SSLi sends the re-encrypted traffic tothe server.TRAFFIC FLOW THROUGHTHE DECRYPT ZONEThunder SSLi provides visibility via a logicaldecrypt zone where third-party security devicesinspect traffic for threats. Thunder SSLican be deployed in a one- or two-applianceconfiguration.Decrypt ZoneClientNon-InlineSecurity DeviceInlineSecurity DeviceIDS/ATPIPS/NGFWICAPDeviceDLP/AVA10 Thunder SSLiTHUNDER840 SSLiMULTIPLE DEPLOYMENT &DECRYPTION OPTIONSInternetThunder SSLi may be deployed inline, on theenterprise perimeter, and can decrypt traffic fora variety of security products simultaneously,including inline, non-inline (passive/TAP) andICAP-enabled devices.THUNDER500 Mbps5840S SSLi20 GbpsTHUNDERSSLiSMALLMEDIUMLARGEThunder SSLi provides decryption solutions that cater to the needs of small, medium and large enterprises.4
DECRYPTED TRAFFIC SOLUTIONSFOR ANY SECURITY DEVICEThunder SSLi decrypts traffic for security devices from the top vendors.FIREWALLS Cisco ASA with FirePOWER Palo Alto Networks NextGeneration Firewalls Check Point Next GenerationFirewallsSECURE WEBGATEWAYSADVANCED THREATPROTECTION FireEye Network Security Fidelis NetworkFORENSICS ANDSECURITY SYSTEMSOTHERS Symantec Data Loss Prevention(DLP) Bivio Networks Cybersecurity Trend Micro Deep Security Cyphort Advanced Threat Detection Vectra Networks Cybersecurity RSA NetWitness Symantec ProxySG IBM QRadar Forcepoint Trusted GatewaySystemFEATURESFULL-PROXYARCHITECTUREThunder SSLi operates as a full-proxy,which enables adjusting of cipher suiteselection for encryption. Thunder SSLican re-negotiate to a different cipher suiteDECRYPTACROSS MULTIPLE PORTS ANDPROTOCOLSof similar strength, making the solutionfuture-proof against new ciphers or TLSversions that might be introduced to thenetwork without notice. Thunder SSLi canUsing Dynamic Port Inspection, Thunderensure traffic is encrypted using the mostSSLi decrypts traffic across all TCPsecure ciphers, eliminating the use ofports. Decryption for protocols likecompromised ciphers.STARTTLS, XMPP, SMTP and POP3 arealso supported.However, the decryption functionalitiesare not limited to only SSL/TLS, encryptedtraffic and decryption for SSH traffic issupported as well.MULTIPLE CIPHERSFOR PFS SUPPORTWith dedicated SSL accelerationhardware, Thunder SSLi delivers highperformance with 2048-bit and 4096-bitkey sizes, while supporting multiple ciphersuites, including DHE and ECDHE, forperfect forward secrecy (PFS) support.5
URLCLASSIFICATIONFOR SELECTIVE DECRYPTIONThunder SSLi URL classificationcategorizes the traffic of more than 460million domains, selectively bypassingtraffic decryption to enforce privacypolicies so private/sensitive data (e.g.,medical or financial records) is notEXPLICITPROXY SUPPORTIn addition to the standard transparentproxy deployment, Thunder SSLican also be deployed as an explicitproxy, giving more control over trafficmanagement. Thunder SSLi canconnect to multiple upstream proxyservers using proxy chaining.decrypted, in adherence to compliancestandards like HIPAA.URL FILTERINGFOR ACCESS CONTROLURL filtering is used to maximizeemployee productivity and reducerisks by blocking access to maliciouswebsites, including malware, spam andphishing sources.LOAD BALANCESECURITY DEVICESICAPSUPPORTData Loss Prevention (DLP) systemstypically use ICAP to connect to thenetwork and help prevent unauthorizeddata exfiltration. Thunder SSLi supportsICAP connectivity simultaneously withother decryption modes. This enables anetwork’s existing DLP systems withoutthe purchase of extra solutions.SERVICE CHAININGWith load-balancing support,FOR HIGH-PERFORMANCE SECURITYThunder SSLi dramatically increasesSelectively redirect traffic, based onperformance of firewalls and othersecurity devices. Easily add securitycapacity and extend the life of existingsecurity devices. Flexible weightedtraffic priorities can be assigned.application type, to different service chainswith fine-grained policies. Thunder SSLireduces latency and potential bottleneckswith the Decrypt Once, Inspect Many Timesapproach, consolidating decryption andencryption duties.SECURE HSMFOR FIPS COMPLIANCEThunder SSLi supports both internal andexternal network HSMs to ensure privateGRANULARTRAFFIC CONTROLkeys are securely stored. With industry-Examine, update, modify or dropleading support for up to four internalrequests DPI using A10 aFleX HSMs (FIPS 140-2 Level 3-validated),scripting. Fully control which traffic isThunder SSLi provides high performanceintercepted and forwarded to a third-with better security. Thunder SSLiparty security device, and which trafficinteroperates with existing externalshould be sanitized before being sent toHSMs deployed in the network.the intended destination.6
THUNDER SSLi PHYSICAL APPLIANCETHUNDERTHUNDERTHUNDERTHUNDERTHUNDER1030S SSLi3030S SSLi3040S SSLi3230S SSLi0.5 Gbps1.5 Gbps2.5 Gbps2.5 Gbps3.5 GbpsRSA (1K): 500RSA (2K): 300RSA (1K): 4KRSA (2K): 3kRSA (1K): 8kRSA (2K): 6kRSA: 6.5kECDHE: 4.5kRSA: 12.5kECDHE: 7k40k125k200k200k200k1 GE Copper566601 GE Fiber (SFP)022241/10 GE Fiber (SFP )22444PERFORMANCE*1840 SSLiSSLi ThroughputSSLi CPSSSLi Concurrent SessionsNETWORK INTERFACEManagement Ports1 x Ethernet Management Port, 1 x RJ-45 Console PortHARDWARE SPECIFICATIONSProcessorMemory (ECC RAM)StorageHardware AccelerationSSL Security Processor (‘S’ Models)Dimensions (Inches)Rack Units (Mountable)Unit WeightPower Supply (DC option available)Power Consumption (Typical/Max)*2Heat in BTU/Hour (Typical/Max)Cooling Fan*2Intel CommunicationsProcessorIntel Xeon 4-coreIntel Xeon 4-coreIntel Xeon 4-coreIntel Xeon 4-core8 GB8 GB16 GB16 GB16 GBSSDSSDSSDSSDSSDSoftwareSoftwareSoftwareSoftware1 x FTA-4N/AYesYesYesYes1.75 (H) x 17.0 (W) x12 (D)1.75 (H) x 17.5 (W) x17.45 (D)1.75 (H) x 17.5 (W) x17.45 (D)1.75 (H) x 17.5 (W) x17.45 (D)1.75 (H) x 17.5 (W) x17.15 (D)1U1U1U1U1U8.8 lbs18.0 lbs20.1 lbs (RPS)20.1 lbs20.6 lbs23 lbsSingle 150W (AC only)Single 600W*3Dual 600W RPSDual 600W RPSDual 600W RPS100 - 240 VAC,50-60Hz57W / 75W98W / 108W180W / 240W180W / 240W190W / 240W195 / 256334 / 369615 / 819615 / 819648 / 819Single Fixed FanOperating RangesRegulatory CertificationsStandard Warranty80 Plus Platinum efficiency, 100 - 240 VAC, 50 – 60 HzHot Swap Smart FansTemperature 0 - 40 C Humidity 5% - 95%FCC Class A, UL, CE,TUV, CB, VCCI, CCC,BSMI, RCM RoHSFCC Class A, UL, CE,TUV, CB, VCCI, CCC,KCC BSMI, RCM, FAC RoHSFCC Class A, UL, CE,TUV, CB, VCCI, CCC,KCC, BSMI, RCM,EAC, FAC RoHS,FIPS 140-2 , FCC Class A, UL, CE,CB, GS , VCCI, CCC ,KCC, BSMI, RCM RoHSFCC Class A, UL, CE,TUV, CB, VCCI, CCC,KCC, BSMI, RCM,NEBS RoHS90-day Hardware and Software7
Thunder SSLi Physical Appliance Specifications (Cont.)THUNDER3430S SSLiPERFORMANCE*1SSLi ThroughputTHUNDERTHUNDER4440S SSLi5330S SSLiTHUNDER5440S SSLiTHUNDER5840S SSLi5.5 Gbps8 Gbps10 Gbps15 Gbps20 GbpsRSA: 18kECDHE: 10kRSA: 22kECDHE: 10kRSA: 30kECDHE: 15kRSA: 35kECDHE: 20kRSA: 50kECDHE: 25k400k400k400k1 Million1 Million1 GE Fiber (SFP)400001/10 GE Fiber (SFP )4248242440 GE Fiber (QSFP )04044SSLi CPSSSLi Concurrent SessionsNETWORK INTERFACEManagement Ports1 x Ethernet Management Port, 1 x RJ-45 Console PortHARDWARE SPECIFICATIONSProcessorMemory (ECC RAM)StorageHardware AccelerationSSL Security Processor (‘S’ Models)Dimensions (Inches)Rack Units (Mountable)Unit WeightPower Supply (DC option available)Power Consumption (Typical/Max)*2Heat in BTU/Hour (Typical/Max)*2Intel Xeon 6-coreIntel Xeon 6-coreIntel Xeon 10-coreIntel Xeon 12-coreIntel Xeon 18-core32 GB32 GB32 GB64 GB64 GBSSDSSDSSDSSDSSD1 x FTA-42 x FTA-41 x FTA-42 x FTA-42x FTA-4YesYesYesYesYes1.75 (H) x 17.5 (W) x17.15 (D)1.75 (H) x 17.5 (W) x30 (D)1.75 (H) x 17.5 (W) x17.15 (D)1.75 (H) x 17.5 (W) x30 (D)1.75 (H) x 17.5 (W) x30 (D)1U1U1U1U1U23 lbs32.5 lbs23 lbs32.5 lbs32.5 lbsDual 600W RPSDual 1100W RPSDual 600W RPSDual 1100W RPSDual 1100W RPS80 Plus Platinum efficiency, 100 - 240 VAC, 50 – 60 Hz210W / 260W360W / 445W210W / 260W360W / 445W375W / 470W717 / 8871,229 / 1,519717 / 8871,229 / 1,5191,280 / 1,604Cooling FanHot Swap Smart FansOperating RangesRegulatory CertificationsTemperature 0 - 40 C Humidity 5% - 95%FCC Class A, UL, CE,GS, CB, VCCI, CCC,KCC, BSMI, RCM,NEBS RoHSStandard WarrantyFCC Class A, UL, CE,GS, CB, VCCI, CCC,KCC, BSMI, RCM RoHS, FIPS 140-2 , FCC Class A, UL, CE,GS, CB, VCCI, CCC,BSMI, RCM, NEBS RoHSFCC Class A, UL, CE,GS, CB, VCCI, CCC,BSMI, RCM RoHSFCC Class A, UL, CE,GS, CB, VCCI, CCC,BSMI, RCM RoHS90-day Hardware and SoftwareThe specifications, performance numbers are subject to change without notice, and may vary depending on configuration and environmental conditions.*1 Tested in single appliance SSLi deployment with maximum SSL option. Cipher “AES128-SHA256” with 2K RSA keys are used for RSA cases,“ECDHE-RSA-AES128-SHA256” with EC P-256 and 2K RSA keys are used for ECDHE case.*2 With base model. Number varies by SSL model.*3 Optional RPS available. Certification in process. FIPS model must be purchased.8
THUNDER SSLi PHYSICAL APPLIANCE WITH HSMTHUNDERPERFORMANCETHUNDER5440 SSLi with HSM*1,*2SSLi Throughput (RSA 2K keys)6630 SSLi with HSM15 Gbps40 Gbps50k100k1/10 GE Fiber (SFP )241240 GE Fiber (QSFP )40100 GE Fiber (CXP)0SSLi CPS (RSA 2K keys)NETWORK INTERFACE4Management Ports1 x Ethernet Mgmt port, 1 x RJ-45 console portHARDWARE SPECIFICATIONSProcessorMemory (ECC RAM)StorageHardware AccelerationSSL Security Processor (‘S’ Models)Dimensions (Inches)Rack Units (Mountable)Unit WeightPower Supply (DC option available)Power Consumption (Typical/Max)2 x Intel Xeon 12-core64 GB128 GBSSDSSD2 x FTA-44 x FTA-31 or 21, 2 or 41.75 (H) x 17.5 (W) x 30 (D)5.3 (H) x 16.9 (W) x 30 (D)1U3U32.5 lbs74.5 lbsDual 1100W RPS2 2 1100W RPS80 Plus Platinum efficiency, 100 - 240 VAC, 50 – 60 Hz*2Heat in BTU/Hour (Typical/Max)*2Cooling Fan400W / 485W995W / 1,150W1,365 / 1,6553,395 / 3,924Hot Swap Smart FansOperating RangesRegulatory CertificationsIntel Xeon 12-coreTemperature 0 - 40 C Humidity 5% - 95%FCC Class A, UL, CE, GS, CB, VCCI, CCC, BSMI, RCM RoHS, FIPS 140-2 Level 3Standard WarrantyFCC Class A, UL, CE, TUV, CB, VCCI, KCC , EAC, FAC RoHS, FIPS 140-2 Level 390-day Hardware and SoftwareThe specifications, performance numbers are subject to change without notice, and may vary depending on configuration and environmental conditions.*1 Tested with maximum HSM cards in two appliances SSLi deployment. Cipher RSA AES128-SHA with 2K RSA keys are used.*2 With base model. Number varies by HSM card option. Certification in process.9
DETAILED FEATURE LISTFeatures may vary by appliance.Decryption High-performance SSL decryptionand encryption as a forward proxy Full-proxy architecture Internet Content Adaption Protocol(ICAP) support for data lossprevention (DLP) and antivirussolutions Client certificate detection andoptional bypass Untrusted/expired certificatehandling using:-- Online Certificate StatusProtocol (OCSP)-- Certificate Revocation Lists(CRL) Dynamic port decryption to detectand intercept SSL or TLS trafficregardless of TCP port number TLS alert logging to log flowinformation from SSLi events Forward proxy failsafe to bypasstraffic when there is a handshakefailure aFleX scripting for customizable,application-aware switching Decryption bypass based onhostname; bypass list scales up to1 million Server Name Indication(SNI) values Firewall Load-Balancing (FWLB) Multi-bypass list support Extensive cipher and protocolsupport-- SSL 3.0, TLS 1.0/1.1/1.2-- RSA/DHE/ECDHE ciphers withPerfect Forward Secrecy (PFS)support-- SHA, SHA-2, MD5 MessageAuthentication Code (MAC)algorithms-- IPv4 and IPv6-- HTTP 1.1, HTTP/2 Decryption of HTTPS, STARTTLS,SMTP, XMPP, POP3, SSH, SCP,sFTP SSL session ID reuse High Availability: Active-Active,Active-Standby configurationsHardware Security Module(HSM) FIPS 140-2 Level 3-validated onboard HSM (Up to four cards on asingle platform)** External network HSM with ThalesnShieldDeployment Inline transparent proxy or explicitproxy deployment with non-inlinethird-party devices Inline transparent proxy or explicitproxy deployment with inline thirdparty devices Inline transparent proxy or explicitproxy deployment with ICAPconnected devices Inline transparent proxy or explicitproxy deployment with third-partytransparent and explicit proxydevices using proxy chainingManagement Dedicated on-box managementinterface (GUI, CLI, SSH, Telnet) Web-based AppCentric Templates(ACT) support SNMP, syslog, email alerts RESTful API (aXAPI) LDAP, TACACS , RADIUS support Configurable control CPUsURL Classification*** URL Bypassing for web categorybased selective decryption URL Filtering for blocking ofknown malicious or undesirablewebsites URL Classification Servicepowered by Webroot* Features may vary by appliance.** Available on select models.*** URL Classification for URL Filtering andBypassing subscriptions are available as anadditional paid service. 2017 A10 Networks, Inc. All rights reserved. A10 Networks, the A10 Networks logo, ACOS, Thunder and SSL Insightare trademarks or registered trademarks of A10 Networks, Inc. in the United States and other countries. All othertrademarks are property of their respective owners. A10 Networks assumes no responsibility for any inaccuraciesin this document. A10 Networks reserves the right to change, modify, transfer, or otherwise revise this publicationwithout notice. For the full list of trademarks, visit: www.a10networks.com/a10-trademarks.Part Number: A10-DS-15113-EN-10JUN 2017A10Networks.Optrics.comtoll free: 877.386.3763local: 780.430.6240
The most comprehensive decryption solution, A10 Thunder SSLi (SSL Insight) decrypts traffic across all ports, enabling third-party security devices to analyze all enterprise traffic without compromising performance. THUNDER SSLi REAL-TIME VISIBILITY INTO ENCRYPTED TRAFFIC DATASHEET ELIMIN