Transcription
SOLUTION GUIDEInternal Segmentation Firewall (ISFW)Control and Protect Against Threat Propagation and Damagein the Internal Network
IntroductionThe quantity, quality and impact of cyber attacks are on the rise. Breaches draw unwanted public attention, loss of reputation andcustomer confidence and may result in heavy recovery costs for the enterprise.As organizations embrace the latest IT technology such as Mobility and the Cloud, traditional network boundaries are becomingincreasingly complex to control and secure. There are now many different ways into an enterprise network.Organizations have been investing in perimeter security protection at different levels of the enterprise network – branches, campusand the data center – to prevent threats from entering their internal infrastructure. For a decade, this has proven to be a valuable andeffective strategy.In addition to the placement of firewalls at the network perimeter, additional purpose build security solutions are added to provideapplication level and APT multi-layered protection. Yet sophisticated attacks are still able to penetrate the enterprise network.Accepting the fact that threats will penetrate the perimeter, an additional security layer needs to be added in the internal network – onethat segments the access of potential threats vectors to critical resources, provides next generation security, greater visibility and limitspotential breach damage.2www.fortinet.com
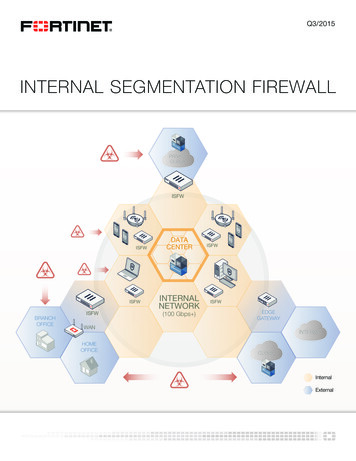
SOLUTION GUIDE: INTERNAL SEGMENTATION FIREWALL (ISFW)The ChallengeFact #1 – Threats’ Quantity, Sophistication and Impact Are on the Rise - In today’s environment, access points to the enterprisenetwork have multiplied exponentially. Mobility, smart devices and the cloud - all represent a growing attack surface through which agrowing number of sophisticated attacks and threats can enter the network.Fact #2 - The Internal Network is Flat and Open - To facilitate flexibility and agility, networks have become increasingly flatter andopen. Security implementation within the internal network is, in most cases, basic and limited to Virtual LANs and layer 4 access lists.Therefore, once beyond the security perimeter, exploits and hackers can easily and freely spread and gain further access to credentials,resources and data. Furthermore, the lack of security infrastructure within the internal network significantly limits the enterprise visibilityinto suspected traffic behavior, threats and data flows, which hinders its ability to detect a breach.Fact #3 - Virtual LAN (VLAN) Segmentation is Just Not Enough - Traditionally, internal network segmentation has been done viaVLANs deployment with intra-VLAN communication carried out by a routing function. VLAN segmentation may limit the spread of asimple threat to members within the same VLAN. However, more sophisticated threats can easily spread between VLAN as routers arenot security appliances and do not have the security services and awareness required to effectively identify and block threatsVLAN segmentation model has a very limited scalability and can only support up to 4K VLANs, which limits its ability to provide thenecessary micro segmentation in today’s enterprise environments that may contain thousands of servers and virtual machines.The Solution – Internal Segmentation FirewallTo help resolve the above challenges, enterprises should deploy enterprise firewalls with next generation functionality in strategic pointswithin the internal network, adding an additional security layer. The deployment of such firewalls, known as Internal SegmentationFirewalls (ISFW), will provide the following security benefits:1. Control access to critical resources/assets as close as possible to the user via policy-driven segmentation.2. Establish security barriers to stop and limit the uncontrolled spread of threats and hackers activity within the internal network via theimplementation of physical segmentation with advanced security mechanisms.3. Limit the potential damage of threats inside the perimeter.4. Increase threat visibility and enhance breach discovery and mitigation.5. Strengthen the enterprise’s overall security posture.To effectively achieve and maximize threat control and potential damage limitation, the deployment of ISFW relies on two foundations:nn Policy-driven firewall segmentationnn Physical & virtual firewall segmentationISFW: Policy-Driven Firewall SegmentationThe objective of policy-driven segmentation is to segment users’ access to the network, applications and resources via the associationof the user’s identity with security policies enforcement so that one can limit the potential attack vectors and threats carried by the user.Policy-based segmentation is the automatic association of user’s identity and the enforced security policy. A user’s identity may bedefined as a set of attributes, such as physical location, the type of device used to access the network, the application used, etc. As theuser’s identity may change dynamically, the enforced security policy must dynamically and automatically follow the user’s identity. Forexample, a user may have different policies enforced based on the type of device he is using to access the network.3
SOLUTION GUIDE: INTERNAL SEGMENTATION FIREWALL (ISFW)In order to achieve the required user identification and the overall parameters needed to create and enforce granular security policies,ISFW must be able to:1. Allow user, device and application identification2. Provide integration with the enterprise’s directory services solution, such as Microsoft’s Active Directory and others, to dynamicallyidentify user’s identity3. Dynamically map a user’s identity to a specific security policy and enforcementThe association of a user profile upon which a specific security policy will be enforced should happen as close as possible to the sourceor access point. Therefore, all firewalls deployed, at the various levels of the organization - from the branch office to the campus/HQ must have the ability to dynamically identify the user and enforce the appropriate policy throughout the organization. In effect, the entirefirewall infrastructure turns into an intelligent policy-driven segmentation fabric.ISFW: Physical & Virtual Firewall SegmentationPolicy-based segmentation also defines the security services applied by the firewall, such as AV, IPS and Application control. No matterhow efficient these may be, it is clear that an unknown threat may enter the network. To maximize threat detection and protectionand to limit the threat’s spread within the internal network – physical firewall segmentation must be put in place. The need for physicalfirewall segmentation is driven by the harsh realities of breaches and the growing adaptation of the zero trust concept – implyingmicro-segmentation of all assets and resources within the enterprise network via the deployment of adapted security infrastructure andmechanisms to effectively isolate servers, data repositories and applications.ISFW Functionality Throughout the EnterpriseVirtual ISFW for the Software Defined Data Center (SDDC) - With virtualization and software-defined computing massively deployedin enterprise’s data centers around the globe, micro-segmentation is already implemented via the deployment of advanced virtualfirewall appliances - segmenting each Virtual Machine (VM). These virtual ISFWs, such as the FortiGate-VM and FortiGate-VMX, providethe required security services for visibility, analysis and protection of traffic flows between virtual machines, also known as “east-west”traffic.Physical ISFW - For traffic flows entering and exiting the network perimeter and the data center, also known as “north-south” traffic,the implementation of physical ISFWs is required to provide a cost effective and scalable way to extend security segmentation andvisibility throughout the enterprise:nn from the deployment of virtual ISFWs for virtual machines’ micro-segmentation;nn through physical ISFWs within the internal network to provide security-enhanced segmentation of servers, applications and data,functions and departments;nn to the logical segmentation of user’s access to sensitive resources via ISFW policy-based segmentation.Unlike the implementation of ISFW in the virtual environment, where a single virtual FortiGate ISFW will segment and protect all VMswithin a server, determining the physical firewall segmentation granularity (size, performance and the number of Ethernet ports) dependsupon multiple factors such as the firewall’s physical location; the architecture of the network; the trust structure of the enterprise and thecriticality and location of datacenter assets.4www.fortinet.com
SOLUTION GUIDE: INTERNAL SEGMENTATION FIREWALL (ISFW)End-to-End ISFW - Although independent, combining policy-driven and virtual/physical ISFW will provide the following benefits:1. Policy-driven ISFW to limit users and threat vectors access to sensitive resources2. Ability to provide physical and virtual internal segmentation throughout the network3. Threats and their impact are now limited to the network segment they penetrated4. More visibility into the applications, users, devices and data flows in the internal network5. Shorten time for breach detection and mitigationISFW Considerations - The implementation of an ISFW infrastructure can be achieved via:1. Modifying the organization’s existing firewall infrastructure2. Adding firewalls to act as designated ISFWsAdding FortiGate firewalls to act as designated ISFWs provides the advantage of simplified deployment with Transparent Mode for rapiddeployment. In this mode, the firewall acts as a “bump in the wire” and is not seen as a router hop to connected devices and thereforeIP address modifications are not required.Whichever deployment option is chosen, the following criteria should be considered:nn Virtual and physical ISFWs for a complete end-to-end solutionnn Integration with directory servicesnn Enhancement of the security policies in place to allow policy-driven segmentationnn When required, addition firewall network ports for greater physical segmentationnn ISFW performance must meet the throughput and latency required while providing next generation security in a highlysegmented environmentInternal Segmentation Firewall with FortinetFortinet has pioneered the concept and deployment of Internal Segmentation Firewalls as part of its Advanced Threat Protection (ATP)framework, protecting organizations against today’s most sophisticated threats.Fortinet provides a dynamic, manageable and scalable ISFW solution:1. User/Device/Application-aware FortiGate firewall policies for policy-driven segmentation2. Integration with RADIUS, LDAP, Active Directory for user authentication & management3. FortiGate firewalls provide a rich set of security services, including AV, IPS and Application Control, to provide maximum internalnetwork protection4. FortiGate physical appliances are ASIC based to provide the required high performance, speed and low latency required in a highlysegmented environment5. FortiGate virtual firewalls provide ISFW functionality in the SDDC and public clouds6. Wide range of physical and virtual FortiGate ISFW appliances to fit performance and scalability required for optimized segmentationthroughout the network7. A scalable, manageable and automated end-to-end solution with FortiManager, FortiAnalyzer/FortiView and FortiAuthenticator5
SOLUTION GUIDE: INTERNAL SEGMENTATION FIREWALL (ISFW)ManagementISFW is a component within Fortinet’s end-to-end security platform, from secured wireless access to physical and virtual datacenterfirewalls and application level security appliances, all managed under a single pane of glass – with FortiManager and FortiAnalyzer.In the context of an ISFW deployment, the number of defined policies is expected to grow with policy-driven internal segmentation. Inaddition, any firewall in the enterprise network should be capable of dynamically enforcing policy-based segmentation, requiring everyfirewall to be aware of the entire range of policies defined.Such requirements can potentially create a management nightmare and impact the firewalls resources.Fortinet’s FortiManager, FortiAnalyzer and FortiAuthenticator address these issues by:1. Defining policies once through FortiManager2. FortiManager automatically distributes the policies to the firewalls participating in the ISFW functional segmentation3. User awareness and policy-based segmentation scalability is achieved via the integration of FortiAuthenticator – providingintegration & automation of FortiGate firewalls and the Directory Services4. FortiAnalyzer and FortiView provide a granular and aggregated traffic visibility (users, devices, applications, threats, etc.) throughoutthe enterpriseSummaryAs threats grow in numbers, sophistication and impact, it is clear that placing all the security emphasis in the network perimeter is notenough.Internal Segmentation Firewalls provide organizations with an additional layer of protection inside their network perimeters, protectingcritical assets while enhancing their ability to detect breaches and shorten mitigation delays.With high performance virtual and physical ISFWs under a single pane of glass management, Fortinet leads the way and provides agranular, cost effective and high performance end-to-end ISFW solution for the most demanding organizations and environments.6www.fortinet.com
SOLUTION GUIDE: INTERNAL SEGMENTATION FIREWALL (ISFW)7
GLOBAL HEADQUARTERSFortinet Inc.899 Kifer RoadSunnyvale, CA 94086United StatesTel: 1.408.235.7700www.fortinet.com/salesEMEA SALES OFFICE120 rue Albert Caquot06560, Sophia Antipolis,FranceTel: 33.4.8987.0510APAC SALES OFFICE300 Beach Road 20-01The ConcourseSingapore 199555Tel: 65.6513.3730LATIN AMERICA SALES OFFICEProl. Paseo de la Reforma 115 Int. 702Col. Lomas de Santa Fe,C.P. 01219Del. Alvaro ObregónMéxico D.F.Tel: 011-52-(55) 5524-8480Copyright 2015 Fortinet, Inc. All rights reserved. Fortinet , FortiGate , FortiCare and FortiGuard , and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product orcompany names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other resultsmay vary. Network variables, different network environments and other conditionsmay affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expresslywarrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any such warranty will belimited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants, representations,and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publicationwithout notice, and the most current version of the publication shall be applicable. 09 Oct 2015 – 9:54 AM MKT-STORAGE:01 BROCHURES:05 SOLUTION GUIDES:SG-Internal Segmentation Firewall:SG-Internal Segmentation Firewall Folder:SG-Internal Segmentation Firewallwww.fortinet.com
Internal Segmentation Firewall with Fortinet Fortinet has pioneered the concept and deployment of Internal Segmentation Firewalls as part of its Advanced Threat Protection (ATP) framework, protecting organizations against today’s most sophisticated threats. Fortinet provides a dynamic, manageable and scalable ISFW solution: 1.