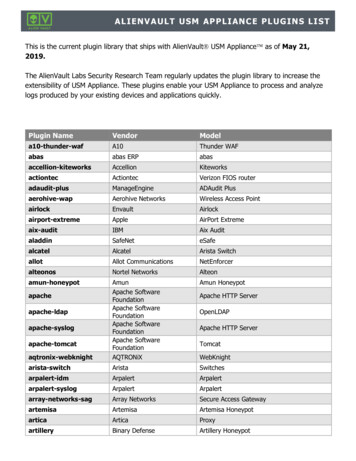
Transcription
Netflow Collection with AlienVaultAlienvault 2013CONFIGUREConfiguring NetFlowNetFlow Capture of TCP/IP Trafficfrom an AlienVault Sensor or Remote HardwareLevel: Beginner to IntermediateNetflow Collection with AlienVault - Page 1 of 17
ContentsNetflow Collection with AlienVault . 1Alienvault 2013 . 1Introduction. 3The NetFlow Specification . 3NetFlow as a Security Tool . 4Prerequisites. 5Installation . 5Configuration. 6Enabling Netflow Collection from an AlienVault Sensor . 6Collecting Netflow Data from an External Source . 8Configuring the External Device to send NetFlow/sFlow data to Alienvault . 12Validation . 13Troubleshooting . 15Netflow Collection with AlienVault - Page 2 of 17
IntroductionThe NetFlow SpecificationNetFlow is a protocol designed and published by Cisco Systems that has become the acceptedindustry standard for recording and transmitting information about network flows (connectionsbetween hosts via the TCP/IP protocols) on a network.Flows are unidirectional – a standard TCP session will create two flows – one of the traffic fromhost A to host B, a second of the traffic from Host B to Host A.A flow record (using netflow v5, the most commonly adopted version), will contain thefollowing information about the traffic session:1.2.3.4.5.6.7.Network InterfaceSource IP AddressDestination IP AddressIP ProtocolSource port (for UDP or TCP flows, 0 for other protocolsDestination port (for UDP or TCP, type and code for ICMP, or 0 for other protocols)IP Type-Of-Service flagsThis is the bare minimum information contained in a flow, however versions 7 and 9 of thenetflow standard include many additional supported fields. Of these additional fields, the onesmost relevant to Netflow in the content of AlienVault USM or OSSIM are:8. TCP Flags9. Total Packets in Flow10. Total Bytes in Flow11. Packets Per Second (PPS)12. Bits Per Second (BPS)13. Average Bits Per Packet (BPP)14. Duration (milliseconds)Netflow Collection with AlienVault - Page 3 of 17
NetFlow as a Security ToolAlthough designed to assist network adminstrators generate metrics for performance andutilization of their networks, NetFlow has garnered increasing utility in recent years as a vitaltool for security analysis, detection and forensic investigation. With many standard securitycontrols placed around the perimeter of the network, netflow has proven to be vital wheninvestigating intrusions that pass the ‘hard outer shell’ and start migrating throughout the ‘softunderbelly’ of an organization.Operating Systems and applications are rarely configured to log every last action they perform (unless placed into debug mode, an option rarely used since it carries an accompanyingperformance cost ) and all too often, this can leave a critical gap in the forensic reconstructionof an event.Services may log who connected to them, but not from where, or when a session was started,yet not when it was closed. Cross-referencing application and service logs against the records ofnetwork traffic to that host, can allow analysts to infer the missing information needed to tracethe path of a successful intruder across the network.17:28 Connection fromExternal HostHost A21:28 Connection fromHost AHost BWas our attacker still connected to Host A when it connected to Host B ?17.28 Connection from External Host (to Host A)Flow: src: externdst:host A duration21.28 Connection from Host A to Host B18501291millisecondsYES!Netflow Collection with AlienVault - Page 4 of 17
PrerequisitesNetflow is entirely dependent upon having visibility to traffic traversing the network – whichmeans the routers and switches that traffic flows over. There are two ways to acquire this: The Router or Switch is configured to accrue netflow data directly, and transmit it to acollector.The Switch is configured with a SPAN/Mirror port to clone all traffic to a single port,attached to a system that will generate netflow data from the observed packets.AlienVault supports both of these scenarios: Netflow data can be sent to an AlienVault sensor, and incorporated into SIEM DataThe Sensor (which should be connected to a SPAN port for normal functionality) cangenerate its own netflow data from observed traffic.These options are not mutually exclusive and many practical deployments will incorporate bothmethods of collection.InstallationNetflow Collection and Analysis is included with AlienVault by default and no additionalinstallation is necessary.External Netflow sources (switches, etc) have their netflow capabilities defined in theiroperating firmware and usually require only some minimal configuration to enable itNetflow Collection with AlienVault - Page 5 of 17
ConfigurationEnabling Netflow Collection from an AlienVault SensorAfter a default installation, Netflow defaults to being disabled on an AlienVault Sensor, andmust be activated and configured before collection will begin.NetFlow Collection is configured on a per-sensor basis, in the sensor configuration screen:access this through the sidebar menu at Deployment - AlienVault Components Select the Sensors tab at the top: And click the IP Address of the sensor to be configured: The main sensor configuration screen will load: at the very bottom of the configurationpage is the Flow configuration section.Netflow Collection with AlienVault - Page 6 of 17
There are three primary configuration options, all of which may safely be left with their defaultvalues:PORT: This is the port that the sensor will transmit netflow data back to the AlienVault servervia. Each sensor must transmit on a unique port number. A suitable default will appear in thistext box and is recommended to leave it as this default unless there is a specific operationalreason to (perhaps a specific port range your network has assigned for administrative trafficACLs).TYPE: This is the type of netflow data that the sensor will receive from external sources. If youare only using the Sensor to generate netflow data, this value can be ignored.COLOR: A color value to visually identify flows collected from this sensor in the Flows analysissection of the AlienVault User Interface.Once you have chosen appropriate values (or left them as their defaults), click the Configureand Run button to activate Netflow Collection/Generation from this SensorYou will receive confirmation that the sensor is now generating netflow data – this messageassumes you are configuring an external collector however – the firewall exception for anAlienVault sensor will be automatically created.The configuration section will update to indicate that flow collection is now working.Netflow Collection with AlienVault - Page 7 of 17
Collecting Netflow DataData from an External SourceThird party devices that support the collection and transmission of NetFlow (or the variantsFlow) data, may also be configured as a source of traffic accounting information withinAlienVault.The process to add an additional Flow source is: Create a new Sensor record for the transmitting deviceConfigure the device to transmit NetFlow or sFlow information to the AlienVaultServerPreparing the Sensor EntryTo register Netflows from external devices with their own unique identify and color in flowlistings, a ‘Dummy’ Sensor entry must be created within the AlienVault UIThis Sensor entry will appear to be an AlienVault Sensor, but will permanently appear as‘disconnected’ in the Sensor listing UI screen.Add a New Sensor Entry Return to the Sensor Listing screen at Deployment - AlienVaultComponents Select the Sensors tab at the top: Select “New”Netflow Collection with AlienVault - Page 8 of 17
You will get the Sensor configuration screen – but with no informationpopulated. Fill it out with information about the NetFlow device you areadding. Click Update, you will receive confirmation of the sensor record beingcreated Re-open the sensor configuration window (click the IP address of the newlycreated sensor record) Scroll down the sensor config screen, down to the Services section, disableall services. This is not necessary, but will prevent this ‘dummy’ sensor fromshowing up as an available sensor in the parts of the AlienVault UI that referto these services.Netflow Collection with AlienVault - Page 9 of 17
At the bottom of the screen is the Netflow section.o Select a port that the AlienVault Server will receive NetFlow dataover.o Select NetFlow or sFlow as appropriate for what the device will besending to AlienVault.o Choose a color to display flows in the Flow Analysis UI.o Configure and Run You will receive a message stating that a new firewall exception must beadded to added to the AlienVault Server’s firewall settings.As of version 4.2 this is no longer necessary Select BackNetflow Collection with AlienVault - Page 10 of 17
Firewall ExceptionDespite the message box, as of version 4.2 the firewall exception can be automatically created,by disabling and re-enabling the AlienVault Server’s Firewall. This must be done from the AlienVault Physical Console, or remotely viaSecure Shell.You will need the root account credentials to perform thisThe root user account is only for console access, and is different from theadmin credentials used in the Web User Interface.root credentials are created during installation of AlienVault.Log IntoInto the ConsoleThe next step involves forcing a global rebuild of the AlienVault core configuration. This must bydone at the AlienVault Console (Either by opening the physical console, or using Secure Shell(SSH) log into the AlienVault Server with the root account)Access the AlienVault Console, you will be presented with the Alienvault-Setup console tool.Select the Jailbreak option to access the administrative command line. Select Jailbreak this Appliance to access the command lineAccept the DisclaimerNetflow Collection with AlienVault - Page 11 of 17
Run the command ossim-reconfig The reconfiguration tool will run (may take a few minutes) The Server should now be reachable over UDP, on the port configured for the newnetflow source.Configuring the External Device to send NetFlow/sFlow data to AlienvaultThe final step is to configure the device itself to transmit flow data to the AlienVault Server. Thisprocess is dependent upon the third party device itself. We have made efforts to assembleconfiguration instructions for major device types into accompanying documents, but be awarethat these are third party devices and the information presented here may be outdatedbecause of more recent updates to these devices by their manufacturer.Always consult your device documentation and support channels before carrying out any of theconfigurations listed on the following pages.Netflow Collection with AlienVault - Page 12 of 17
ValidationWith the Server, Sensor and any appropriate devices now configured, all that remains is tovalidate the successful collection of Netflow.Since this process is dependent upon witnessing live data being collected by the system, it isadvisable to wait a short, appropriate length of time before validation (thirty minutes at themost, should provide a good sampling size window)Open the Netflow Analysis UILocated under Situational Awareness - Network:The primary screen should give quick visual confirmation of Netflow data being captured:The colors used to plot the flow graphs, are the colors assigned to each sensor during theconfiguration stage.If you see graph data with the color assigned to your new flow collector, this is the firstindicator of successful configuration.Netflow Collection with AlienVault - Page 13 of 17
View Individual FlowsScroll to the bottom of this UI section and locate the Netflow Processing section of the UISelect and highlight only the sensor you have just configured, then click List last 500 Sessions;After a few seconds a new panel should display beneath the Netflow Processing panel:Data appearing in this panel, is absolute confirmation of successful Netflow Configuration onthis new collector.Netflow Collection with AlienVault - Page 14 of 17
TroubleshootingIf flow data does not appear after a reasonable amount of time, validate that flow data issuccessfully being transmitted and received by the AlienVault server.Validate that Netflow packetspackets are being generated by the Sensor If you are collecting netflow packets from a third party device, skip this section and dowhatever troubleshooting is appropriate to determine that netflow collection isfunctioning correctly on that deviceLog in to the physical console of the Alienvault Sensor.Acquire commandline access via the ‘jailbreak this appliance’ optionValidate that the fprobe system is running, and that it is listening to the correctinterface, and sending packets on the correct port to the server# ps ax grep fprobe The output should appear similar to the following: Confirm that –iethX is the correct interface number for the sensor interface connectedto the switch SPAN port.Confirm that the IP address is the IP address of you AlienVault ServerConfirm that the port number (the number after the colon in the address) is the samenumber you configured in the Netflow UI. Netflow Collection with AlienVault - Page 15 of 17
Validate that Netflow packetspackets are being received by the Server Log in to the physical console of the Alienvault Server.Acquire commandline access via the ‘jailbreak this appliance’ optionValidate that nfcapd is running, and listening on the port assigned for the appropriatesensor# ps ax grep fprobe The output should appear similar to this: There will be multiple instances of nfcapd, one for each netflow sourceThe number after the –p argument should match the port assigned to a particularnetflow source.Use tcpdump to validate that packets are being transmitted to the Server. # tcpdump –I interface ‘port netflow port ’ If packets are being received from the netflow source, you should see output similar tothe following Use ctrl-C to exit tcpdump.Netflow Collection with AlienVault - Page 16 of 17
Validate that Netflow packetspackets are accepted by the Server Firewall Log in to the physical console of the Alienvault Server.Acquire commandline access via the ‘jailbreak this appliance’ optionValidate that the firewall configuration has an exception to allow incoming netflowpackets over the appropriate UDP port# iptables –L –n –v grep configured port The output should resemble the following: The ‘udp dpt’ (destination port) is the important part here, indicating that traffic will beACCEPT’ed by the firewall configuration. The number in the left column indicates thenumber of packets that have previously matched this ACCEPT rule.Netflow Collection with AlienVault - Page 17 of 17
Netflow Collection with AlienVault - Page 13 of 17 ValidationValidation With the Server, Sensor and any appropriate devices now configured, all that remains is to validate the successful collection of Netflow. Since this process is dependent upon witnessing live data being collected by the system, it is