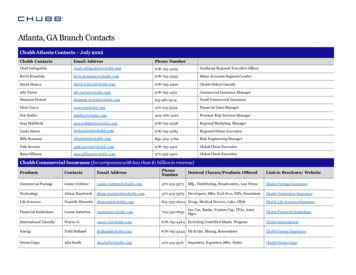
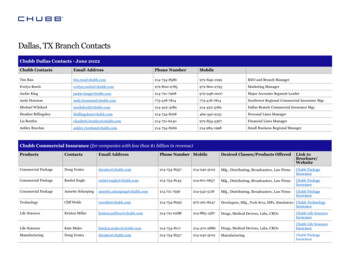
Transcription
Chubb Cyber EnterpriseRisk ManagementFact SheetFinancial Lines
Chubb Cyber EnterpriseRisk ManagementWhen it comes to a data security breachor privacy loss, it isn’t a matter of if itwill happen as when it will happen.So when it does happen, you’ll needcomprehensive protection from aninsurer that specialises in handlingcyber risks, offers a full suite of integratedinsurance solutions to help minimisegaps in coverage, and understandshow to tailor coverage to your business.2
The InformationAge is ChangingBusiness Modelsand InsuranceNeedsThe information age allows us to collectmore data, store more data and extractinformation around the globe 24/7. Thisaccess to private and sometimes sensitiveinformation can significantly increasea company’s vulnerability to cybersecurity threats - any of which can resultin significant out-of-pocket costs that candevastate an organisations bottom line.Cyber attacks undermine customer,regulatory and employee confidence.They can severely damage the reputationof an organisation which leads toincreased customer churn and potentialmonitoring by regulators.How prepared is your organisationfor: Costs for forensic investigations anddisaster recovery relating to theft ofnon-public privacy information orpersonal records? A business interruption eventincluding expenses that result from asecurity failure or internet virus? A cyber extortion threat? Costs related to privacy notification,incident response and recoveryexpenses, public relations costs orcredit monitoring? A lawsuit stemming from a securityfailure or alleged technology thatresults in damages to customers? A regulatory proceeding seekingfines or penalties as a result of actualor potential unauthorised access toprivate information?The Costs of Data Security Breachescan be Significant The estimated annual cost of cyberattacks to the global economy ismore than 400 billion.1Cyber attacks affected 5 millionAustralians at an estimated cost of 1.06 billion.2Information theft is the mostexpensive consequence of a cybercrime (43% of cost) followed bybusiness disruption (33%).3 The average cost of cyber crime toan Australian business is US5.41million, an increase of 26% from theprevious year.3Gaps in Traditional InsuranceThe Internet has no boundaries andas business models evolve throughthe use of new technologies, so musttraditional insurance programs and riskmanagement practices. Businesses maybe operating under the belief that theirexisting insurance policies are enoughto cover their data security and privacyexposures. Unfortunately, this is not thecase and traditional insurance policiesmay be inadequate to respond to theexposures organisations face today.Consider these traditional policies:General Liability policies are typicallytriggered in response to Bodily Injury(BI) and Property Damage (PD) claims.A cyber attack will not usually involveeither BI or PD. General Liability policiestypically don’t offer cover for any firstparty costs.Property/ISR policies typically respondto destruction or damage to tangibleproperty resulting from a physicalperil. The tangible loss then permitsthe business interruption and extraexpense cover to respond. A cyberattack can cause no physical damage,yet the attack can shut down a businessresulting in substantial expense costsand loss of income.Crime policies typically respondto direct loss from employee theftof tangible property and money orsecurities. Computer crime extensionsusually exclude any third-party liabilitycover and don’t cover the loss ofconfidential information.1. Centre for Strategic and International Studies, Net losses: Estimating the global cost of cybercrime—Economic impact of cybercrime II, report, June 2014, McAfee, p. 2. 2. Symantec, 2013 Norton report:Total cost of cybercrime in Australia amounts to AU 1.06 billion, media release, 16 October 20133. Ponemon Institute /Accenture, 2017 Cost of Cyber Crime Study, page 30.3
Chubb Cyber Enterprise Risk ManagementNo Company is ImmuneCyber risk is an enterprise wide issue thataffects companies large and small. Thetargets of cyber attacks span a multitudeof industries including construction,retailers, restaurants, media companies,manufacturers, banks, asset managers,defence contractors, transportorganisations, healthcare organisations,agriculture and professional firms,just to name a few.Are your clients prepared?The Solution: Cyber EnterpriseRisk ManagementChubb Cyber ERM is more thana policy, it is a risk managementsolution. Cyber Enterprise Risk Managementis a comprehensive packagedesigned by cyber risk expertsto address the full breadth ofrisks associated with doingbusiness in today’s technologydependent world. The policy offers full life cyclesupport in the event of a networkattack or privacy breach. The solution includes capabilitiesfor both first party liability andthird party liability via severaldifferent insuring agreements. Policyholders have access topre event risk mitigation servicesand post event incident responsemanagement, supported bya 24/7/365 call centre,Chubb’s expert vendors andaward winning claims team.Coverage HighlightsThird-Party Cyber Liability Coverage for: Privacy liability arising from theinsured’s handling of sensitivenon-public personal information,confidential third party corporateinformation, and violations of theInsured’s privacy policy.4Network Security Liability Stemming from the insured’smanagement of their networkoperations. This could include theimpaired access to the Insured’snetwork from an attack, virusattacks (malicious code), the use ofthe insured’s network in a denial ofservice attack, or the introductionof malicious code. Regulatory Fines Payment CardLoss (PCI) and consumers finesresult from Privacy or NetworkSecurity Liability. First-Party Expenses Incident Response Expenses including forensic investigationcosts, notification expenses and/or regulatory advice. Also, creditmonitoring services, identity theftmonitoring and fraud services foraffected customers are included. Business interruption and recoverycosts including the cover for actsof criminal hackers, maliciousoutsiders and distributeddenial-of-service (DDoS) attacks.Coverage triggers are extendedto human error (fat finger cover)programming errors and powerfailure of your computer systems.Recovery costs to remove malware,reconstruct insured data or costs tomitigate business income loss.Cyber extortion expenses, includingthe cost of hiring crisis negotiators,regulatory IT and PR consultants.Data asset loss, includes cover forexpenses resulting from entry to,corruption of, or destruction of anInsured’s data.Chubb’s Cyber PropositionPre-QuotePre-BindServicesChubb CyberIncident ResponsePlatformOn RiskPre-EventServices
Chubb Cyber Incident Response ProcessPolicyholder calls Chubb Cyber Incident Response Hotline1800 027 428 or Chubb claims team direct (9am-5pm).Hotline is available worldwide 24/7/365.Local Incident ResponseManager (IRM) assignedIncident assessmentbegins.Within 5 hours.Post Incident Activity Analysis Policy response Future remediation Lessons learnt Risk mitigationExpert vendors AssignedBased on Chubb’s incident triage,our panel of expert vendors areassigned to the incident. i.e. Privacy or Data breach Rogue employee actions Nation state threatWithin 24 hours.Incident Containmentand Recovery.Initial incident debriefbetween IRM andpolicyholder.Chubb Cyber ERM offers a comprehensive range of pre and post breachservices to help your clients navigate the digital age.Please contact your local Chubb distribution team for more information.Note: A call to the Hotline does not constitute notification under the policy unless the Insured specifically requests notification to Chubb.5
Chubb Cyber Enterprise Risk ManagementLoss ScenariosConsider the following loss scenariosbased on actual claims and then askyourself whether you haveadequate insurance in place.Type of Organisation:Third-Party AdministratorEmployees:500Annual Turnover: 65,000,000Coverage Considerations:e-Business Interruption, PrivacyNotification and Crisis Management,Conduit Wrongful Act, ImpairedAccess Wrongful Act and DisclosureWrongful Act.A clandestine organisation hacked anadministrator’s network prior to a majorholiday weekend and stole personallyidentifiable information. In addition toobtaining the names and credit cardinformation of 25,000 customers, theorganisation stole the employee dataof the 250 staff members. A virus wasalso placed into the administrator’s ITnetwork, rendering the firm unable toconduct business for 72 hours.The administrator’s clients wereunable to access the network forbusiness purposes and sustainedvirus related impacts to their ownsystems. The clients sued theadministrator for impaired accessand conduit related injuries.The administrator incurred costs of 250,000 for forensic investigations,notification and monitoring measures,system restoration and legal advice.They also sustained more than 2,000,000 in lost business incomeand extra expense associated with thesystem shutdown. 300,000 in defencecost where incurred and 5,000,000in damages where paid to customerswho where unable to access theadministrator’s network.6Type of Organisation:HotelEmployees:2,500Annual Turnover: 250,000,000Coverage Considerations:Privacy Notification and CrisisManagement.A former hotel executive gainedunauthorised access to the hotel’sconfidential database of names andcredit/debit card information of75,000 customers as well as personalinformation of 2,500 employees. Theinformation was sold to an organisedcrime network.The hotel incurred more than 2,500,000 in expenses associatedwith the forensic investigation,notifying customers, credit andidentify monitoring and restoration,public relations and regularly actiondefence costs. The hotel was also fined 2,500,000.
Type of Organisation:ManufacturerType of al Turnover: 10,000,000Annual Turnover: 20,000,000Coverage Considerations:Disclosure Wrongful Act, PrivacyNotification and Crisis Management.Coverage Considerations:e-Threat, e-Business Interruption,Privacy Notification and CrisisManagement.A manufacturer leased a copyingmachine for a 2 year period through athird-party intermediary. During the 2years the manufacturer made copiesof business information, includingproprietary client information and itsown employee data. After the leaseexpired the manufacturer returnedthe machine via the third-partyintermediary. Prior to making its wayback to the actual leasing companya rogue employee of the third-partyintermediary accessed the machine’sdata and stole and sold the proprietaryinformation.The manufacturer incurred 75,000in connection with a forensicinvestigation, notification, identitymonitoring, restoration services andindependent counsel fees. It alsoincurred approximately 100,000 inlegal defence costs and 275,000 inindemnity associated with the theft andsale of proprietary client information.Hackers obtained access to a law firm’snetwork and claimed to have access tosensitive client information, includinga public company’s acquisition target,another company’s prospective patenttechnology, the draft prospectus of aventure capital client and a significantnumber of claimants’ personallyidentifiable information. The firm wascontacted by the hacker group seeking 10,000,000 not to place the stoleninformation on-line.The law firm incurred 2,000,000for forensic investigation, extortionrelated negotiations, a ransom payment,notifications, credit and identitymonitoring, restoration services andindependent lawyers’ fees. The firmalso sustained 600,000 in lost businessincome and expenses associated withthe system shutdown.7
Chubb Cyber Enterprise Risk ManagementRisk MinimisationBusinesses have become more relianton technology to operate but it is stillpeople and our desire to trade thatcreates the exposures. Yesterday’s risksnow manifest themselves very differentlyin today’s digitally connected world. AtChubb we understand how to help limityour cyber exposure and insurance costs.Simple network hygiene reduces anorganisations exposure to cyber risk.The Australian Signals Directoratesuggests organisations that utilise thefollowing 8 strategies can mitigate up to85% of common cyber attacks.11.Application whitelisting – only allowselected software applications torun on computers. This can preventall other unapproved softwareapplications, including malware frominfiltrating your network.2. Patch applications – patchingsecurity vulnerabilities in softwareapplications and keeping themup to date. A regimented patchmanagement process maintainssystems integrity. Threat actorsuse known vulnerabilities totarget computers.3. Disable untrusted Microsoft Officemacros – Microsoft Office “macros”which can automate tasks should bedisabled. These macros are used toautomate the download of malwareso should be secured or disabled.4. User application hardening –block browser access to variousitems that are popular ways to delivermalware and infect computers, i.e.Adobe Flash player, web ads anduntrusted Java code.5. Restrict administrative privileges– only use administrator privilegesfor managing systems, installinglegitimate software and applyingsoftware patches. This accessshould be restricted to onlythose that need them.86. Patching Operating Systems –keep your operating systemsup to date and fully patched forvulnerabilities. Threat actors willuse known vulnerabilities to targetan organisations network.7.Multi-Factor authentication –strengthen password controls byusing strong authentication withan additional “factor”, such as aphysical tokens or ‘something youhave’. Having multiple levels ofauthentication makes it much harderfor adversaries to accessyour information even if the“password” is breached.8. Daily Backup of Important Data –it may sound obvious but maintaininga regular backup of all data that isstored securely offline will greatlyassist with business continuity shouldan organisation suffer a cyber attack.Don’t forget to test the integrity ofthose back-ups!In addition to the 8 mitigation strategiesabove, it is also good practice to prepareyour response to a major cyber attackand update business continuity plans.9. Have an Incident Response Plan(IRP) An organisation with a clear,concise and tested IRP will be abletake fast action to contain a breachand minimise the financial damageto an organisation. They are morelikely to have a better response tolegal requirements and potentialcostly fines.10. Appoint a Chief SecurityInformation Office (CISO) network and data security is anenterprise wide risk and not a riskthat can be managed within the siloof the IT department. A CISO (orequivalent) should be responsible fordata protection and have centralisedresponsibility for data management.The CISO should lead and coordinatean enterprise’s response (GeneralCounsel, Risk Management, PR/Marketing, Executive Management)to a cyber attack. This person shouldbe listed in the IRP.
Why Chubb?Leadership — We have been committedto protecting organisations with contentexposures for over 40 years. Ourexpertise allowed us to develop “all risk”coverage. What’s more, Chubb offers afull suite of complementary insurancesolutions, including directors andofficers liability, employmentpractices liability, and propertyand casualty coverages.Protection — The true measure ofan insurer is how it responds to andmanages claims. We strive to treat eachcustomer the way we would like to betreated if we experienced the same loss with integrity, empathy, promptness,and fairness - and to reach mutuallyagreeable outcomes.Endurance — Chubb’s financial stabilityand ability to pay claims rate amongthe best in the insurance industry,as attested by the leading insurancerating services.9
About Chubb in AustraliaChubb is the world’s largest publiclytraded property and casualtyinsurer. Chubb, via acquisitions byits predecessor companies, has beenpresent in Australia for over 50 years.Its operation in Australia (ChubbInsurance Australia Limited) providesspecialised and customised coveragesinclude Marine, Property, Liability,Energy, Professional Indemnity,Directors & Officers, Financial Lines,Utilities as well as Accident & Health,for a broad client base, including manyof the country’s largest companies.Contact UsChubb Insurance Australia LimitedABN: 23 001 642 020 AFSL: 239687Grosvenor PlaceLevel 38, 225 George StreetSydney NSW 2000O 61 2 9335 3200F 61 2 9335 3411www.chubb.com/auMore information can be found atwww.chubb.com/auInsurance cover is issued by Chubb Insurance Australia Limited, ABN 23 001 642 020, AFS Licence Number 239687. Thismaterial contains general information only and may not suit your particular circumstances. The precise insurance coverprovided is subject to the terms, conditions and exclusions set out in the relevant Policy Wording and the insurancepolicy when issued. Insurance cover may not apply to the extent that trade or economic sanctions or other laws orregulations prohibit Chubb, its parent company or its ultimate controlling entity from providing insurance cover. Chubbis authorised to provide general insurance products. Please obtain and read carefully the relevant insurance policybefore deciding to acquire any insurance product. A Policy wording can be obtained at www.chubb.com/au; throughyour broker or by contacting any of the Chubb offices. Chubb Cyber Enterprise Management Fact Sheet, Australia.Published 10/2017. 2017 Chubb Insurance Australia Limited. Chubb , its logos, and Chubb.Insured.SM are protectedtrademarks of Chubb.Chubb10-105-1117
Within 24 hours. Policyholder calls Chubb Cyber Incident Response Hotline 1800 027 428 or Chubb claims team direct (9am-5pm). Hotline is available worldwide 24/7/365. Local Incident Response Manager (IRM) assigned Incident assessment begins. Within 5 hours. Chubb Cyber ERM off ers a comprehensive range of pre and post breach