Transcription
Secure Science DMZ usingEvent-Driven SDNTae HwangTechnical Solutions Architect @ Cisco
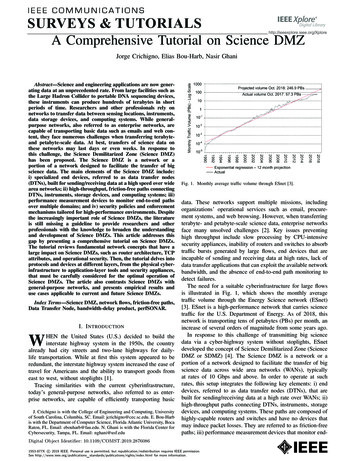
Typical Science DMZ Network Architecture “1.0”What is the biggest challenge with this architecture?InternetFirewallI2 AL2S/AL3SCampusUCS B200 M3Traffic is managed viasimple ACL orFlow RuleUCS B200 M3UC S5 1 0 et!ConsoleReset2UCS B200 M3UCS B200 M3SLOTSLOT34UCS B200 M3UCS B200 M3SLOT6SLOT5UCS B200 M3UCS B200 M3SLOTSLOT78OKFAILOKFAILOKFAILOKFAILDMZ SwitchUCS B200 M3UCS B200 M3UC S5 1 0 !ConsoleReset!ConsoleReset2UCS B200 M3UCS B200 M3SLOTSLOT34!ConsoleReset!ConsoleResetUCS B200 M3UCS B200 M3SLOT6SLOT5UCS B200 M3UCS B200 TN/Servers/Storage/perfSONAR 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential2
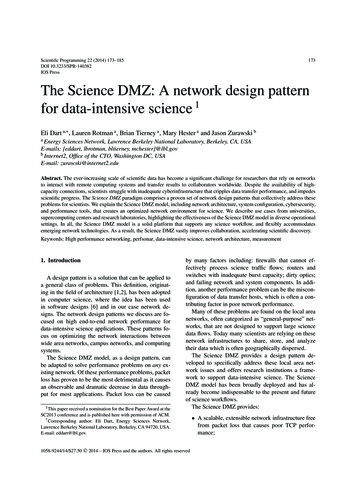
Science DMZ “2.0”SciPassOperation- Phase 3n - Phase2BypassingCampusFirewallfor Large ss Architecture: Combined with Brocade OF Switch (typically), SciPass inserts bypassBro IDS, PerfSONAR, and SciPass controller (Indiana University)dOpenFlow forwarding rulesNetwork – Traffic not sent to IDS– Traffic not sent to FirewallSciPass: Controller100G ThroughputimprovesNetwork100GSciPass: ControllerFeedback10GIDSOpenFlow ack10GIDSOpenFlow ork 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential3
Flow Detection Method IPS/IDS/FW/Router – Insert whitelist/ACL to match a packet with specific headerinformation Data Transfer Node (DTN) – Get a notification from DTN that is about to start adata transfer Globus – Get a notification from Globus or similar tools. 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential4
FW/IPS Bypass MethodsOption 1: Enable OpenFlow feature on Cisco OpenFlow Hybrid SwitchOption 2: Use a dedicated OpenFlow Switch if the current device doesn’tsupport OF.Option 3: Use PBR with NXAPI.Option 4: Use VACL and Redirect with NXAPI 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential5
How to Secure Science DMZ and CampusQ. Science DMZ is directly connected to the Internet. How can we secure ScienceDMZ and the campus?A. Leverage security devices to detect the threats and log threats to Event server,such as Splunk. Necessary actions against the threat are triggered by apps in theevent server, actions could be Blackholeling BGP routes on routers, or applyingOpenFlow rules on the OF switches, or both. 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential6
extGenera onFirewall Commodity:In- ‐Line Internet2:In- ‐LineorOOBw/SteeringOpenFlowNexus 3KBGPBGPNullRoutesHigh- ‐ThroughputScienceNetworksASR 1KASR AL2SNexus 9KFlowNo3ngfica3onDTN ASA 5585CorporateDCBlockiCampusEvent CorrelationLog StorageAuditingAnalysisExternalServices 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential7
Splunk as an SDN Application Logically sits on top of COSC to provide application intelligence Likely already sending events to central logging Has the most informed view of the status of the network, servers, and apps. Provides event correlation Consolidates the number of devices sending REST commands Correlates by severity, rate, and between events Provides for auditing and reporting capabilities Leverage existing skill by writing logic in Splunk search language 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential8
Example Event ActionsReal-Time, Immediate Action:From IDSe.g. High Priority IDS Event: Block Host ImmediatelyReal Time With Sliding Window and Threshold:e.g. SYN Attacks: Block host after 100 improper SYNs in 60 secondsFrom FWScheduled with Fixed Window:e.g. Block Timeout: Unblock host if it has not been seen in last 24 hours 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential99
Globus for Data Transfer A key service in the research networking ecosystem with more than 10,000 active endpoints Software-as-a-Service (SaaS) solution to manage transfers where users can direct requests totransfer or synchronize files and directories between two locations Uses GridFTP to provide secure, reliable, and efficient transfer of data across wide-area distributednetworks GridFTP extensions provides parallelism (i.e., the use of multiple socket connections between pairsof data movers), restart markers, and data channel security. GridFTP control plane provides the source and destination information for the flows it sets up Effectively authenticates flows before they bypass security 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential10
OpenFlow Data Flow SteeringBase setup depending on mode:Out-Of-Band IDS:Outside54 priority 100 /priority in-port 54 /in-port output-node-connector 52 /output-node-connector output-node-connector 25 /output-node-connector In-Band Firewall/IPS: priority 100 /priority in-port 54 /in-port output-node-connector 25 /output-node-connector in-port 25 /in-port output-node-connector 52 /output-node-connector Bypass operation the same for both modes2552InsideOut-Of-Band IDSOutside54 priority 200 /priority in-port 54 /in-port output-node-connector 52 /output-node-connector IDS25FW/IPS52InsideIn-Band FW/IPS 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential11
Bypass Flows in “Tap” SwitchFlow start notification:Jun 10 10:53:43 localhost splunk odl action: log level INFO, action start, flow 199.66.189.10:50368-128.55.29.41:42600,status code 200Flows added to Nexus 3000:Flow: 4Match:Actions:Priority:Flow: 5Match:Actions:Priority:tcp,in port 54,nw src 199.66.189.10,nw dst 128.55.29.41,tp src 50368,tp dst 42600output:52200tcp,in port 52,nw src 128.55.29.41,nw dst 199.66.189.10,tp src 42600,tp dst 50368output:54200Flow stop notification:Jun 10 10:54:51 localhost splunk odl action: log level INFO, action stop, flow 199.66.189.10:50368-128.55.29.41:42600,status code 200 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential12
Remotely Triggered Black Hole RoutingStatic routes added by COSC through Netconf on ASR 9000:router staticaddress-family ipv4 unicast1.0.184.115/32 Null0 tag 6661.161.169.139/32 Null0 tag 6662.25.74.127/32 Null0 tag 6662.50.153.67/32 Null0 tag 66612.197.32.116/32 Null0 tag 666Export the Null routes setting next-hop to black hole IP:route-policy as-11017-outif tag is 666 thenset next-hop 192.0.2.1set community (no-export) additivepasselseEnable uRPF on WAN interface on ASR 9000:ipv4 verify unicast source reachable-via any allow-defaultRoute Black Hole IP to NULL 0 on other borderrouters:ip route 192.0.2.1 255.255.255.255 Null0Enable uRPF on WAN interface on ASR 1000:ip verify unicast source reachable-via anypassendifend-policy 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential13
Cisco Open SDN ControllerApplication 1Application 2Application 3Application 4Application ‘n’NetworkApplicationsREST APIsDLux User InterfaceBASE NETWORK SERVICE viceL2 SwitchHostTracker3rd PARTY NETWORK SERVICE FUNCTIONSNetworkNetworkNetworkService 1Service 2Service 3GBPServiceNetworkService 4NetworkService ‘n’Cisco OpenSDN ControllerPlatformModel Driven Service Abstraction Layer(Plugin Manager, Capacity Abstraction, Flow Programming, Inventory, etc)OpenFlowInterfaceOpenFlow witchesBGPLSInterfacePCEPInterfaceCisco and 3rd Virtualand Physical DevicesData PlaneElements 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential14
Splunk Screenshot 1 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential15
Splunk Screenshot 2 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential16
Splunk Screenshot 3 2015 Cisco and/or its affiliates. All rights reserved. Cisco Confidential17
SDN SOLUTIONS SHOWCASE SciPass Operation - Phase 3 11 SciPass inserts bypass OpenFlow forwarding rules - Traffic not sent to IDS - Traffic not sent to Firewall Throughput improves OpenFlow Switch IDS IDS IDS IDS Network Network 100G SciPass: Controller 100G PerfSONAR 10G Feedback Firewall 10G 10G SDN Solutions Showcase, October 14 .