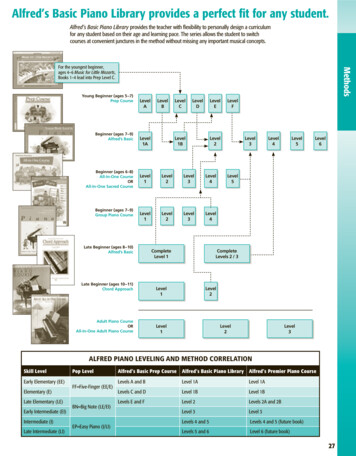
Transcription
Production Level Security inJBoss Enterprise ApplicationPlatform 6(JBoss EAP)
OUTLINE Introduction Enabling SSL Connector Securing Management Interfaces Configuring LoginModules Introduction To PicketLink SPNEGO
Introduction JBoss EAP 6 has several new features added to the securitysubsystemThe security subsystem provides the infrastructure for all securityfunctionality in the Enterprise Application Platform. The securitysubsystem can be configured in the managed domain or in thestandalone configuration file.The presentation would include small demos,which will help tounderstand how can we configure the security subystem foreg:configuring variuos authentication modules,configuringvaultsfor securing passwords,securing management interfaces,enablingencrypted communication(SSL) etc.
Enabling SSL Connector The example shows enabling 2-way SSLwhere server and client both need are requiredto present each other a certificate.For testing I have used self-signed certifiactes.
Enabling SSL Connector subsystem xmlns "urn:jboss:domain:web:1.2" default-virtualserver "default-host" native "false" connector name "http" protocol "HTTP/1.1" scheme "http"socket-binding "http"/ connector name "https" protocol "HTTP/1.1" scheme "https"socket-binding "https" secure "true" ssl key-alias "test"password ”password”certificate-key-file " icate-file " {jboss.server.config.dir}/trust.jks"protocol "TLSv1" verify-client "true"/ /connector
OUTLINE Introduction Enabling SSL Connector Using Vault to Encrypt Passwords Securing Management Interfaces Configuring LoginModules Intoduction to PicketLink SPNEGO
Enabling SSL Connector In order to get more details on SSL connectorattributes please refer the belowdocumentation JBoss Enterprise Application Platform/6/html/Administration and Configuration Guide/SSL Connector Reference1.html
Using Vault To Encrypt Passwords Web applications and other deployments often include clear-text files,such as XML deployment descriptors, which include sensitiveinformation such as passwords and other sensitive strings. JBossEAP 6 includes a password mechanism called as “Vault”The Vault enables us to encrypt sensitive strings and store them in anencrypted keystore. The vault mechanism manages decryption of thestrings for use with security domains, security realms, or otherverification systems. This provides anextra layer of security. The mechanism relies upon tools that areincluded in all supported JavaDevelopment Kit (JDK) implementations.
Initializing The Vault And StoringPasswords In order to initialize a vault and storepasswords we need to execute the vault.shscript which is present inside/home/jboss-eap-6.0/bin/vault.sh Prerequisites:1)keytool utility2)A Java keystore to store the strings
Using The Vault In JBoss Initializing the vault: vault vault-option name "KEYSTORE URL" value " {jboss.server.config.dir}/vault/vault.keystore"/ vault-option name "KEYSTORE PASSWORD" value "MASK3EqTGNvEUm2zBW9JGpulUT"/ vault-option name "KEYSTORE ALIAS" value "systemprop"/ vault-option name "SALT" value "jboss123"/ vault-option name "ITERATION COUNT" value "25"/ vault-option name "ENC FILE DIR" value " {jboss.server.config.dir}/vault/"/ /vault
Using The Encrypted Password Using the encrypted password in SSL connector connector name "https" protocol "HTTP/1.1"scheme "https" socket-binding "https" secure "true" ssl key-alias "test"password " Byb3A }"certificate-key-file " icate-file " {jboss.server.config.dir}/trust.jks"protocol "TLSv1" verify-client "true"/ /connector
Securing Management Interfaces The management interfaces are alreadysecured.We can still add up more by enabling themanagement console to be accessed overSSL and as well using an LDAP.
Securing Management Interfaces Enabling Management Console over SSL Securing Management Console with an LDAP
Securing Management Interfaces Enabling Management Console over SSL server-identities ssl keystore path "console.jks" relativeto "jboss.server.config.dir" keystorepassword "password" alias "console"/ /ssl /server-identities
Enabling Management Console overSSL We need to change the socket Binding as well socket-binding https "management-https"/
Securing Management Console withLDAP Creating an LDAP outbound connection outbound-connections ldap name "ldap connection"url "ldap://10.65.211.223:389"searchdn "cn testuser,cn Users,dc mydomain,dc com"search-credential "jboss@123" / /outbound-connections
Securing Management Console withLDAP security-realm name "TestRealm" server-identities ssl keystore path "console.jks" relative-to "jboss.server.config.dir" keystorepassword "password" alias "console"/ /ssl /server-identities authentication ldap connection "ldap connection" basedn "cn Users,dc mydomain,dc com" username-filter attribute "userPrincipalName" / /ldap /authentication /security-realm
Securing Management Console withLDAP Modify the following management-interfaces . http-interface security-realm "TestRealm" /management-interfaces
Configuring Various LoginModules Following is the list of few LoginModulessupported in EAP LoginModule
UserRolesLoginModule Following things need to be added1)In application's web.xml security-constraint . auth-constraint role-name JBossAdmin /role-name /auth-constraint /security-constraint security-role role-name JBossAdmin /role-name /security-role
UserRolesLoginModule2)Create users and roles files in EAP3)Add the security-domain to jboss-web.xmlfile security-domain java:/jaas/test /securitydomain
UserRolesLoginModule4)Add the following configuration to standalone.xml security-domain name "test" authentication login-module code "flag "required" module-option name "usersProperties" value ration/user.properties"/ module-option name "rolesProperties" value ration/roles.properties"/ /login-module /authentication /security-domain
Introduction To PicketlinkPicketLink Federation allows you to implement SAML v2.0 basedservices and applications. It also has support for Oasis WS-Trustbased applications.It has the following features: SAML v2 Web Browser SSO Support for JavaEE Web Container.SAML v2 Web Browser SSO (HTTP/Redirect Binding) Support for JBossApplication Server and Apache Tomcat.SAML v2 Web Browser SSO (HTTP/Redirect Binding) Support for JBossApplication Server and Apache Tomcat with XML Signature Support.SAML v2 Web Browser SSO (HTTP/POST Binding) Support for JBossApplication Server and Apache TomcatSAML v2 Web Browser SSO (HTTP/POST Binding) Support for JBossApplication Server and Apache TomcatSAML v2 Global LogOut.
QuickStart Examples. The Documentation for the same is tLink QuickstartsYou can download the required QuickStart Packages nexus-search;quick picketlink-quickstartsYou can download the PicketLink jar “picketlink-core-2.1.6.Final.jar” nal/ You can download the latest picketlink binding jar "picketlink-jbas7-2.1.6.Final.jar" -jbas7/
QuickStart Examples.Configuring, Deploying and Running the Applications: Download the picketlink-core-2.1.6.Final.jar, picketlink-jbas7-2.1.6.Final.jar.In EAP 6, go to main and place the above twomentioned files in the main directory.Now replace the entries in the module.xml file with the new jar files as follows: resources resource-root path "picketlink-as7-extension-1.0.1.Final.jar"/ resource-root path "picketlink-jbas7-2.1.6.Final.jar"/ !-- new entry -- resource-root path "picketlink-core-2.1.6.Final.jar"/ !-- new entry -- /resources Now, we would need to add the security domains for IDP and SP in the standalone.xml(or a copy ofit) file as follows :
security-domains security-domain name "idp" cache-type "default" authentication login-module code "UsersRoles" flag "required" module-option name "usersProperties" value "users.properties" / module-option name "rolesProperties" value "roles.properties" / /login-module /authentication /security-domain security-domain name "picketlink-sts" cache-type "default" authentication login-module code "UsersRoles" flag "required" module-option name "usersProperties" value "users.properties" / module-option name "rolesProperties" value "roles.properties" / /login-module /authentication /security-domain security-domain name "sp" cache-type "default" authentication login-module code .auth.SAML2LoginModule" flag "required"/ /authentication /security-domain . security-domains
DeskTop SSO:Kerberos If the user runs the application from a systemwhich is already logged into the directory service, andwhere the required roles are already applied to the user,the web application does not prompt for authentication,and SSO capabilities are achieved. The LoginModules arecom.sun.security.auth.module.Krb5LoginModule inModule
JBoss EAP 6 has several new features added to the security subsystem The security subsystem provides the infrastructure for all security functionality in the Enterprise Application Platform. The security subsystem can be configured in the managed domain or in the standalone configuration file.