Transcription
BridgingthedatagapCyber crisisin the insurance industrymanagement:Readiness, response,and recoveryStrategic & Reputation Risk
Readiness,response,and recoveryHacked devices, crashed websites, breachednetworks, denials of service, copied emails,stolen credit card data, and other cyberincidents have become commonplace. It’senough to leave one thinking—correctly—that no organization can achieve totallyassured cybersecurity.1Most organizations have therefore developedsome level of cyber incidence response (CIR)capabilities. Yet those capabilities, which areoften weighted toward short-term responsesand IT issues, may fail to address all impactsof a cyber incident and keep it from reachingcrisis proportions.Avoiding a cyber crisis often comes down toproperly managing a cyber incident before,during, and after it unfolds. This starts witha broad view of cyber crisis management.Executives often see cyber incidents as“an IT issue,” when IT is only one domaininvolved. Forward-thinking managementteams recognize that effective crisis planninginvolves multiple functions and skill sets.They also recognize that these must behighly coordinated if an incident is to becontained or, if an incident does escalate tocrisis levels, managed.Cyber crisis management Readiness, response, and recovery
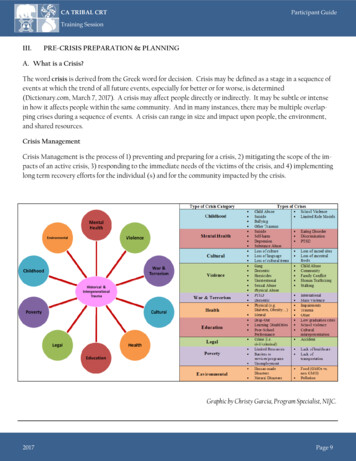
The need forcrisis planningCBS.com notes that 1.5 million cyberattacksoccur every year, which translates to over4,000 attacks every day, 170 every hour,or nearly three every minute.1 While fewattacks succeed, the high probability of cyberincidents dictates that every organizationneeds to be prepared to respond effectively.Effective preparation addresses the entirecrisis management lifecycle of readiness,response, and recovery (see Exhibit 1).Each phase of this lifecycle presentsopportunities to protect the organizationfrom risks, costs, and damage emanatingfrom an incident—and to strengthen theorganization’s defenses going forward:1ReadinessReadiness equates not only to vigilance, forexample in the form of 24/7 Monitoring,but also to readiness of resources. A wellprepared, multifunctional team must bepoised to deal with all aspects of an incidentor crisis. In addition, crisis simulation and wargaming enables management to understandwhat can happen, which steps to take, andwhether the organization is truly prepared.ResponseManagement’s response can either containor escalate an incident; indeed, a poorresponse can even create a crisis. Vigorous,coordinated responses to incidents limitlost time, money, and customers, as wellas damage to reputation and the costs ofrecovery. Management must be prepared tocommunicate, as needed, across all media,including social media, in ways that assurestakeholders that the organization’s responseis equal to the situation. BS News, These cybercrime statistics will make you think twice aboutCyour password: Where’s the CSI cyber team when you need them?2Cyber crisis management Readiness, response, and recovery
crises pose to reputation, brand, operations,and customer and supplier relationships willcontinue to increase, as will the associatedlegal and financial effects.No board of directors or senior executiveteam can credibly deny the seriousnessor the likelihood of cyberthreats. So, thetime to prepare a highly effective cybercrisis management plan is before a cyberincident occurs.Exhibit 1Deloitte’s crisis management lifecycleEffective crisis management extendsbeyond preparing for any specific event todevelopment of broad, flexible capabilities thatenable response to a wide range of eventsalong various dimensions. From the standpointof cybersecurity—the main deterrent to cyberincidents—the goal is to develop a secure,vigilant, and resilient organization.ReadinessResponseRecoveryCRISIS COMMUNICATIONSSTRATEGIC RISK/CRISIS MANAGEMENTPLANNINGIT and digital assets now drive a hugeportion of enterprise value. Knowing this andunderstanding system vulnerabilities, attackerstarget organizations repeatedly and fromvarious angles. Therefore, the risk that cyberCRISIS TRIGGER*RecoverySteps to return to normal operations andlimit damage to the organization and itsstakeholders continue after the incident orcrisis. Post-event steps include assessmentsof the causes and of the management ofthe incident or crisis, and promulgation oflessons MULATIONREAL-TIME RESPONSE24/7 MONITORING*cyberattacks natural disasters misdeeds and financial crimes financial disruptions industrial accidents civil or political unrest3Cyber crisis management Readiness, response, and recovery
Secure, vigilant, and resilientIn pursuing cybersecurity, an organization should strive to become:SecureA secure organization prioritizes the value of digitalassets, with a focus on what matters most to theorganization. All data is not created equal, nor is itpractical or possible to provide complete security forall data. By prioritizing the value of digital assets,management can allocate resources according tothe value of the assets, with the goal of obtaining alevel of security that corresponds to their value.VigilantVigilance demands that everyone be aware of howthey could expose the organization to cyber riskthrough their devices, social media, and onlineconduct. A vigilant approach rests on gatheringthreat-related intelligence and gauging the rangeof threats that could harm the organization. Thisinformation also informs cyberthreat monitoring.In addition, policy development, training, andaccountability regarding cyber incidents each play akey role in maintaining vigilance.4Cyber crisis management Readiness, response, and recoveryResilientA resilient organization aims to minimize the impactof an incident on its stakeholders while quicklyrestoring operations, credibility, and security. Rapiddetection of cyber incidents and well-structuredrecovery plans can usually limit damage. Recoveryplans should designate clear roles, responsibilities,and actions to mitigate damage and reduce futurerisk, remediate the situation, and return to normaloperations.A secure, vigilant, resilient organization has all threephases of cyber risk management covered. Deloittestrives for this state as an organization and hasorganized cyber risk services to enable clients to dothe same.
While the precise nature, location, and impactof incidents cannot be predicted, the incidentresponse lifecycle follows a predictable path(see Exhibit 2).The CIR lifecycle illustrates the interplaybetween organizational capabilities andstakeholder confidence. Immediately afteran incident, affected capabilities must berestored. This usually takes hours or days,but can take weeks or months in severecases. Also, cybersecurity must be enhancedto secure the environment, improve visibilityinto threats, and reduce the impact offuture incidents.Containing an incident and avoiding a crisiscalls for proactively addressing stakeholderconcerns. Customers usually express concernregarding loss of personal data and privacyand may develop long-term brand aversion.Exhibit 2Cyber incident response lifecycleHIGHLOWMONITORINGOngoingConsumer confidence5Business partners are concerned about nearterm cross-contamination of their systemsand the longer-term integrity of data andtransactions. Employees may be overwhelmedby negative publicity and increased stress.Regulators want assurance regardingconsumer protection, and the state of thebusiness and industry. Investors are attunedto short-term financial impacts and longerterm business and brand viability.CRISISThe cyber incidentresponse lifecycleCyber crisis management Readiness, response, and recoverySHORT-TERMHours – Days – WeeksRegulatory confidenceINTERMEDIATEWeeks – MonthsInternal confidenceBusiness andoperational capabilitiesLONG-TERMMonths – YearsCyber risk capabilities
Over the course of the response lifecycle, crisiscommunications stand among the highestpriorities. Specifically, the organization must: Respond to a high volume of requestsfrom customers, business partners,vendors, regulators, law enforcement, andthe board of directors Manage requests from business partnersto modify arrangements, processes, andmethods of sharing information Engage in proactive messaging to thebroader base of stakeholders and thepublic regarding what is known and notknown, and what the organization is doing Monitor and address traditional, webbased, and social media reactions to theevent and to the organization’s responseand intentions6In addition, management must: Address any potential threat of legalor regulatory action, and determinewhat legal recourse is available to theorganization Minimize the time between developingand implementing the remediation plan,while also managing the risks generated inthat interimThe more comprehensive and tested theplan, the better management’s response toan incident will be. Yet management shouldunderstand that the plan does not representa script that will play out in reality and thatresponses must be flexible and fluid. You mayhave to depart from the plan, but the planwill provide a framework and guidance forcoordinating the diverse elements involved inthe response.Cyber crisis management Readiness, response, and recoveryGetting coordinatedCyber incident response programs requirecoordination in six key areas: governance,strategy, technology, business operations,risk and compliance, and remediation.1GovernanceGovernance frames the wayyou organize and manageyour response team. It ensuresprogram coordination across functional areas,documentation of all policies, procedures,and incidents, and clear communication roles,responsibilities, and protocols. Governancealigns response strategy with goals andprovides mechanisms for cross-functionalcommunication.
Key steps in establishing governance forresponse management include: Segregating duties by establishing anindependent investigation team to helpdetermine causes and remediation steps Considering the role of legal counsel,who should be on or represented on theresponse team, which should be led bya business manager (to foster a crossfunctional approach to CIR) Defining incident response and recoverylifecycle phases and a decision frameworkwith clear steps and measures of successKey questions Do we have the right team in place? What should be reported, to whom,and when? Are we periodically testing our planand training our staff? How are we incorporatinglessons learned?7Exhibit 3Cross-functional capabilities required for effective responseGovernanceIncident response cross-functional coordination,documentation, and stakeholder communicationStrategyOrganizationalstrategy in dealingwith cyber incident,including executive,board, and customercommunicationCyber crisis management Readiness, response, and recoveryTechnologyTechnical IncidenceResponse, forensics,malware analysis, loganalysis, and IToperations supportBusinessOperationsOperational resilienceduring cyber incidentsthrough Integratedbusiness continuityand disaster recoveryprocesses and proactivecommunicationsRemediationRemediation of incident root causeand associated business processesRisk &ComplianceRisk and compliancemanagement,including interfacingwith regulators, legalcounsel, and lawenforcement
2StrategyResponse strategy defineshow you lead, prioritize,and communicate duringincident response and crisis management.Organizations should align response strategywith the organization’s responsibilities andvalues. A sound strategy frames a costeffective, well-resourced, organization-wideapproach to addressing cyber incidents. Thisminimizes “tunnel vision” in response planningand reduces adverse impact to operationsand revenue.8Key aspects of response strategy include: Defining escalation and prioritizationprocesses to manage and coordinate IT,operational, and business recovery Engaging the organization’s governmentaffairs team or other government liaisonfunction to inform and work withregulatory agencies and any appropriateofficials—an essential step in anyregulated industry Aligning response efforts with securitymanagement and IT engineering initiativesKey questions When should the C-suite and boardbe informed? Does our strategy address internaland external coordination? How will we assist affected stakeholders? What are the best communicationchannels?Cyber crisis management Readiness, response, and recovery3TechnologyThe IT and cybersecurityteams develop and implementmechanisms for detecting,monitoring, responding to, and recoveringfrom a cyber incident or crisis. IT engineerscreate the needed architecture, and ITworks to maintain systems that are resistantto attacks.Technical forensic and investigative capabilitiesare vital to preserving evidence and analyzingcontrol failures, security lapses, and otherconditions related to the incident (see sidebar:After an incident: Investigation and response).In addition, organizations should implementboth proactive and responsive technologysolutions to mitigate future cyber incidents.
Key steps in framing the technologyaspects of incident response include: Being realistic about IT tools, which enablesecurity and operational capabilities, butdo not eliminate risk Resolving the tension between immediateneeds in the wake of an incident andlonger-term remedies Accepting that workarounds and throwaway work are often necessary to meetnear-term prioritiesAfter an incident: Investigation and responseKey questions Which incident and crisis mitigationtechniques are we employing? What technical capabilities do we have,and what are we missing? Do we have access to forensic resources? How are we gathering and using threatintelligence?In general, the following steps to address a cyberincident can assist in identifying causes andremedies, and hasten recovery:9Think of a digital crime scene as you would a physical crime scene: trampling evidence or cleaning things upcan make forensic tasks difficult to impossible. So, the team should start by securing the digital crime sceneand preserving evidence.However, saving the “victim”—a damaged orcompromised system required to run a process orbusiness—may also be a priority. That “victim” mayrequire first aid when the recovery strategy calls forrestoring the same system as quickly as possible.In such cases, the business needs to balance thatdecision and associated activities against the needto preserve evidence for analysis. Document how the incident came to light,who reported it, and how they were alerted;interview IT staff and other relevant parties Consider and research the possibility of insiderinvolvement and take steps to minimize this riskgoing forward Identify affected systems and isolate them so noone attempts to fix, patch, or alter the state ofthe systemsCyber crisis management Readiness, response, and recovery Gather all available evidence and analyze it todetermine cause, severity, and impact of theincident Strengthen network security, improve protocols,and increase vigilance as indicated by theanalysis Enhance monitoring and other measures tomitigate future risk of similar incidents andenhance policies that may increase security Document and report the findings to anyrelevant stakeholders and consider potentialrequirements to report the incident to aregulatory bodyWithout an effective investigative response, thecauses of the incident may never be understood,and the risk of a repeat incident may actuallyincrease. Speed is essential to limiting damage afteran incident. For example, for insurance purposesimmediate response can result in more accurate lossmeasurement and claim quantification, and fastersettlement of a claim.
4Business operationsAfter an incident, critical businessoperations must resume as soonas possible to minimize disruptionsthat generate financial, reputational,regulatory, and stakeholder impacts.Keys to minimizing businessdisruption include: Implementing out-of-band processes toreplace those that are broken or thatpresent too many constraints duringincident response or to remediation Planning for surge support and allocatingresources accordingly Understanding existing business limitations,such as the risks associated with usingstandard payments systems or certainapplicationsKey questions Which business processes and applicationsare most critical to operations? What infrastructure must be given thegreatest protection? How will we go about returning tofull operations? How can staff, suppliers, and partnerssupport recovery?5Risk and complianceRisk and compliance functionsshould assess and manage theregulatory compliance elementsof incident and crisis response, includinginterfacing with legal counsel, regulators,and law enforcement. The keys are to beable to comply with requirements and todemonstrate compliance. For example,after an incident, investigative processesand responses must be documented todemonstrate the adequacy of both.10 Cyber crisis management Readiness, response, and recoveryKeys to successful managementof risk and compliance after anincident include: Anticipating requests from regulatorsand law enforcement, which may includerequests for access to systems and areview of response activity Analyzing the impacts and loss exposuresfor insurance and other reporting purposes Understanding any additional risks broughtabout by ad hoc processes, technology,and work-arounds required duringincident responseKey questions What are the breach notificationrequirements? What are the regulatory and third-partyobligations? When and how do we inform lawenforcement? How could this particular incident—or a pattern of incidents—impact theorganization’s compliance posture?
Five lessons in crisismanagement6RemediationRemediation begins after criticalbusiness operations resume, withshort- and long-term efforts toclose gaps. The organization must verifythat attack vectors are eradicated and takesteps to prevent similar attacks in the future.Remediation must eliminate or minimize rootcauses of incidents and return businesses,functions, IT, and stakeholders to a secureoperating environment.Keys to successful remediation include: Balancing the inclination to securedigital assets against the need to dobusiness seamlessly Prioritizing the influx of technology projectrequests and increased IT budgetary needs Preparing for increased regulatoryscrutiny and a potentially more rigorousregulatory regimeKey questions Have the IT and business-process rootcauses been identified? Has a remediation plan been developed? Have the root causes been eliminated orminimized? What are the lessons learned and how canwe apply them?The response team should include individualsfrom each of the above six areas to develop awell-resourced, balanced, consistent approachto cyber incidents and cyber crises across theorganization.11Cyber crisis management Readiness, response, and recoveryDeloitte’s work in crisis managementwith senior executive teams has yielded thefollowing lessons:1 There’s no substitute for preparedness. Wargaming, rehearsals, and other structuredpreparations do much to position theorganization to launch a coordinated response.2 Every decision counts. In a crisis every decision can affect stakeholdervalue mainly through heightened reputationalrisks, which can destroy value faster thanoperational risks.3 Response times should be in minutes. Teams on the ground must respond rapidly, notin hours or days. They must take control, leadwith flexibility, act on incomplete information,communicate well, and inspire confidence.4 When the crisis has passed, work remains. After breathing a sigh of relief, you must capturedata, log decisions, manage finances, handleinsurance claims, and meet legal and regulatoryrequirements.5 You can emerge stronger. Almost every crisis creates opportunities foran organization to shine, first, by respondingeffectively and, second, by searching outopportunities to improve.Customers, suppliers, employees, and otherstakeholders understand that crises will occasionallyaffect the organization. What they find hard tounderstand are lack of preparation, inadequateresponses, and confusing communications on thepart of management.
Are you ready?Most organizations will lack the resourcesto develop and maintain all necessaryincident and crisis response capabilitiesin-house. The expertise required, theevolving risk landscape, and the resourcesof cybercriminals render it impractical formost organizations to go it alone. Thus, anoutsourced or co-sourced approach witha provider of managed cybersecurity andresponse services may be the best option formost organizations.Leveraging cyberthreat intelligencecapabilities, for example via sharing withindustry peers or outsourcing to specialistswill make sense for many organizations. Manywill also benefit from external support indeveloping and maintaining cyber monitoringand cyber risk management programs.For example, 24/7 Monitoring can provideearly warnings of cyberthreats and risk sensingcan detect patterns of criminal activity, butwould not be economically viable for mostorganizations to develop on their own. By thesame token, objective verification of readiness,response, and recovery plans, by meansof crisis simulation, wargaming, and otherassessments, can detect gaps and weaknessesin those plans.When it comes to incident and crisismanagement, readiness is an evolutionarystate. What you were ready for yesterday maybe the last thing cybercriminals have in mindtoday. Indeed, you cannot really know thespecific source or target of the next attack. Butyou can gauge risks based on the value of yourdigital assets and the impact of their beingcompromised. You can gauge likelihood. Andyou can ready the organization for effectiveresponse and recovery.12 Cyber crisis management Readiness, response, and recoveryLet’s talkFor more information, please contactyour local crisis management leaderwww.deloitte.com/crisiscontacts
Deloitte refers to one or more of Deloitte Touche Tohmatsu Limited, a UK private company limited by guarantee (“DTTL”), its network of member firms,and their related entities. DTTL and each of its member firms are legally separate and independent entities. DTTL (also referred to as “Deloitte Global”)does not provide services to clients. Please see www.deloitte.com/about for a more detailed description of DTTL and its member firms.Deloitte provides audit, consulting, financial advisory, risk management, tax and related services to public and private clients spanning multipleindustries. Deloitte serves four out of five Fortune Global 500 companies through a globally connected network of member firms in more than 150countries bringing world-class capabilities, insights, and high-quality service to address clients’ most complex business challenges. To learn more abouthow Deloitte’s approximately 225,000 professionals make an impact that matters, please connect with us on Facebook, LinkedIn, or Twitter.This communication contains general information only, and none of Deloitte Touche Tohmatsu Limited, its member firms, or their related entities(collectively, the “Deloitte Network”) is, by means of this communication, rendering professional advice or services. Before making any decision ortaking any action that may affect your finances or your business, you should consult a qualified professional adviser. No entity in the Deloitte Networkshall be responsible for any loss whatsoever sustained by any person who relies on this communication. 2016. For information, contact Deloitte Touche Tohmatsu Limited.
3 Cyber crisis management Readiness, response, and recovery Recovery Steps to return to normal operations and limit damage to the organization and its stakeholders continue after the incident or crisis. Post-event steps include assessments of the causes and of the management of the incident or crisis, and promulgation of lessons learned.