Transcription
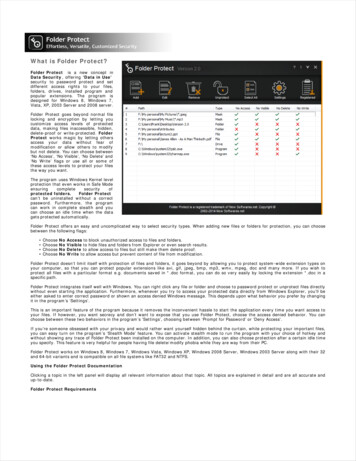
WHITE PAPERIntel Core vPro ProcessorsEndpoint EncryptionProtect Your Company’s Data withEfficient Encryption and SecureRemote ManagementIntegrated hardware-software solutions from Intel and McAfee help you keep remote PCs and data safer with acceleratedencryption and secure remote access to PCs powered by Intel Core vPro processors.1One of the top sales representatives from your company has just left a sales call inanother city. She walks into a crowded downtown coffee shop, puts her laptop bag downon the floor while paying for her coffee, and then walks out without the laptop. Later thatsame day, a user in a remote office calls IT because his computer is infected with malwareand won’t start properly. And yet another user calls because he’s forgotten his password.Sound familiar? You’re not alone.Companies are relying more and more ona highly mobile workforce. By 2015, theworld’s mobile worker population will reach1.3 billion, representing 37.2 percent of thetotal workforce, according to a study byIDC.2 But as companies become increasinglymobile, the risks of losing data from lost orstolen laptops will continue to grow, makingit increasingly difficult for organizationsto meet internal and regulatory securitycompliance requirements.IT administrators need an effectiveway to protect laptops and keep datasecure without dragging down userproductivity. But those same protectionsalso need to extend to files, folders, andremovable drives in order to secure datain all locations and forms—whether atrest or in motion—to better protect theorganization and meet government andindustry compliance mandates.Administrators and support staff alsoneed to ensure that PCs—regardlessof their location in the world—are keptup to date with operating system andsecurity updates, in addition to driverand application patches. And in worstcase situations where problems ariseor malware takes hold of a system,administrators need an effective way tosupport the remote system and remediatethe threat quickly, without the high costsand lost productivity incurred from onsite visits or shipping remote PCs back tocorporate headquarters.Improve Data Protection and SimplifySecurity ManagementMost of the device management andsecurity solutions available today requirepiecing together software and hardwarecomponents from multiple vendors.
Secure Your Endpoints and DataThese fragmented solutions can bedifficult and costly to configure, manage,and support and can leave risky gaps inyour overall security posture.Intel and McAfee (a wholly ownedsubsidiary of Intel) have collaboratedto create a unique, integrated solution:strong, hardware-enhanced securityfeatures integrated with comprehensivesecurity management software. Thejoint solution is built around PCs andUltrabook devices powered by Intel Core vPro processors. McAfee EndpointEncryption software takes advantageof the hardware-enhanced encryptionprovided by Intel Advanced EncryptionStandard New Instructions (Intel AES-NI)to deliver strong, efficient protection foryour computer drives, files, folders, andeven removable media, including USBdrives, CDs, and DVDs.3 When combinedwith McAfee ePolicy Orchestrator (McAfee ePO ) Deep Command, the resultis a comprehensive solution that deliversfull control of remote PCs for out-of-bandpatch management, problem remediation,update distribution, and password resets—all with secure, pre-boot connectivity froma single management console.By using innovative, integrated solutionsfrom Intel and McAfee, you can reducecomplexity and effort for your IT supportstaff, minimize downtime caused bymalware remediation, and lower energycosts by remotely starting PCs forscheduled updates during non-peak hours.At the same time, the joint solution canhelp increase security, energy efficiency,productivity, and compliance, whichcan make you a hero to your cost- andreputation-conscious CIO.2Intel AES-NIINTEL ADVANCED ENCRYPTION STANDARD NEW INSTRUCTIONSEncryption UsesEncryption ProcessAESTraditional software-based AESalgorithms are compute intensive.Data in FlightData at RestIntel AES-NIData in ApplicationHardware instructions reduceCPU cycles for each round.Figure 1: Intel AES-NI accelerates encryption for efficient protections with faster performanceAccelerate Encryption for Drives,Folders, and FilesEncryption is at the heart of a completeendpoint security solution. When yousafeguard the data, you reduce the riskof compromising sensitive customeror employee information, confidentialfiles, and your company’s reputation.According to a recent study by Gartner,“The encryption of information storedon endpoints is one of the mosteffective security controls to protectstored information from unauthorizedaccess, especially when devices arelost or stolen.”4 Unfortunately, manyorganizations are hesitant to widely deployencryption because it can significantlyimpair performance. Advanced EncryptionStandard (AES), for example, has beenused worldwide for years as a highlyeffective solution for protecting data,but the AES encrypting and decryptingoperations can be resource intensive.In response to this challenge, Intel hasdeveloped Intel AES-NI, an instructionset found in Intel Core processors andlatest-generation Intel Atom processorsthat increases encryption and decryptionperformance and reduces processor load.As shown in Figure 1, by implementingsome intensive substeps of the AESalgorithm into the hardware,
Secure Your Endpoints and DataIntel AES-NI accelerates execution ofthe AES application, while also reducingvulnerability to side-channel attacks.When you deploy McAfee EndpointEncryption solutions to devices poweredby Intel Core processors, you automaticallyprovide your users with strong, hardwareenhanced encryption from Intel AES-NIwith minimal performance impact and noadditional configuration effort. You canachieve even greater performance gainsby combining Intel AES-NI acceleratedencryption with high-performance,reliable, and efficient Intel Solid-StateDrives (SSD). Intel SSDs are ideal forachieving top performance with theadvantages of enhanced encryption.Intel AES-NI eliminates barriers towidespread adoption of encryptionby significantly reducing performancebottlenecks—especially when paired withefficient Intel SSDs. By applying strongencryption to drives, files, folders, andremovable media, you can better protectyour company assets at rest or in motion.Enjoy Stronger, HardwareBased EncryptionEncryption relies on strong cryptographickeys for security. Most encryptionproducts create those keys usingsoftware-based random numbergenerators (RNGs). Keys generated withRNG protocols can be more vulnerable toattack due to predictable or poor qualityrandom numbers. McAfee EndpointEncryption takes a different approachfor generating stronger cryptographickeys. The solution relies on Intel SecureKey Technology: a digital random numbergenerator that creates more secure, trulyrandom numbers directly on the processorchip.5 This hardware-based processgreatly strengthens encryption algorithmsto keep your data safer.Deploy and Manage Encryption AcrossYour EndpointsWith McAfee Endpoint Encryption,you can maintain productivity whileconfidently protecting data stored onoffice desktop PCs, remote PCs andUltrabook devices, and even on sharednetwork files and removable USB storagedevices. And because it’s fully integratedwith the McAfee ePO console, you cancentrally manage deployments, policyadministration, password recovery,monitoring, reporting, and auditing forconsistent protection and lower total costof ownership (TCO).Simplify Activation of New DevicesMcAfee Endpoint Encryption includes newfeatures that make it easier to identifyand activate compatible devices. With theoffline activation feature, you can installMcAfee Endpoint Encryption, apply apreconfigured policy, and encrypt a devicethat does not currently have a connectionto McAfee ePO. Any machine activatedwhile offline is essentially unmanaged,until it is connected to a network whereit can communicate with the McAfee ePOserver. Once communication with McAfeeePO has been established, the machinemoves into a managed mode.Another new feature, pre-boot smartcheck, tests your pre-boot environmentto verify it will work as expected. Anadministrator can specify that a devicecannot be activated and encrypteduntil it has passed a test sequencethat determines and confirms aworking configuration for a pre-bootenvironment. If no viable configurationcan be determined, the test fails withoutinstalling pre-boot or encrypting the drive,and it reports the failed status to McAfeeePO for an administrator to remediate.By quickly and automatically checkingsystems prior to deployment,administrators can easily determine thestatus of new devices attempting to jointhe network, regardless of those devices’locations. This benefit is particularlyuseful in a bring-your-own-device (BYOD)environment and can result in significantsavings in time and support costs.Securely Manage Remote PCsStrong, efficient encryption adds a criticallayer of protection for your assets, butyou still need to provide updates, applypatches, and enforce policies to yourendpoints. And unfortunately, there aretimes when you need to touch individualdevices for remediation of softwareproblems, removal of malware, or even asimple password reset.With mobile or remote users acrossmultiple locations, it can be difficult tokeep systems up to date with the latestpatches and drivers. And when a problemor malware strikes, it can be difficultand costly to troubleshoot or repair aremote PC. Typically you’d need to senda technician on site or have the affectedusers send in their computer, which canbe risky, time-consuming, and costly fromshipping expenses and lost productivity.Even worse, your affected users mightdelay addressing the issue while they’reunder pressure to make a sale or completea project, which can increase the risk orlead to more catastrophic problems ifmalware is present.Security can’t sacrifice productivity orefficiency, either. To keep from disruptingusers, you need to install patches andmanage security during off hours. But thatcan be difficult if your organization powersdown idle machines to cut energy costs.3
Secure Your Endpoints and DataWith McAfee ePO Deep Command, you canmonitor and control remote endpoints atthe hardware level, even if the device ispowered off, disabled, or encrypted. Fromone central control panel, you can enforcesecurity and compliance policies, deploypower management programs to conserveenergy, and remediate unresponsive PCs.McAfee ePO Deep Command uses Intel Active Management Technology (Intel AMT), found in systems powered by IntelCore vPro processors, to access endpointswithout relying on the operating system.6By accessing McAfee ePO Deep Commandentirely through the simple, comprehensiveMcAfee ePO control panel, administratorscan schedule policies to power on groupsof remote systems, execute security tasks,and then return the endpoints to theirprevious power states. Intel AMT alsoprovides centralized remote keyboard,video, and mouse (KVM) controls and bootredirection. Through the power of IntelAMT, you can even securely initiate theboot process and unlock endpoints runningMcAfee Endpoint Encryption in order toconduct remote security tasks without theneed for user authentication.Remediate Disabled EndpointsIntel AMT integration with McAfeeEndpoint Encryption and McAfee ePODeep Command can significantly reduceremediation costs by allowing a helpdesk technician to remotely repair aPC anywhere in the world through anetwork connection. Users with disabledPCs don’t have to wait for a personal,off-site visit because administratorscan quickly and conveniently remediateproblems or restore infected systemsfrom a central location.4By using the McAfee KVM Viewer, youcan securely and fully control a remotePC’s keyboard, video, and mouse togreatly simplify remediation. With McAfeeePO Deep Command communicatingdirectly to the hardware, you can controlthe remote PC through power cyclesand operating system reboots withoutbreaking the connection.By providing centralized, secureremediation and management ofendpoints, McAfee ePO Deep Commandhelps you reduce support, remediation,and maintenance costs, strengthen yoursecurity posture, and maintain efficiencyand productivity for your users.Schedule Off-Hours Patching andPower Management with Secure,Remote Pre-BootMcAfee ePO Deep Command allows you toconnect to remote computers to conductsecurity maintenance or time-intensiveupdates during off hours, when users willnot be disrupted.In the past, the primary way to wake PCsremotely was by using the wake-on-LANfeature, where a wakeup call was sentto the network card and passed on tothe PC. But this method would leave thePC stuck at the pre-boot authenticationscreen, requiring a user at the remotelocation to authenticate.Today, McAfee ePO Deep Command andIntel AMT simplify the remote connectionprocess and enable secure remoteaccess—even to encrypted PCs. McAfeeePO Deep Command initiates the processwith a wake request to the client, whichwill then contact McAfee ePO DeepCommand to request permission to boot.Intel vPro TechnologyBuilt-in security for greaterprotectionToday’s rapidly evolving businessenvironment is creating a new setof security challenges. To quicklyrespond to these challenges andstay ahead of high-level securitythreats, businesses need acomprehensive suite of securitysolutions that address critical areasof IT security.Intel vPro technology is a setof security and manageabilitycapabilities built into the Intel Core vPro processor family.Intel Active ManagementTechnology (Intel AMT) enablesIntel vPro technology capabilitiesto be accessed and administeredseparately from the harddrive, operating system, andsoftware applications—in a preboot environment. This makesmanagement less susceptible toissues affecting these areas andallows remote access to the PC,regardless of the system’s powerstate or operating system condition.Intel vPro technology alsoaccelerates data encryption/decryption using Intel Advanced Encryption StandardNew Instructions (Intel AES-NI),which can encrypt data up tofour times faster than standardencryption without interferingwith user productivity.
Secure Your Endpoints and DataBased on configured policies, McAfee ePOwill deny or allow the request. If McAfeeePO sends a denial or can’t be reached, theclient will remain at the pre-boot screenand will not start the operating systemwithout authentication from a user. IfMcAfee ePO approves the request, it willalso return cryptographic information toMcAfee Endpoint Encryption to unlock preboot securely and allow the PC to startthe operating system.the password to a one-time passwordthat is sent to the remote PC using IntelAMT. The user can authenticate with theone-time password, and then immediatelychange it to a new one. With remotepassword reset, a distracting, timeconsuming task can now be completed inlittle more than the time it takes your userto call IT for help.Once the connection is establishedand authenticated, you can securelypatch, reset user passwords, or performremote remediation. With the integratedcapabilities of McAfee ePO DeepCommand, Intel AMT, and McAfee EndpointEncryption, routine scans, updates, andother tasks can be scheduled for individualPCs, groups of PCs, or all computersin your enterprise, regardless of theirlocation or operating system state, evenif they are encrypted. The secure wakeand sleep capabilities also allow you toimplement energy savings programsfor your business and pursue industryincentives to cut power consumptionwithout compromising security.If you need to support shared computersin areas such as office meeting rooms orhospitals, you know how difficult it can befor different users to log on each time theyneed access. The joint Intel and McAfeesolution includes a location-aware pre-bootoption that enables a PC to boot directlyinto the operating system seeminglywithout a pre-boot environment, whilestill retaining the protections a pre-bootenvironment provides. This configuration isalso useful for streamlining authenticationin an office when a managed device is onthe internal, corporate network. When thePC is in the office, there is no need to showthe pre-boot. But as soon as it leaves theoffice for an insecure area, the user will berequired to authenticate normally.Securely Reset PasswordsImagine that one of your remote userscomes back from a two week vacationand discovers she can’t remember herpassword. She’s now stuck in pre-bootmode, calling the IT administrator for help.In the past, she’d have to call from thecomputer, exchange a 16-character stringwith the help desk, and hope neitherperson misreads or mistypes a character.With McAfee Endpoint Encryption, theadministrator can easily locate the user inthe McAfee ePO console and changeConfigure PCs to Boot AutomaticallyBased on LocationWhen a device is configured for locationaware pre-boot, it reaches out to McAfeeePO during startup and asks for bootpermission. If a positive response isreceived, it simply boots into the operatingsystem. However, if the device cannotreach McAfee ePO or is not on an allowednetwork location, it will automatically showthe pre-boot authentication environment.This unique feature combines convenienceand usability with the secure protectionsof the pre-boot environment.Powerful, Secure RemoteAccess from Intel ActiveManagement Technology(Intel AMT)Intel AMT allows IT or managedservice providers to better discover,repair, and protect their networkedcomputing assets by usingintegrated platform capabilities andpopular third-party managementand security applications. Intel AMTenables IT to remotely diagnoseand repair PCs, ultimately loweringIT support costs.Intel AMT is a feature of Intel Core processors with Intel vPro technology.Simplify and Unify Your EnterpriseSecurity Management and ReportingMcAfee ePO provides a softwaremanagement framework that is capableof scaling to hundreds of thousands ofendpoints. Designed to support distributedarchitectures and security managementteams, McAfee ePO software provides aunified security policy management andreporting environment for your entireMcAfee security infrastructure. Now, bytaking advantage of Intel AMT capabilities,it can take your policies and complianceinitiatives beyond the operating system. Byextending the information you can includein McAfee ePO software dashboards andreports, you can increase your visibility intoeach endpoint’s compliance in addition tothe organization’s overall security posture.5
Secure Your Endpoints and DataProtect Your Business withEfficiency, Manageability, and aLower TCOIntel and McAfee deliver hardwareenhanced security solutions thatprovide deeper levels of protection withunprecedented efficiency, scalability,and control. By combining the hardwarefoundation of security from Intel CorevPro processors with strong management,protection, and encryption software fromMcAfee and Intel, you can help loweryour security operations’ costs whileenhancing your overall security postureand maintaining high performance andproductivity for your users.With this broad, centralized control,security teams have stronger, moreefficient options for protecting endpointsahead of emerging threats. Systems can beupdated before a potential threat reachesthem, and countermeasures can beinitiated remotely, reducing any impact onusers while keeping data safer. The result?Easier, more comprehensive managementfor IT, stronger, proactive protections withgreater compliance for your business, animproved experience for your users, and alower TCO for your company.Learn MoreFor more information on comprehensive hardware-based security solutions from Intel and McAfee, visit the following web sites:McAfee Endpoint ryption.aspxMcAfee ePO Deep d.aspxIntel /data-protection-aes-generaltechnology.htmlIntel vPro:www.intel.com/vproIntel AMT:www.intel.com/amt1Intel vPro Technology is sophisticated and requires setup and configuration. Availability of features and results will depend upon the setup and configuration of your hardware, software, and IT environment. To learn more about the breadth ofsecurity features, visit http://www.intel.com/technology/vpro.2IDC Worldwide Mobile Worker Population 2011-2015 Forecast, doc #232073, December 2011.3Intel Advanced Encryption Standard–New Instructions (Intel AES-NI) requires a computer system with an AES-NI-enabled processor, as well as non-Intel software to execute the instructions in the correct sequence. AES-NI is available onselect Intel Core processors. For availability, consult your system manufacturer. For more information, Gartner, “Comparing Endpoint Encryption Technologies,” ID:G00250256. March 2013. http://www.gartner.com/id 2397415.5No system can provide absolute security. Requires an Intel Secure Key-enabled platform, available on select Intel processors, and software optimized to support Intel Secure Key. Consult your system manufacturer for more information.6Security features enabled by Intel AMT require an enabled chipset, network hardware and software, and a corporate network connection. Intel AMT may not be available or certain capabilities may be limited over a host OS-based VPN or whenconnecting wirelessly, on battery power, sleeping, hibernating, or powered off. Setup requires configuration and may require scripting with the management console or further integration into existing security frameworks, and modifications orimplementation of new business processes. For more information, see y/intel-amt/.Software and workloads used in performance tests may have been optimized for performance only on Intel microprocessors. Performance tests, such as SYSmark and MobileMark, are measured using specific computer systems, components,software, operations and functions. Any change to any of those factors may cause the results to vary. You should consult other information and performance tests to assist you in fully evaluating your contemplated purchases, including the performance of that product when combined with other products.McAfee, the McAfee logo, McAfee ePolicy Orchestrator, and McAfee ePO are registered trademarks or trademarks of McAfee, Inc. or its subsidiaries in the United States and other countries. Other marks and brands may be claimed as theproperty of others. The product plans, specifications, and descriptions herein are provided for information only and subject to change without notice, and are provided without warranty of any kind, express or implied. Copyright 2013 McAfee, Inc.Intel, the Intel logo, Intel Core, Ultrabook, and vPro are trademarks of Intel Corporation in the U.S. and/or other countries.Copyright 2013 Intel Corporation. All rights reserved. Intel Corporation, 2200 Mission College Blvd., Santa Clara, CA 95052-8119, USA.* Other names and brands may be claimed as the property of others.Printed in USA0713/JL/PRW/PDFPlease Recycle328939-001US
tions.Learnmore
McAfee Endpoint Encryption includes new features that make it easier to identify and activate compatible devices. With the offline activation feature, you can install McAfee Endpoint Encryption, apply a preconfigured policy, and encrypt a device that does not currently have a connection to McAfee ePO. Any machine activated