Transcription
System Security Engineering forProgram Protection and CybersecurityMelinda ReedOffice of the Deputy Assistant Secretary of Defensefor Systems Engineering18th Annual NDIA Systems Engineering ConferenceSpringfield, VA October 27, 201518th NDIA SE ConferenceOctober 26-29, 2015 Page-1Distribution Statement A – Approved for public release by DOPSR on 10/19/2015, SR Case # 16-S-0131 applies. Distribution is unlimited.
Ensuring Confidence inDefense Systems Threat:– Adversary who seeks to exploit vulnerabilitiesto:o Acquire program and system information;o Disrupt or degrade system performance;o Obtain or alter US capability Vulnerabilities:– All systems, networks, and applications– Intentionally implanted logic (HW/SW)– Unintentional vulnerabilities maliciouslyexploited (e.g., poor quality or fragile code)– Controlled defense information resident on, ortransiting supply chain networks– Loss or sale of US capability that provides atechnological advantage Access points are throughoutthe acquisition lifecycle Consequences:– Loss of data; system corruption– Loss of confidence in critical warfightingcapability; mission impact– Loss of US capability that provides atechnological advantage18th NDIA SE ConferenceOctober 26-29, 2015 Page-2 and across numerous supplychain entry points- Government- Prime, subcontractors- Vendors, commercial partsmanufacturers- 3rd party test/certificationactivitiesDistribution Statement A – Approved for public release by DOPSR on 10/19/2015, SR Case # 16-S-0131 applies. Distribution is unlimited.
Spectrum of Program ProtectionRisks to ConsiderQualityEscapeProduct defect/inadequacyintroduced eitherthrough mistake ornegligence duringdesign,production, andpost-productionhandling resultingin the introductionof deficiencies,vulnerabilities, anddegraded life-cycleperformance.ReliabilityFailureMission failure inthe field due toenvironmentalfactors unique tomilitary andaerospaceenvironmentfactors such asparticle strikes,device aging, hotspots, electromagnetic pulse,etc.FraudulentProductCounterfeit andother than genuineand new devicesfrom the legallyauthorized sourceincludingrelabeled, recycled,cloned, defective,out-of-spec, etc.MaliciousInsertionThe intentionalinsertion ofmalicious hard/softcoding, or defect toenable physicalattacks or causemission failure;includes logicbombs, Trojan ‘killswitches’ andbackdoors forunauthorizedcontrol and accessto logic and edextraction ofsensitiveintellectualproperty usingreverseengineering, sidechannel scanning,runtime securityanalysis,embedded systemsecurity weakness,etc.Stolen dataprovides potentialadversariesextraordinaryinsight into USdefense andindustrialcapabilities andallows them tosave time andexpense indeveloping similarcapabilities.DoD Program Protection focuses on risks posed by malicious actors18th NDIA SE ConferenceOctober 26-29, 2015 Page-3Distribution Statement A – Approved for public release by DOPSR on 10/19/2015, SR Case # 16-S-0131 applies. Distribution is unlimited.
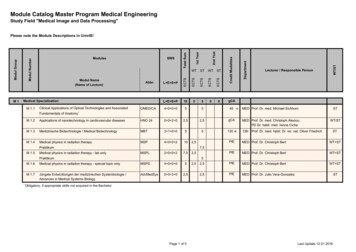
Program Protection inDoDI 5000.02 DoD considers SSE a critical discipline of SE. To furtherestablish SSE, DoD has focused on integrating SSE into SEpolicy, contracts and workforce education. System Security Engineering is accomplished in the DoDthrough program protection planning (PPP) DoDI 5000.02 requires program managers to employ systemsecurity engineering practices and prepare a ProgramProtection Plan to manage the security risks to criticalprogram information, mission-critical functions andinformation Program managers will describe in their PPP:––––18th NDIA SE ConferenceOctober 26-29, 2015 Page-4Critical Program Information, mission-critical functions and criticalcomponents, and information security threats and vulnerabilitiesPlans to apply countermeasures to mitigate associated risksPlans for exportability and potential foreign involvementThe Cybersecurity Strategy and Anti-Tamper plan are includedDistribution Statement A – Approved for public release by DOPSR on 10/19/2015, SR Case # 16-S-0131 applies. Distribution is unlimited.
Program ProtectionIntegrated in PolicyDoDI 5000.02 Operation of the Defense Acquisition System–Regulatory Requirement for Program Protection Plan at Milestones A, B, C and FRP/FDDDoDI 5200.39 Critical Program Information (CPI) Identification and Protection WithinResearch, Development, Test, and Evaluation (RDT&E)––Assigns responsibility for Counterintelligence, Security, and System Engineering support for the IDand protection of CPIRescoped definition of CPIDoDI 5200.44 Protection of Mission Critical Functions to Achieve Trusted Systems andNetworks–Establishes policy and responsibilities to minimize the risk that warfighting capability will be impaireddue to vulnerabilities in system design or subversion of mission critical functions or componentsDoDI 4140.67 DoD Counterfeit Prevention Policy–Establishes policy and assigns responsibility to prevent the introduction of counterfeit material at anylevel of the DoD supply chainDoDI 8500.01 Cybersecurity–18th NDIA SE ConferenceOctober 26-29, 2015 Page-5Establishes policy and assigns responsibilities to achieve DoD cybersecurity through a defense-indepth approach that integrates the capabilities of personnel, operations, and technology, and supportsthe evolution to network centric warfareDistribution Statement A – Approved for public release by DOPSR on 10/19/2015, SR Case # 16-S-0131 applies. Distribution is unlimited.
What Are We Protecting?Program Protection PlanningDoDI 5000.02DoDM 5200.01, Vol. 1-4DoDI 5200.39TechnologyDoDI 8500.01DoDM 5200.45DoDI 8510.01DoDI 5200.44DoDI 5230.24ComponentsInformationWhat: A capability element that contributesto the warfighters’ technical advantage (CPI)What: Mission-critical elements andcomponentsWhat: Information about applications,processes, capabilities and end-itemsWho Identifies: System Engineers withCI/Intel and Security SME supportWho Identifies: System Engineers, LogisticiansWho Identifies: AllID Process: Criticality AnalysisID Process: CPI identification, criticalityanalysis, and classification guidanceThreat Assessment: Foreign collection threatinformed by Intelligence andCounterintelligence (CI) assessmentsThreat Assessment: Defense IntelligenceAgency Threat Analysis CenterThreat Assessment: Foreign collection threatinformed by Intelligence andCounterintelligence assessmentsCountermeasures: Anti-Tamper,Classification, Exportability Features,Security, etc.Countermeasures: SCRM, Cybersecurity, Anticounterfeits, software assurance, TrustedFoundry, etc.Countermeasures: Cybersecurity,Classification, Export Controls, Security, etc.Goal: “Keep secret stuff in”by preventing the compromise and loss of CPIGoal: “Keep malicious stuff out”by protecting key mission componentsGoal: “Keep critical information from gettingout” by protecting data from our adversariesID Process: CPI IdentificationProtecting Warfighting Capability Throughout the LifecyclePolicies, guidance and white papers are found at our initiatives site: http://www.acq.osd.mil/se/initiatives/init pp-sse.html18thNDIA SE ConferenceOctober 26-29, 2015 Page-6Distribution Statement A – Approved for public release by DOPSR on 10/19/2015, SR Case # 16-S-0131 applies. Distribution is unlimited.
Systems Security EngineeringIntegrates Program Protection PlanningConcept StudiesDesign DefinitionSRRSystem Definition(Functional Baseline)Preliminary Design (Allocated Baseline)Design DefinitionDesign DefinitionSE Baselines*CriticalityAnalysisDetermine criticalcomponentsbased on criticalmission threadsAnalyzecomponentvulnerability tomalicious exploitIdentify potentialcomponentsuppliersCPI AnalysisIdentify capabilityelementsproviding a UStechnologicaladvantageAssess the riskassociated witheach CPI(exposure,consequence yCategorizesystem (C,I,A)Identifycontrolbaselines andoverlays, thentailorTrace controlstorequirementsDetailed Design (Product Baseline)Program Protection PlanDetermine candidate protectionmeasures to address vulnerabilities:anti-tamper, cybersecurity, hardware/software assurance, physicalsecurity, operations security, supplychain, system security, and trustedsuppliersDetermine foreign involvementexpectations and impacts onprotection measuresConduct engineering risk/costtrade-off analysis to selectprotection measuresThreats and Vulnerabilities AssessmentIdentify supply chainthreats and vulnerabilitiesIdentify foreigncollection threats andvulnerabilitiesIdentify personnel, physical, operationalthreats and vulnerabilities18th NDIA SE ConferenceOctober 26-29, 2015 Page-7Identify acquisitionmitigations (e.g.,blind buy, rotection measures areidentified and integratedinto technical baselines,iteratively informed by andinforming the maturingdesign.ContractorRespond to acquisition andsecurity requirementsContinually assess securityrisks during design reviewsand system implementationConduct early defenseexportability featuresplanning and designTest and EvaluationAssess hardware andsoftware vulnerabilitiesEvaluate Anti-TamperprotectionsVerify securityrequirements (Contractor,DT&E, OT&E)Distribution Statement A – Approved for public release by DOPSR on 10/19/2015, SR Case # 16-S-0131 applies. Distribution is unlimited.
CPI Policy Updates CPI and AT Policy Updates– DoDI 5200.39, Critical Program Information (CPI)Identification and Protection Within Research,Development, Test, and Evaluation (RDT&E):Revises the CPI definition, requires CPI identificationearly and throughout the program, and emphasizeshorizontal identification and protection– DoDD 5200.47E, Anti-Tamper: Designates theSecretary of the AF as the Executive Agent for AntiTamper and establishes requirements for ATplanning, implementation, and evaluation. Revised definition of CPI has been scoped to focus only onthose elements that provide a capability advantage and resideon the end-item (system or supporting systems)– “U.S. capability elements that contribute to the warfighters’ technicaladvantage, which if compromised, undermines U.S. military preeminence.U.S. capability elements may include, but are not limited to, softwarealgorithms and specific hardware residing on the system, its trainingequipment, or maintenance support equipment.”18th NDIA SE ConferenceOctober 26-29, 2015 Page-8Distribution Statement A – Approved for public release by DOPSR on 10/19/2015, SR Case # 16-S-0131 applies. Distribution is unlimited.
Joint Federated Assurance Center(JFAC)Field ProgrammableGate 10110111011111101static void goodG2B() { char * data;char data buf[100] ""; data data buf; /* FIX: Specify the fullpathname for the library ; { HMODULE hModule; /*POTENTIAL FLAW: If the path tothe library is not specified, anattacker may be able to * replacehis own file with the intendedlibrary */ hModule LoadLibraryA(data); if (hModule ! NULL) { FreeLibrary(hModule);printLine("Library loaded and freedsuccessfully"); } else {printLine("Unable to load library");}}}Erasable ProgrammableRead-Only Memory (EPROM)Computer SourceSoftware CodeBinary ComputerSoftware CodeAssure Mission SW and HW SecurityKey Participants: Sponsor(s): ASD(R&E)/DASD(SE) Contributors: CIO, AF, Army, Navy, USMC, NSA, NRO, MDA, DISA,Defense Microelectronics Activity (DMEA)Approach: Establish federation of HwA and SwA capabilities to support programsin program protection planning and execution Support program offices across life cycle by identifying and facilitatingaccess to Department SwA and HwA expertise and capabilities,policies, guidance, requirements, best practices, contractinglanguage, training, and testing supportIntent: Congress directed DoD to “ provide for the establishment of ajoint federation of capabilities to support the trusted defensesystem needs to ensure security in the software and hardwaredeveloped, acquired, maintained, and used by the Department.”(FY14 NDAA, Sect. 937)Expected Outcomes/Deliverables: Federated cross-DoD awareness and coordination of software andhardware assurance (SwA/HwA) capabilities and expertise Development and sharing of SwA/HwA vulnerability assessmentbest practices, tested tools, and proven processes Identification of R&D needs to advance SwA/HwA capabilities forprograms in acquisition, operational systems, and legacy systemsand infrastructureMilestones:Formed Steering Committee and Working Groups7/14Initiated First Series of Technical Tasks9/14Charter signed by Deputy Secretary of Defense2/15Congressional Report on funding, organization,management, and operations of JFAC signed &submitted3/15CONOPS signed by stakeholders of Federation8/15Capability Assessment, Gap Analysis, Strategic Plan10/15Joint Federated Assurance Center (JFAC) IOC12/15 Coordinate with DoD R&D for HwA and SwA Procure, manage, and distribute enterprise licenses for SwA/HwAtools18th NDIA SE ConferenceOctober 26-29, 2015 Page-9Distribution Statement A – Approved for public release by DOPSR on 10/19/2015, SR Case # 16-S-0131 applies. Distribution is unlimited.
Program ProtectionIntegrated in Contract RegulationDFARS 252.204-7012Purpose:Establish minimum requirementsfor DoD unclassified controlledtechnical information oncontractor information systemsRequires:Contractors implement minimumset of information securitycontrolsFlow Down to SubcontractorsContractors report cyber incidentand compromises on ControlledTechnical InformationContractor actions to supportDoD damage assessment asneededPublished November 18, 201318th NDIA SE ConferenceOctober 26-29, 2015 Page-10 DFARS Subpart 204.73 – Safeguarding Unclassified Controlled rs/dfars/html/current/204 73.htm#204.7303 PGI 204.7303-3 Cyber Incident and Compromise Reportinghttp://www.acq.osd.mil/dpap/dars/pgi/pgi htm/PGI204 73.htm#204.7303-3 DoDI 5230.2, Distribution Statements on Technical /pdf/523024p.pdf Frequently Asked Questions (FAQs) Regarding DFARS Subpart 204.73 and PGISubpart ledTechnicalInformation FAQ.pdf Guidance to Requiring Activities for Implementing DFARS Clause 252.204-7012,Safeguarding Unclassified Controlled Technical ide.pdf**New Interim Rule Safeguarding of Covered Defense Informationand Cyber Incident Reporting published in 2015: Expands scope to covered defense information Direct the use in all solicitations and contracts Replaces security controls specified in NIST SP 800-53 with NISTSP 800-171 Contractors to report cyber incidents affecting Controlled DefenseInformation and ability to provide operationally critical support Contractors to submit any malicious softwareDistribution Statement A – Approved for public release by DOPSR on 10/19/2015, SR Case # 16-S-0131 applies. Distribution is unlimited.
PPP Elements withinRequest For Proposal (RFP) Review document titled, “Suggested Language to Incorporate System SecurityEngineering for Trusted Systems and Networks into DoD Requests For Proposals”* Statement of Work (SOW) Systems Engineering (SE) Section or Security Section–– Section L– Include statement SECL0002 from “suggested language”*o This requires the contractor to describe the integration of program protection into their SEprocessesEnsure that Systems Engineering Plan (SEP) Section 4.4 Technical Reviews include:–– Review and adapt statements from the “suggested language”*At a minimum include SOW001, SOW004, SOW009 and SOW0010o These statements ensure that criticality analysis, supply chain risk, and software assuranceare addressed by the contractorEntry Criteria – Updated PPP (this will capture the CA/VA/TA activities)Products – Updated Security Risk Assessment and Mitigation Plans; updated PP Activities onProgram ScheduleIf not included in the SEP then incorporate in the SOW an updated PPP as entrancecriteria to all technical reviews and an updated risk assessment as an exit criteria forall technical reviewsRFP/SOW Plays a Key Role in Integrating the PPP into -TSN-in-DoD-RFPs.pdf18th NDIA SE ConferenceOctober 26-29, 2015 Page-11Distribution Statement A – Approved for public release by DOPSR on 10/19/2015, SR Case # 16-S-0131 applies. Distribution is unlimited.
Designing and Managing Cybersecurityin our ProgramsDoDI 5000.02 Release Memo to the Acquisition Workforce“I have also already initiated work on a new enclosure that will deal withthe increasingly serious problem of designing for and managingcybersecurity in our programs.”Better Buying Power 3.0 Develop a new Enclosure for DoDI 5000.02 addressing allaspects of the program manager’s and other’s responsibilitiesfor cybersecurity throughout the product lifecycle. A draft willbe provided to the USD(AT&L) by July 2015. Review current system security engineering design processesand methods and recommend standardization or otherapproaches to improve cybersecurity of system designs,including all outside interfaces, by October 2015.Establishes expectations and provides methodology forSSE processes during design, development and through sustainment18th NDIA SE ConferenceOctober 26-29, 2015 Page-12Distribution Statement A – Approved for public release by DOPSR on 10/19/2015, SR Case # 16-S-0131 applies. Distribution is unlimited.
Incorporating Program Protectioninto Acquisition Workforce Training Effective program protection planning is enabledby qualified, trained personnel– Two program protection coursesare currently in development– First course (ENG 160) is expectedto be available in FY16 ENG 160: Program Protection Overview– Provides an overview of program protection concepts, policy and processes– Intended for the entire Acquisition Workforce, with focus on ENG and PM ENG 260: Program Protection Practitioner Course– Intended for Systems Engineers and System Security Engineers– Focuses on application of program protection concepts and processes18th NDIA SE ConferenceOctober 26-29, 2015 Page-13Distribution Statement A – Approved for public release by DOPSR on 10/19/2015, SR Case # 16-S-0131 applies. Distribution is unlimited.
Our Focus on SSE and SE DoD is putting guidance in place for a risk-based cost benefittrade-off process to protect programs and systems, theirsupply chain, and their software developmentDoD is emphasizing the importance of SSE within systemsengineering and its contribution to the design of systems by:– Ensuring that program protection is addressed as part of system engineering, testand sustainment activities– Incorporating program protection and system security engineering requirements andprocesses into engineering development contracts– Working with industry and standards groups to synergize methodologies Industry has been playing an important role in the DoD SSEinitiative by:– Investing in research and processes to protect systems, the supply chain and thesoftware development– Developing their SE and SSE processes and skillsDoD efforts are targeting integration of system security engineeringconsiderations throughout the system life cycle18th NDIA SE ConferenceOctober 26-29, 2015 Page-14Distribution Statement A – Approved for public release by DOPSR on 10/19/2015, SR Case # 16-S-0131 applies. Distribution is unlimited.
Systems Engineering:Critical to Defense AcquisitionDefense I
18th NDIA SE Conference October 26-29, 2015 Page-1 Distribution Statement A –Approved for public release by DOPSR on 10/19/2015, SR Case # 16S--0131 applies. Distribution is unli mited. System Security Engineering for Program Protection and Cybersecurity Melinda Reed Office of the Depu