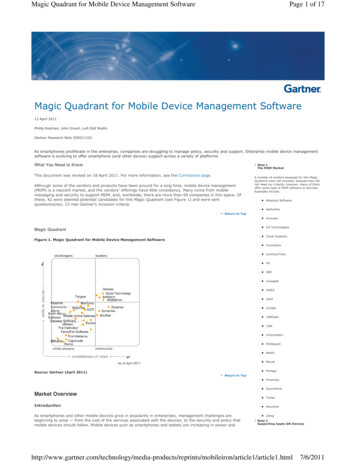
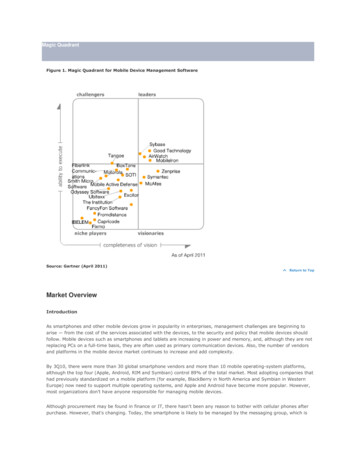
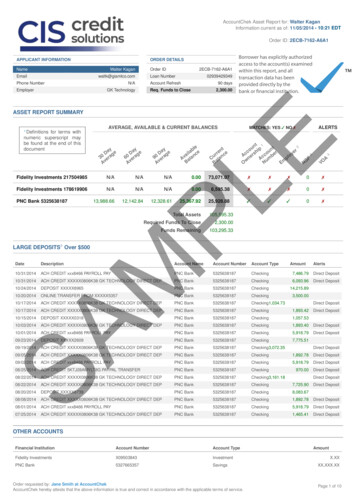
Transcription
Authorized Device and Software Management InitiativesUnauthorized Device & Unauthorized SoftwareWorking Group Bi-weekly MeetingOctober 11, 2018Code 710Qi’Anne KnoxShoeb SirajTammy Tuttle1
Agenda Roll CallPhase 1 ACES Orders Status UpdateAuthorized Device (AD) Initiative Phase 1 Update & Next StepsSoftware Management (SM) InitiativeCommunication ClarificationReferences2
Roll Call3
ACES Orders Status Update Orders not received to date may impact delivery as it relates to Office 365(O365) Velocity Migration requirements Please continue to coordinate with Emma Coates from End User ServicesOffice (EUSO) for orders not fulfilled within waves and send RITM numbersfrom orders placed4
AD Initiative Phase 1 Update MDM User Agreement SATERN is 99% complete “Security controls will be levied to ensure users remain up to date ontheir operating system (OS)”– Currently, users will get alerts that their OS needs to be updated to continueusing MDM– In the future, the compliancy check may be enforced where it removes MDM Non-ACES Government Funded Equipment (GFE)/PersonallyFunded Equipment (PFE) registration timeline will be part of theOffice 365 (O365) Delta Operational Readiness Review (ORR) andDelta Key Decision Point (KDP)-E5
O365 Update At Delta ORR, SERT did not approve moving forward with fullvelocity migration, but instead the O365 Project Team will beimplementing a limited further deployment at MSFC to allowadditional coordination and testing– This deployment may include some additional early adopters at GSFC, but theproject team needs to confirm this is feasible. O365 deployment completion date is TBD Planning to start Velocity migration on October 246
AD Initiative Phase 1 Next Steps Continue coordination with O365 Project Team UD Security Requirements are being implemented in conjunction withO365. Requirements of particular interest will be:– PIV Authentication is default required method for authentication RSA Token and UserName/Password can be used to authenticate in, but willrequire for users to have a “PIV Exemption” to utilize either option listed– Reviewing list of users with only RSA Token and UserName/Password atGSFC and remote centers (except Agency action)– O365 Services can only be accessed from NASA IP space, exception beingMDM enrolled devices Users will either have to be on Center Networks or Virtual Private Network (VPN) Continue exploring single Mobile Device System Security Plan at GSFC Work with Enterprise Border Projection (EBPro) Team to see if VPNenrollment communication will be sent7
SM Initiative GSFC Web Content Filter Transition:– Developing process to review web content currently categorized asunrated End goal is to get back to the original state of blocking unrated categoriesby January 1, 2019– Planning to transition to automated portal late October Communication regarding this change will be distributed Unauthorized Software:– Building inventory list from BigFix dataset to create baseline and begindeveloping whitelist– The Agency SM team is focused on licensing currently– Plan to attend first Tiger Team meeting October 16 to learn next steps8
Communications Advisory: Use of Unauthorized Software on NASA Devices sentOctober 9 at 9:08 AM– The intent of the advisory was meant to focus on unauthorizedapplications around “games” that are currently installed on end clientsystems (not mobile devices– Corrected communication will be sent EUSO News (October 2018) sent on October 5 at 6:00 PM– MDM notices for enrollment will be targeted to the current Active SyncUsers with non-ACES GFE & Personal Devices (due to 10K LicenseCap)– EUSO is the MDM License Authoritative Source and will sendflag/notice to core UD Team when 7K MDM Licenses have beendistributed/accepted (to and by users)9
Agency Communication10
EUSO Communication11
References MDM Registration Site: https://mdr.nasa.gov/ Registration l NAMS Workflow (not live):– MDM PFE (ID: 252534) – MDM GFE (ID: 252533) https://idmax.nasa.gov/nams/asset/252533/017767035 NASAs Strategy to Improve Network Security OCIO ve-network-security O365 Resources: http://inside.nasa.gov/euso/office-365-resources AD/SM on ITCD Website: https://itcd.gsfc.nasa.gov/12
GSFC Points of Contact Please continue to communicate your concerns and suggestions tous, which we will communicate up.– GSFC-IT-Security-Review@mail.nasa.gov– shoeb.siraj@nasa.gov– qianne.l.knox@nasa.gov Next Meeting is October 2513
Backup14
Reminders NASA webmail will no longer be remotely accessible from outside theNASA network, and will require an Agency Badge (PIV or SmartBadge) or RSA Token for authentication. Users will no longer be ableto authenticate using username/password except for “PIVExemption” Webmail will remain remotely accessible via VPN with an AgencyBadge or RSA token Remote users will no longer be able to access NASA email via theMicrosoft Outlook (or compatible) client unless they are connected tothe NASA internal network via VPN– Personal Devices are not authorized to connect per UD Policy15
NASA GFE & PFE MDM Program (1) Users should not enroll any non-ACES device in MDM until they have beenmigrated to O365. Users will receive notification of migration schedule twoweeks prior to occurrence with instructions and additional details NASA will not authorize personal devices for use on the NASA network,however, users may be eligible to enroll their personal smartphone (iOS orAndroid) in NASA’s MDM Program given they meet the initial set of baselinerequirements Enrollment of a personal device in NASA’s MDM program is voluntary, andthe government will not mandate the requirement to anyone Users are only allowed to enroll 1 personal device in NASA’s MDM program Users who have an enrolled ACES or GFE device are not eligible to enroll apersonal device in NASA MDM program due to current license limitations16
NASA GFE & PFE MDM Program (2) NASA personnel which have the NASA MDM container or solution installedon their personally owned devices shall not access the MDM solution fromsuch device while outside the U.S. and its territories (enforced through theuse of geofencing capabilities) Security controls will be levied to ensure users remain up to date on theiroperating system Security controls will be levied to ensure users are not violating supply chainmanagement controls (certain phones/models will be blacklisted fromparticipation) All users registering a personal device will be required to submit a NAMSrequest for approval All users registering a personal device will be required to accept the MDMterms of use via SATERN training on an annual basis17
MDM Baseline Requirements Civil Servants. A NASA Civil Servant may be permitted to participate in the MDMProgram if two conditions are met. First, the Civil Servant must need remote access toNASA e-mail and calendaring functions in order to effectively perform his or her jobduties. Second, the Civil Servant must voluntarily request to use their personally-ownedmobile device instead of GFE. Contractor Personnel. An employee of a contractor may be permitted to participate inthe MDM Program if two conditions are met. First, the employee must need remoteaccess to NASA e-mail and calendaring functions in order to accomplish contract tasks.Second, use of a personally-owned mobile device must be more efficient and/or costeffective than using GFE for remote access. Other Individuals. Other individuals, such as grantees, investigators, or partners, maybe permitted to participate in the MDM Program if two conditions are met. First, theindividual must need remote access to NASA e-mail and calendaring functions in order toaccomplish a NASA purpose. Second, use of a personally-owned mobile device must bemore efficient and/or cost effective than using GFE for remote access.18
Oct 11, 2018 · NASA webmail will no longer be remotely accessible from outside the NASA network, and will require an Agency Ba