Transcription
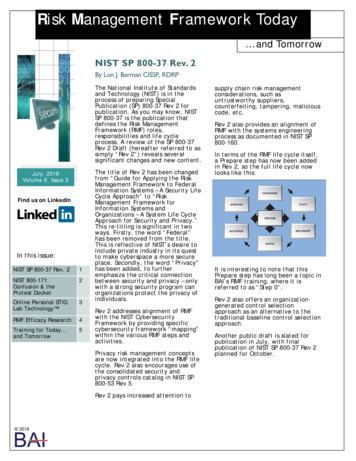
Risk Management Framework Today and TomorrowNIST SP 800-37 Rev. 2By Lon J. Berman CISSP, RDRPThe National Institute of Standardsand Technology (NIST) is in theprocess of preparing SpecialPublication (SP) 800-37 Rev 2 forpublication. As you may know, NISTSP 800-37 is the publication thatdefines the Risk ManagementFramework (RMF) roles,responsibilities and life cycleprocess. A review of the SP 800-37Rev 2 Draft (hereafter referred to assimply “Rev 2”) reveals severalsignificant changes and new content.July, 2018Volume 8, Issue 3Find us on LinkedInIn this issue:NIST SP 800-37 Rev. 21NIST 800-171:Confusion & theProtest Docket2Online Personal STIGLab Technology 3RMF Efficacy Research4Training for Today and Tomorrow5The title of Rev 2 has been changedfrom “Guide for Applying the RiskManagement Framework to FederalInformation Systems – A Security LifeCycle Approach” to “RiskManagement Framework forInformation Systems andOrganizations – A System Life CycleApproach for Security and Privacy.”This re-titling is significant in twoways. Firstly, the word “Federal”has been removed from the title.This is reflective of NIST’s desire toinclude private industry in its questto make cyberspace a more secureplace. Secondly, the word “Privacy”has been added, to furtheremphasize the critical connectionbetween security and privacy – onlywith a strong security program canorganizations protect the privacy ofindividuals.Rev 2 addresses alignment of RMFwith the NIST CybersecurityFramework by providing specificcybersecurity framework “mapping”within the various RMF steps andactivities.Privacy risk management conceptsare now integrated into the RMF lifecycle. Rev 2 also encourages use ofthe consolidated security andprivacy controls catalog in NIST SP800-53 Rev 5.Rev 2 pays increased attention to 2018 supply chain risk managementconsiderations, such asuntrustworthy suppliers,counterfeiting, tampering, maliciouscode, etc.Rev 2 also provides an alignment ofRMF with the systems engineeringprocess as documented in NIST SP800-160.In terms of the RMF life cycle itself,a Prepare step has now been addedin Rev 2, so the full life cycle nowlooks like this:It is interesting to note that thisPrepare step has long been a topic inBAI’s RMF training, where it isreferred to as “Step 0”.Rev 2 also offers an organizationgenerated control selectionapproach as an alternative to thetraditional baseline control selectionapproach.Another public draft is slated forpublication in July, with finalpublication of NIST SP 800-37 Rev 2planned for October.
Risk Management Framework Today and TomorrowPage 2NIST 800-171: Confusion & the Protest DocketBy Kathryn Daily, CISSP, RDRP“ a lack of clarityon the requirementsthemselves willresult in additionalprotests of contractawards .” ownerswill need to address anyof this.”I’m sure by now you’ve at least familiarized yourself with NIST 800171, “Protecting Unclassified Information in Nonfederal InformationSystems and Organizations.” Whatwasn’t made clear was how DoD willevaluate a contractor’s System Security Plan (SSP). In May, DoD releaseddraft DoD Guidance for ReviewingSystem Security Plans and the “NISTSP 800-171 Security RequirementsNot Yet Implemented” which provided some answers but also includedambiguous evaluation criteria.New Guidance suggests that the Government’s evaluation of Contractors’SSP will be used as selection criteriain new contract awards. Additionalguidance has been provided in theform of an SSP Priority Ranking Matrixwhich gives a value to each securityrequirement that is not implemented. The newly released guidanceprovides a few competing scenariosdetailing different implementationsin which the offeror’s compliancewith stated standards are consideredin source selection.Scenario 1: The clause is included inthe contract, but not evaluated attime of award; basically, the offerorself-attest to their compliance withNIST SP 800-171. The cybersecurityrequirements will have no bearing oncontract award or performance.Within this scenario, DoD could assess/track implementation of the 800-171 security requirements after contract award by including cybersecurity language in the statement of workand/or as data requirements.Scenario 2: A DoD contracting officecould evaluate an offeror’s compliance with NIST SP 800-171 as part of 2018 source selection. DoD could make anacceptable/unacceptable decisionbased on the implementation status ofthe NIST 800-171 requirements.Scenario 3: DoD acquisition evaluatorscould assess an offeror’s implementation of its SSP as a separate technicalevaluation factor with evaluation consisting of an assessment of the contractor’s SSP as a stand-alone document or an independent governmentassessment to validate the implementation of each requirement of the SSPusing evaluation tools identified inNIST SP 800-171A.Regardless of the scenario, it is likelythat evaluation of technical requirements by non-IT acquisition personnelcoupled with a lack of clarity on therequirements themselves will result inadditional protests of contractawards.Questions regarding NIST 800-171 canbe directed to kathryn@rmf.org.
Risk Management Framework Today and TomorrowPage 3Online Personal STIG Lab Technology By P. Devon Schall, M.S., MA.Ed. CISSP, RDRPAt BAI RMF Resource Center our primary focus is to provide the most relevantand advanced RMF and RMF ancillary service training in the cybersecurityindustry. In delivering curriculum and instruction, learning theories are ofparamount importance to us in effectively meeting the stated goal above.A very popular model in the field of instructional design and technology isBloom’s Taxonomy. Bloom’s model consists of six levels of knowledge typeswhich are presented visually in the shape of a pyramid. An illustration ofBloom’s Taxonomy is outlined in Figure 1.“ BAI’s STIG 101subject matterexperts providecoachingassistance.”As shown in Figure 1, Bloom’s Taxonomy culminates in a tier titled Creatingwhich demonstrates mastery of a specific topic. Bloom’s states that the higherthe student rises to the top of the knowledge type pyramid, the more masterythe student possesses of the subject being studied.Bloom’s Taxonomy relates directly to the recent development of STIG 101 whichsupports our flagship RMF for DoD IT and RMF for Federal Agencies trainingprograms. In creating STIG 101, our primary course developer was struggling increating effective STIG curriculum. She did not want to create yet anotherPowerPoint deck in training a topic as technical as STIG’s.Her solution led to the creation of Online Personal STIG Lab Technology . Viathis training methodology, students are given access to individual virtual labenvironments where they perform hands on application of STIG settings. ViaOnline Personal STIG Lab Technology BAI’s STIG 101 subject matter expertsprovide coaching assistance as the students work through a variety of STIGimplementation exercises.By allowing the students to Create their own STIG settings, we have hadimmense success in providing them with the knowledge needed to leave ourtraining and return to their work environment with the tangible technical skillsnecessary to begin the STIGing process. 2018 Figure 1. Bloom’s Taxonomy.
Risk Management Framework Today and TomorrowPage 4RMF Efficacy ResearchRMF Community:In August of 2015, I began the pursuit of obtaining my Doctorate ofPhilosophy (Ph.D.) in Information Technology with the majority of my courseworkfocused on cybersecurity. Fast forward three years, and I am excited to haverecently received dissertation topic approval which focuses on RMF effectivenessin relation to formalized RMF training. Over the coming months, I will be reachingout to the RMF community to collect survey data on the perceived shortfalls ofRMF from an effectiveness and implementation standpoint.“.I plan to presentthe findings the RMFcommunity providesme to the authoringteam at NIST ”After conducting a literature review of RMF related topics, I found RMF hasbeen studied very minimally at an academic level. Most of the available literatureon RMF consists of white papers and informal conference presentations.Literature reviewed to date indicates RMF practitioners and RMF decision-makersare frustrated and feel that RMF may not be meeting the goals and objectives itoriginally defined for itself, but as previously stated, minimal research has beenconducted on viable solutions to combat these perceived RMF shortfalls. Myresearch seeks to provide solutions in the ways in which RMF can be successfuland hopefully curb the trend of frustration and finger pointing in blaming NIST forcreating cumbersome ineffective policy.I recognize this study of RMF efficacy cannot fix RMF entirely, but I hope Ican collect enough data and the data collected indicates trends in the perceptionand real-world experiences of those attempting to implement RMF. Withoutgetting into the granular details of research methodology, I will be reaching outto the RMF community at large by sharing a link to my data collection instrument.I recognize as a society, we have become inundated with questionnaires and theyare quite the annoyance. With all of this being said, if you see a link sent from meto a questionnaire on RMF Efficacy in the coming months, I graciously ask you totake a few minutes of your time to provide your valuable experiences.At BAI RMF Resource Center, we consider ourselves leading experts in RMFtraining as well as the study of RMF. As an RMF scholar, I hope to present thefindings you provide me to the authoring team at NIST and hopefully take a stepin the right direction of strengthening the cybersecurity posture of our nation.Sincerely,Devon Schall, MS, MAEd, CISSP, RDRPExecutive Director Training ServicesBAI Information Securitydevon@rmf.org 2018
Risk Management Framework Today and TomorrowTraining for Today and TomorrowPage 5Our training programs: Contact Us!RMF Today and Tomorrowis a publication of BAI Information Security, Fairlawn,Virginia.Phone: 1-800-RMF-1903Fax: 540-518-9089Email: rmf@rmf.org Payment arrangementsinclude credit cards,SF182 forms, andPurchase Orders.RMF for Federal Agencies – recommended for Federal “civil” agency (non-DoD) employees and contractors that require detailed RMF knowledge and skill training; covers the RMF life cycle, documenta on, and security controls.eMASS eSSENTIALS – designed as an add-on to RMF for DoD IT. This training program provides prac cal guidance on thekey features and func ons of eMASS. “Live opera on” of eMASS (in a simulated environment) is u lized.Con nuous Monitoring Overview – designed as an add-on to RMF for DoD IT. This is a one day “fundamentals” program.RMF in the Cloud – designed as an add-on to RMF for DoD IT. This one-day training program will provide students theknowledge needed to begin shi ing their RMF efforts to a cloud environment.Cer fied Authoriza on Professional (CAP) Prepara on – designed as a one-day add-on to RMF for DoD IT. CAP Prepprovides prepara on for the Cer fied Authoriza on Professional (CAP) cer fica on administered through (ISC)2.STIG 101 – is designed to answer core ques ons and provide guidance on the implementa on of DISA Security TechnicalImplementa on Guides (STIGs).Our training delivery methods: Registra on forall classes isavailable ath ps://register.rmf.orgRMF for DoD IT – recommended for DoD employees and contractors that require detailed RMF knowledge and skill training; covers the RMF life cycle, documenta on, security controls, and transi on from DIACAP to RMF.Tradi onal classroom – regularly-scheduled training programs are offered at various loca ons na onwide, including Colorado Springs, Huntsville, Na onal Capital Region (Pentagon/Crystal City area), Dallas, Pensacola, and San Diego.Online Personal ClassroomTM – regularly-scheduled training programs are also offered in an online, instructor-led format that enables you to ac vely par cipate from the comfort of your home or officeOn‐site training – our instructors are available to deliver any of our training programs to a group of students from yourorganiza on at your site; please contact BAI at 1-800-RMF-1903 to discuss your requirementsTrainPlus! & Registered DoD RMF Prac oner (RDRP) – BAI offers ancillary support services such as TrainPlus! which is afree monthly conference call offered to our alumni staffed with RMF subject ma er experts. We also offer a program tledRDRP that provides registrants access to a valuable community of RMF for DoD prac oners.Regularly‐scheduled classes through December, 2018:RMF for DoD IT—4 day program (Fundamentals and In Depth) Na onal Capital Region 1‐4 OCT Online Personal Classroom 6 SEP 13 NOVHuntsville 24 ‐ 27 SEP 10 ‐ 13 DECPensacola 13‐16 AUG 5‐8 NOVColorado Springs 27‐30 AUG 3‐6 DECSan Diego 17‐20 SEPDallas 30 JULY ‐ 2 AUG 29 OCT ‐ 1 NOVOnline Personal Classroom 20 ‐ 23 AUG 24 ‐ 27 SEP 22 ‐ 25 OCT 26 ‐ 29 NOV 10 ‐ 13 DECeMASS eSSENTIALS—1 day programNa onal Capital Region 5 OCTHuntsville 28 SEP 14 DECPensacola 17 AUG 9 NOVColorado Springs 31 AUG 7 DECSan Diego 21 SEPDallas 3 AUG 2 NOVCon nuous Monitoring Overview —1 day program Online Personal Classroom 25 JUL 30 OCTRMF in the Cloud—1 day program 2018 Online Personal Classroom 8 AUG 15 NOVCAP Prep—1 day program Online Personal Classroom 5 SEP 29 OCTSTIG 101—1 day program Online Personal Classroom 28 SEP 26 OCT 14 NOV 30 NOV 14 DEC
RMF for DoD IT - recommended for DoD employees and contractors that require detailed RMF knowledge and skill train-ing; covers the RMF life cycle, documentaon, security controls, and transion from DIACAP to RMF. RMF for Federal Agencies - recommended for Federal "civil" agency (non-DoD) employees and contractors that re-











