Transcription
CIP Standards Version 5Requirements & StatusPhilip Huff – Arkansas Electric Cooperative CorporationDoug Johnson – Commonwealth Edison CompanyDavid Revill – Georgia Transmission CorporationCSO706 SDT WebinarAugust 24, 2011
AgendaB kBackgrounddVersion 4 - OverviewVersion 5 – Requirements SummarySchedule and Implementation PlanAugust 24, 2011CSO706 SDT Webinar2
Project BackgroundVersion 1 Filed with FERC August 28, 2006 Approved by FERC January 18, 2008 Effective July 1, 2008 through January 1, 2010 (phased)Version 2 Low-hanging fruit Filed with FERC May 22, 2009 Approved by FERC September 30, 2009 Effective April 1,1 2010Version 3 Compliance filing to Version 2 Filed with FERC December 2929, 2009 Approved by FERC March 31, 2010 Effective October 1, 2010August 24, 2011CSO706 SDT Webinar3
CIP--002CIP002--4 Overview Version 4 of the CIP Standards Approved by Industry December 30, 2010 Submitted to FERC February 10, 2011 2,232 page filing Filing included CIP-002-4 through CIP-009-4, but onlychanges in CIP-002-4August 24, 2011CSO706 SDT Webinar4
Looking Ahead to Version 5 The SDT continues work to address theremaining 50 issues in Order 706 Version 5 builds on CIP-002-4 and previousdrafts of CIP-010 & 011 Use similar content structure and terminology asprevious CIP Standards (CIP-002 through CIP009)August 24, 2011CSO706 SDT Webinar5
Development GoalsGoal 1: To address the remainingRequirements-relatedqdirectives from allCIP related FERC orders, all approvedinterpretations, and CAN topics withinapplicable existing requirementsGoal 5: To minimize technical feasibilityexceptionspGoall 2:G2 ToT developdl consistenti t tidentification criteria of BES CyberSystems and application of cyber securityrequirements that are appropriate for theriski k presentedt d tto theth BESGoall 6:G6 ToT developdl requirementsit ththattfoster a “culture of security” and duediligence in the industry to complement a“culture of compliance”Goal 3: To provide guidance and contextGoal 7: To develop a realistic andcomprehensible implementation plan forthe industryfor each Standard RequirementGoal 4: To leverage current stakeholderinvestments used for complying withexisting CIP requirementsAugust 24, 2011CSO706 SDT Webinar6
Levels of Impact High Impact Large Control Centers CIP-003 through 009 Medium Impact Generation and Transmission Other Control Centers Si il tto CIPSimilarCIP-003003 tto 009 v44All other BES Cyber Systems Security Policy Security Awareness Incident Response Boundaryy ProtectionAugust 24, 2011CSO706 SDT Webinar7
Format (1/4) – Introductory Requirement RRequirement/measuresit/ffor implementedi lt dprocedures in most requirements Most requirements reference a tableimmediately belowAugust 24, 2011CSO706 SDT Webinar8
Format (2/4) – Contextual Boxes Rationale – Purposepofrequirement and anyassumptions made aboutthe requirement Summary of Changes –High level overview ofchanges in thisrequirement Guidance – Additionalguidance in applying therequirementAugust 24, 2011CSO706 SDT Webinar9
Format (3/4) – Requirement Row MMeasurementt specifiesifi acceptablet bl evidenceidoffcompliance associated with the requirement rowAugust 24, 2011CSO706 SDT Webinar10
Format (4/4) – Applicability All Responsible Entities High Impact BES Cyber Systems Medium Impact BES Cyber Systems External Connectivity Attributes –Routable or Dial-up connectivity Associated Electronic Access Control Systems –CIP-005-4 R1.5 Associated PhysicalyAccess Control Systemsy–CIP-006-4 R2 Associated Protected Cyber Systems –Non-CriticalNonCritical Cyber Assets within an ESPAugust 24, 2011CSO706 SDT Webinar11
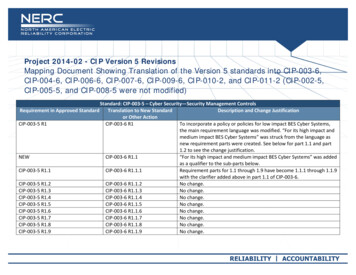
CIP--002CIP002--5 – CIPCIP--011011--5
CIP--002CIP002--5 Summary of Modifications Categorized list of High and Medium Impact Attachment 1 criteria OthOther BES CCyberb SSystemstddeemedd tto bbe LLowImpact by default Update required lists for significant changes toBES that affect High/Medium categorization Senior manager or delegate annual review andapprovalAugust 24, 2011CSO706 SDT Webinar13
CIP--002CIP002--5 Impact Criteria (Attachment 1) High: Large Control Centers (e.g. RC, BA, TOP) Medium: Significant impact field assets, otherControl Centers Other BES Cyber Systems deemed to be LowImpact by default Based on V4 criteria Review of Transmission voltage threshold by SDT forV5 Use of MVA bright-linegunder considerationAugust 24, 2011CSO706 SDT Webinar14
CIP--003CIP003--5 Summary of Modifications (1/2) CIP-003-5CIP 003 5 was reorganized to only includeelements of policy and cyber security programgovernance Elements that addressed Change Control andConfiguration Management were moved to CIP-010-5 Elements that address Information Protection weremoved to CIP-011-5August 24, 2011CSO706 SDT Webinar15
CIP--003CIP003--5 Summary of Modifications (2/2) Additional flexibility was added to the CyberSecurity Policy requirement by explicitly allowingfor multiple policies and specifying the topicalareas (as opposed to all requirements) that thepolicy must address The SDT has removed the requirement todocument exceptions to the policy, althoughdiscussions of this approach with FERC staff areongoingAugust 24, 2011CSO706 SDT Webinar16
CIP--003CIP003--5 Addressing FERC DirectivesFERCOrder 706Para.aa 33766“the Commission adoptsp its CIP NOPR pproposalpand directs the ERO to clarify that the exceptionsmentioned in Requirements R2.3 and R3 of CIP003-1 do not except responsible entities from theRequirements of the CIP Reliability StandardsStandards.” The SDT considers this a general managementissue that is not within the scope of a compliancerequirement. The SDT found no reliability basis in thisrequirement.requirement The SDT has proposed removing the requirementfor documented exceptions to the Cyber SecurityPolicy.August 24, 2011CSO706 SDT Webinar17
CIP--004CIP004--5 Summary of Modifications (1/3) Security Awareness Continues to be general awareness that is refreshedquarterly and not formal tracked training Training Addition of visitor control program electronic interconnectivity supporting the operation andcontrol of BES Cyber Systems storage media as part of the handling of BES CyberSystems information Reorganization of requirements into the respectiverequirements for “program” and “implementation” of thetraining.trainingAugust 24, 2011CSO706 SDT Webinar18
CIP--004CIP004--5 Summary of Modifications (2/3) Personnel Risk Assessment Changed to only initial identity verification Now includes documenting the processes used todetermine when to deny access Reorganization of requirements into the respectiverequirements for “program” and “implementation”August 24, 2011CSO706 SDT Webinar19
CIP--004CIP004--5 Summary of Modifications (3/3) Authorization Consolidated authorization and review requirementsfrom CIP-003-4, CIP-004-4, CIP-006-4 and CIP-007-4 Allow quarterly and annual reviews to find and fixproblems rather than self-report everything as aviolation Revocation RRemove abilitybilit tto access BES CCyberb SSystemtwhenhaccess no longer neededAugust 24, 2011CSO706 SDT Webinar20
CIP-004CIP004--5 Addressing FERC Directives((Training)g)FERC Order706 Para. 433FERC Order706 Para. 434FERC Order706 Para. 435““we direct the ERO to consider, in developing modifications to CIP-004-1, whetheridentification of core training elements would be beneficial and, if so, develop anappropriate modification to the Reliability Standard.”“The Commission adopts the CIP NOPR’s proposal to direct the ERO to modifyRequirement R2 of CIP-004-1 to clarify that cyber security training programs are intendedto encompass training on the networking hardware and software and other issues ofelectronic interconnectivity supporting the operation and control of critical cyber assets.”“ConsistentConsistent with the CIP NOPRNOPR, the Commission directs the ERO to determine whatwhat, ifany, modifications to CIP-004-1 should be made to assure that security trainers areadequately trained themselves.” The SDT addressed this by identifying the training topicsthat should be provided in the Training ProgramProgram. The SDT added this as a topic for role specific training. Take actions to remove the ability to access the BESCyber System when access is no longer requiredAugust 24, 2011CSO706 SDT Webinar21
CIP-004CIP004--5 Addressing FERC Directives((Immediate Revocation))FERCOrder 706Para.a a 46060“TheThe Commission adopts the CIP NOPR proposal to direct theERO to develop modifications to CIP-004-1 to require immediaterevocation of access privileges when an employee, contractor orvendor no longer performs a function that requires physical orelectronic access to a critical cyber asset for any reason (includingdisciplinary actionaction, transfertransfer, retirementretirement, or termination)termination).” Take actions to remove the ability to access theBES Cyber System when access is no longerrequiredi dAugust 24, 2011CSO706 SDT Webinar22
CIP--005CIP005--5 Summary of Modifications Define ‘External Connectivity’y for scopep modification Focus on ‘Electronic Access Points’ vs. ESP Require IDS at Control Centers Add clarity to ‘secure’ dialups CConsolidatedlid t d MMonitoringit i anddVVulnerabilitylbilitAssessment Requirements in CIP-007 and CIP-011respectivelypy Removed Appropriate Use Banner Incorporated CIP-005-4 Urgent Action revisionsAugust 24, 2011CSO706 SDT Webinar23
CIP-005CIP005--5 Addressing FERC Directives((2 Securityy Measures – Defense in Depth)p )FERCOrder 706Para.a a 49696“Commission adopts the CIP NOPR’s proposal to direct theERO to developde elop a reqrequirementirement that each responsible entitentitymust implement a defensive security approach includingtwo or more defensive measures in a defense in depthposture when constructing an electronic securityperimeter ”perimeter. Deploy methods to inspect communications anddetect potential malicious communications for allE tExternallCConnectivityti it (Intrusion(I t i DDetection)t ti )August 24, 2011CSO706 SDT Webinar24
CIP--006CIP006--5 Summary of Modifications PhysicalySecurityy Programg Must define the operational or procedural controls torestrict physical access Removed current “6 wall” wording to instead requireDefined Physical Boundary FFor HighHi h IImpact,t addeddd d theth needd tot utilizetili ttwo ormore different and complementary physical accesscontrols to restrict physical access Testing changed to a 24-month cycle with ongoingdiscussions of different cycles based on environmentAugust 24, 2011CSO706 SDT Webinar25
CIP--006CIP006--5 Addressing FERC DirectivesCommission adopts the CIP NOPR proposal to direct the ERO to modify this CIPFERC Order “TheReliability Standard to state that a responsible entity mustmust, at a minimumminimum, implement twomore different security procedures when establishing a physical security perimeter706 Para. 572 oraroundcritical cyber assets.” The SDT added this for High Impact BES Cyber AssetsFERC Order706 Para. 581“The C“ThCommissioni i adoptsd t ththe CIP NOPR proposall andd didirectst ththe ERO totdevelop a modification to CIP-006-1 to require a responsible entity to testthe physical security measures on critical cyber assets more frequently thanevery three years,.” The SDT changed to a 24 month testing cycle but isalso still discussing different cycles based onenvironmentAugust 24, 2011CSO706 SDT Webinar26
CIP--007CIP007--5 Summary of Modifications (1/2) Addition of physical I/O port requirement Security Patch mgt source requirement Non-prescriptive malware requirement Securityy Event Monitoringg failure handlingg Bi-weekly log summary/sampling reviewsAugust 24, 2011CSO706 SDT Webinar27
CIP--007CIP007--5 Summary of Modifications (2/2) Simplified accessaccess-controlcontrol requirements,removed TFE language while strengtheningpassword requirements Added requirement for maintenance devices CConsolidatedlid t d vulnerabilitylbilit assessmentt iin CIPCIP010-5 Disposal requirement moved to CIP-011-5August 24, 2011CSO706 SDT Webinar28
CIP-007CIP007--5 Addressing FERC Directives((Logg Review))FERC OrderOd706 Para. 525“The Commission adopts the CIP NOPR proposal to require the ERO tomodify CIP-005-1 to require logs to be reviewed more frequently than 90days, but clarifies its direction in several respects. At this time, theCommission does not believe that it is necessary to require responsibleentities to review logs daily ”FERC Order706 Para. 628“Requirement R6 of CIP-007-1 does not address the frequency with whichlog should be reviewed. Requirement R6.4 requires logs to be retained for90 calendar days. This allows a situation where logs would only be reviewed90 days after they are created. The Commission continues to believe that, ingeneral, logs should be reviewed at least weekly ” The SDT Proposes the performance of a review of logsummaries or samples every two weeks.August 24, 2011CSO706 SDT Webinar29
CIP-007CIP007--5 Addressing FERC Directives((Malware))FERC OrderOd706 Para. 620FERC Order706 Para. 622“The Commission will not adoptp Consumers’ recommendation that everyy systemyin an electronicsecurity perimeter does not need antivirus software. Critical cyber assets must be protected,regardless of the operating system being used. Consumers has not provided convincing evidencethat any specific operating system is not directly vulnerable to virus attacks. Virus technologychanges every day. Therefore we believe it is in the public interest to protect all cyber assetswithin an electronic security perimeter, regardless of the operating system being used ”“The Commission also directs the ERO to modify Requirement R4 to include safeguards againstpersonnel introducing, either maliciously or unintentionally, viruses or malicious software to acyber asset within the electronic security perimeter through remote access, electronic media, orother means, consistent with our discussion above. Rewrote the requirement as a competency basedrequirement that does not prescribe technology. Added Maintenance to cover malware onremovable media.August 24, 2011CSO706 SDT Webinar30
CIP-007CIP007--5 Addressing FERC Directives((Ports & Services))MarchMh 18thOrder onports/services“The Commission recognizes and encourages NERC’s intention toaddress physical ports to eliminate the current gap in protection as partof its ongoing CIP Reliability Standards project scheduled forcompletion by the end of 2010. Should this effort fail to address theissue, however, the Commission will take appropriate action, whichcould include directing NERC to produce a modified or new standardth t includesthati l d securityit off physicalh i l ports.”t ” The SDT proposes to address this directive byhaving a requirement to disable or restrict use ofphysicalh i l I/O portstAugust 24, 2011CSO706 SDT Webinar31
CIP--008CIP008--5 Summary of Modifications Defined Reportable Cyber Security Incident Working to harmonize with EOP-004-2 Includes additional specification on update andlessons learned associated with the responseplanlAugust 24, 2011CSO706 SDT Webinar32
CIP--008CIP008--5 Addressing FERC DirectivesFERCOrder 706Para.a a 66661“the Commission directs the ERO to develop a modification to CIP-008-1 to: (1)include language that takes into account a breach that may occur through cyber orphysical means; (2) harmonize, but not necessarily limit, the meaning of the termreportable incident with other reporting mechanisms, such as DOE Form OE 417;(3) recognize that the term should not be triggered by ineffectual and untargetedattacks that proliferate on the internet; and (4) ensure that the guidance languagethat is developed results in a Reliability Standard that can be audited andenforced.”fd”A11. Added: Reportable Cyber Security Incidents are either: Any malicious act or suspicious event or events that compromise, or was an attempt to compromise, the Electronic Security Perimeter orPhysical Security Perimeter of a BES Cyber System.orAny event or events which have either impacted or have the potential to impact the reliability of the Bulk Electric System (ReliabilityFunction CIP-002-5).2. Retired R1.3 which contained provisions for reporting Cyber Security Incidents. This is now addressed in EOP-004-2, Requirement 1, Part1 3 Will need1.3.d to givei iinstructioni to report as a “Reportable“Rbl CCyberb SSecurityi Event”E” ini EOPEOP-004004 space.3. See R1.1 above4. Guidance and measurements are being developed accordinglyAugust 24, 2011CSO706 SDT Webinar33
Slide 33A1Rework text format to be consistent with other slide formats (bullets and fonts).Applied to tother slides in CIP-008 and CIP-009 aswell.Author, 8/19/2011
CIP--008CIP008--5 Addressing FERC DirectivesFERCOrder 706Para.aa 66733“The Commission adopts the CIP NOPR proposal to directthe ERO to modifymodif CIPCIP-008-1008 1 to reqrequireire each responsibleentity to contact appropriate government authorities andindustry participants in the event of a cyber securityincident as soon as possible, but, in any event, within onehour of the event,event even if it is a preliminary reportreport.”Cyber Security - Incident Reporting and Response Planning: Retired R1.3which contained provisions for reporting Cyber Security Incidents. This isnow addressed in EOP-004-2, Requirement 1, Part 1.3 and Attachment 1August 24, 2011CSO706 SDT Webinar34
CIP--008CIP008--5 Addressing FERC DirectivesFERCOrder 706Para. 676“the Commission directs the ERO to modify CIP-008-1t requiretoi a responsibleibl entitytit tto, att a minimum,i inotifytifthe ESISAC and appropriate government authorities ofa cyber security incident as soon as possible, but, inany event, within one hour of the event, even if it is apreliminaryli ireport.”t ”– Cyber Security - Incident Reporting and Response Planning: Retired R1.3provisions for reportingpg CyberySecurityy Incidents. This iswhich contains paddressed in EOP-004-2, Requirement 1, Part 1.3.August 24, 2011CSO706 SDT Webinar35
CIP--008CIP008--5 Addressing FERC DirectivesFERCOrder 706Para.a a 686“The Commission adopts the CIP NOPR proposal to direct the ERO tomodify CIPCIP-008-1,008 1 Requirement R2 to require responsible entities tomaintain documentation of paper drills, full operational drills, andresponses to actual incidents, all of which must include lessonslearned.The Commission further directs the ERO to include language inCIP-008-1 to require revisions to the incident response plan to addressththesellessonsllearned.”d ”R3.3 and R3.4 Includes additional specification on update of response planAddresses FERC Requirement (686) to modify on lessons learned andaspects of the DHS ControlsAugust 24, 2011CSO706 SDT Webinar36
CIP--009CIP009--5 Summary of Modifications Added requirement to implement the responseplan Verification of backup media information prior tostorage PreservationPti off datad t forf analysisl iAugust 24, 2011CSO706 SDT Webinar37
CIP--009CIP009--5 Addressing FERC DirectivesFERCOrder 706Para.a a 69694“For the reasons discussed in the CIP NOPR, the Commission adoptsthe proposal to direct the ERO to modify CIPCIP-009-1009 1 to include a specificrequirement to implement a recovery plan.We further adopt theproposal to enforce this Reliability Standard such that, if an entity hasthe required recovery plan but does not implement it when theanticipated event or conditions occur, the entity will not be incomplianceliwithith thisthi ReliabilityR li bilit StStandard”d d”Added specific R1 requirement to implement recovery planAugust 24, 2011CSO706 SDT Webinar38
CIP--009CIP009--5 Addressing FERC DirectivesFERCOrder 706Para.a a 73939“The Commission adopts the CIP NOPR proposal to direct the ERO tomodify CIP- 009-1 to incorporate guidance that the backup andrestoration processes and procedures required by Requirement R4should include, at least with regard to significant changes made to theoperational control system, verification that they are operational beforeth backupstheb kare storedt d or reliedli d upon ffor recovery purposes.””R1.5 Added requirements related to restoration processes based on review ofthe DHS ControlsAugust 24, 2011CSO706 SDT Webinar39
CIP--009CIP009--5 Addressing FERC DirectivesFERCOrder 706Para. 748“The Commission adopts the CIP NOPR proposal to directthe ERO to modify CIP-009-1 to provide direction thatb k practicesbackuptiincludei l d regularl proceduresdtto ensureverification that backups are successful and backupfailures are addressed, so that backups are available forfuture use.”R1.5 : Processes for the restoration of BES Cyber Systems to the mostcurrentt baselinebli configurationfitiAugust 24, 2011CSO706 SDT Webinar40
CIP--009CIP009--5 Addressing FERC DirectivesFERCOrder 706Para. 706“Preserve data for analysis”CIP-009-5 1.6Requires process to preserve data for analysisAugust 24, 2011CSO706 SDT Webinar41
CIP--010CIP010--5 Requirements Summary The SDT proposes the development of a newStandard CIP-010-5 that consolidates allreferences to Configuration ChangeManagement and Vulnerability Assessments. Previously these requirements were dispersedthroughout CIP-003-4, CIP-005-4, and CIP-007-4August 24, 2011CSO706 SDT Webinar42
CIP--010CIP010--5 Requirements Summary The SDT has made changes the VulnerabilityAssessment requirements to: Consolidate the previous requirements in CIP-005-4CIP 005 4and CIP-007-4 into a single requirement Make pprovisions for differences between ControlCenters and field assets Respond to FERC Order 706 regarding theperformance of “active vulnerability assessments”August 24, 2011CSO706 SDT Webinar43
CIP--010CIP010--5 Addressing FERC DirectivesFERCOrder 706Para.a a 39397“The Commission directs the ERO to develop modificationsto RequirementReq irement R6 of CIPCIP-003-1003 1 to providepro ide an eexpresspressacknowledgment of the need for the change control andconfiguration management process to consider accidentalconsequences and malicious actions along with intentionalchanges ”changes. The SDT proposes the introduction of a defined baseline configurationand an explicit requirement for monitoring for changes to the baselineconfigurationgin Highg ImpactpControl Centers in order to capturepmalicious changes to a BES Cyber System. Additionally, the SDT proposes that changes to High Impact ControlCenters be tested in a test environment prior to their implementation inthe production environment to aid in identifying any accidentalconsequences of the change.August 24, 2011CSO706 SDT Webinar44
CIP--010CIP010--5 Addressing FERC DirectivesFERC Order706 Para. 609FERC Order706 Para. 610FERC Order706 Para. 611“WeWe therefore direct the ERO to develop requirements addressing what constitutes a“representative system” and to modify CIP-007-1 accordingly. The Commission directsthe ERO to consider providing further guidance on testing systems in a referencedocument.”“we direct the ERO to revise the Reliability Standard to require each responsible entity todocument differences between testing and production environments in a mannerconsistent with the discussion above.”“the Commission cautions that certain changes to a production or test environment mightmake the differences between the two greater and directs the ERO to take this intoaccount when developing guidance on when to require updated documentation to ensurethat there are no significant gaps between what is tested and what is in production.” The SDT proposes to require a “representative system” or test system for those High Impact ControlCenters to use for the purposes of testing proposed changes and performing active vulnerabilityassessments. The SDT proposes using the defined baseline configuration of a BES Cyber System for the measuringstick as to whether a test system is truly representative of the production system. To account for any additional differences between the two systems, the SDT proposes using the wordsdirectly from FERC Order 706 “Document the differences between the test environment and theproductionpoduc o eenvironmento e includingc ud g a descdescriptionp o oof thee measureseasu es used too accouaccount foro aanyyddifferencese e ces inoperation between the test and production environments.”August 24, 2011CSO706 SDT Webinar45
CIP--010CIP010--5 Addressing FERC DirectivesFERC Order706 Para. 541“we adopt the ERO’s proposal to provide for active vulnerabilityassessments rather than full live vulnerability assessments.”FERC Order706. Para 542“the Commission adopts the ERO’s recommendation of requiring activevulnerability assessments of test systems.”FERC Order706 Para. 547“we direct the ERO to modify Requirement R4 to require theserepresentativepactive vulnerabilityy assessments at least once everyythree years, with subsequent annual paper assessments in theintervening years” The SDT has added requirements for an “active vulnerability”assessment to occur at least once everyy three yyears for Highg ImpactpControl Centers using a test system so as to prevent unforeseenimpacts on the Bulk Electric System.August 24, 2011CSO706 SDT Webinar46
CIP--010CIP010--5 Addressing FERC DirectivesFERC OrderOd706 Para. 544FERC Order706 Para. 544“thethe Commission directs the ERO to revise the Reliability Standardso that annual vulnerability assessments are sufficient, unless asignificant change is made to the electronic security perimeter ordefense in depth measure, rather than with every modification.”“we are directing the ERO to determine, through the ReliabilityStandards development process, what would constitute amodification that would require an active vulnerability assessment” The SDT has proposed that prior to adding a newcyber asset into a BES Cyber System, that thenew cyber asset undergo an active vulnerabilityassessment. An exception is made for specified exceptionalcircumstances such as an emergency.August 24, 2011CSO706 SDT Webinar47
CIP--011CIP011--5 Requirements Summary The SDT proposes the development of a newStandard CIP-011-5 that consolidates all referencesto Information Protection and Media Sanitization Previously these requirements were dispersed throughoutCIP-003-4 and CIP-007-4 The SDT has also moved the requirementsregarding the authorization and revocation of accessto BES Cyber System Information to CIP-004-5CIP-004-5,consolidating these requirements with those forelectronic and physical accessAugust 24, 2011CSO706 SDT Webinar48
CIP--011CIP011--5 Requirements Summary The SDT has introduced a definition of aglossary term “BES Cyber System Information”which defines what needs to be protected Previously, this list was a requirement itselfAugust 24, 2011CSO706 SDT Webinar49
CIP--011CIP011--5 Summary The SDT has shifted the focus of therequirements for media sanitization from theCyber Asset to the information itself In version 4, these requirements are invoked whenthe Critical Cyber Asset is to be disposed of orredeployedp y In version 5, the requirement is triggered when either: BES CyberySystemyInformation no longerg needs to be storedon specific media, or Media containing BES Cyber System Information isgfor disposalpdesignatedAugust 24, 2011CSO706 SDT Webinar50
CIP--011CIP011--5 Addressing FERC DirectivesFERC OrderOd706 Para. 633“The Commission adopts the CIP NOPR proposal todirect the EROO to clarifyf what it means to preventunauthorized retrieval of data from a cyber asset prior todiscarding it or redeploying it.”FERC Order706 Para 635“thethe Commission directs the ERO to revise RequirementR7 of CIP-007-1 to clarify, consistent with thisdiscussion, what it means to prevent unauthorizedretrieval of data.” The SDT has proposed that preventing unauthorizedretrieval of data means to “render the data unrecoverable.” The SDT understands that this mayy be too highg of a barand is continuing discussions in this area.August 24, 2011CSO706 SDT Webinar51
Implementation Plan Implementationppplan is in the veryy earlyypphases ofdevelopment Current concepts include staggered Effective Dates for: CIP-002-5 Organizational Requirements (CIP-003-5, CIP-008-5) Technical Requirements (CIP(CIP-005-5,005 5 CIPCIP-006-5,006 5 etcetc.)) Technical Requirements would be further staggered by: High Impact BES Cyber Systems Medium Impact BES Cyber SystemspCyberySystemsy Low ImpactAugust 24, 2011CSO706 SDT Webinar52
Implementation Plan Currently evaluating a single implementationplan that would include compliance timelines forfuture newly identified BES Cyber Systems andthose BES Cyber Systems that changecategories Eliminates the separate Implementation Plan forNewly Identified Critical Cyber Assets and NewlyRegistered Entities (IPFNICCANRE)August 24, 2011CSO706 SDT Webinar53
Schedule to Date – 2011SeptemberAugustJuly Meet with IndustryRepresentatives Prepare forNERC QualityReview Meet with FERCStaffJuly Walk-through ofGeneration andTransmissionEnvironmentsJune RegionalAudit StaffAugust 24, 2011CSO706 SDT Webinar54
Key Dates Moving Forward November 3rd, 2011 –First Posting for Comment and Ballot Webinars – November 15th and 29th, 2011 Ballot Opensp– December 9th, 2011 Ballot Closing – December 19th, 2011August 24, 2011CSO706 SDT Webinar55
Questions?Points of Contact:Philip Huff – philip.huff@aecc.comDoug Johnson – douglas.johnson@comed.comDavid Revill – david.revill@gatrans.comSlides and Recording of Webinar will be Posted(on NERC Website)
V5 Use of MVA bright-line under consideration August 24, 2011 CSO706 SDT Webinar 14. CIPCIP--003003--5 Summary of Modifications (1/2)5 Summary of Modifications (1/2) . from CIP-003-4, CIP-004-4, CIP-006-4 and CIP-007-4 Allow quarterly and annual reviews to find and fix problems rather than self-report everything as a violation