Transcription
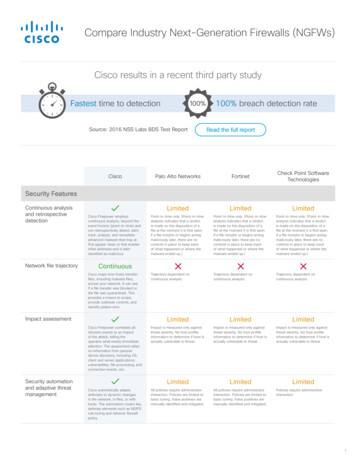
Compare Industry Next-Generation Firewalls (NGFWs)Cisco results in a recent third party studyFastest time to detection100%Source: 2016 NSS Labs BDS Test Report100% breach detection rateRead the full reportFortinetCheck Point SoftwareTechnologiesCiscoPalo Alto NetworksLimitedLimitedLimitedCisco Firepower employscontinuous analysis, beyond theevent horizon (point-in-time) andcan retrospectively detect, alert,track, analyze, and remediateadvanced malware that may atfirst appear clean or that evadesinitial defenses and is lateridentified as malicious.Point-in-time only. (Point-in-timeanalysis indicates that a verdictis made on the disposition of afile at the moment it is first seen.If a file morphs or begins actingmaliciously later, there are nocontrols in place to keep trackof what happened or where themalware ended up.)Point-in-time only. (Point-in-timeanalysis indicates that a verdictis made on the disposition of afile at the moment it is first seen.If a file morphs or begins actingmaliciously later, there are nocontrols in place to keep trackof what happened or where themalware ended up.)Point-in-time only. (Point-in-timeanalysis indicates that a verdictis made on the disposition of afile at the moment it is first seen.If a file morphs or begins actingmaliciously later, there are nocontrols in place to keep trackof what happened or where themalware ended up.)Cisco maps how hosts transferfiles, including malware files,across your network. It can seeif a file transfer was blocked orthe file was quarantined. Thisprovides a means to scope,provide outbreak controls, andidentify patient zero.Trajectory dependent oncontinuous analysis.Trajectory dependent oncontinuous analysis.Trajectory dependent oncontinuous analysis.LimitedLimitedLimitedCisco Firepower correlates allintrusion events to an impactof the attack, telling theoperator what needs immediateattention. The assessment relieson information from passivedevice discovery, including OS,client and server applications,vulnerabilites, file processing, andconnection events, etc.Impact is measured only againstthreat severity. No host profileinformation to determine if host isactually vulnerable to threat.Impact is measured only againstthreat severity. No host profileinformation to determine if host isactually vulnerable to threat.Impact is measured only againstthreat severity. No host profileinformation to determine if host isactually vulnerable to threat.LimitedLimitedLimitedAll policies require administratorinteraction. Policies are limited tobasic tuning. False positives aremanually identified and mitigated.All policies require administratorinteraction. Policies are limited tobasic tuning. False positives aremanually identified and mitigated.Security FeaturesContinuous analysisand retrospectivedetectionNetwork file trajectoryContinuousImpact assessmentSecurity automationand adaptive threatmanagementCisco automatically adaptsdefenses to dynamic changesin the network, in files, or withhosts. The automation covers keydefense elements such as NGIPSrule tuning and network firewallpolicy.Policies require administratorinteraction.1
CiscoPalo Alto NetworksFortinetCheck Point SoftwareTechnologiesLimitedLimitedLimitedSecurity Features (continued)Behavioral indicatorsof compromise (IoCs)User, network, andendpoint awarenessCisco Firepower considers filebehavior and the reputation ofsites, and correlates network andendpoint activity using 1000behavioral indicators. It providesbillions of malware artifacts forunmatched scale and coveragefrom global threats.Standard, nonbehavioral IoCs areavailable in separate product.Cisco Firepower provides fullcontextual threat analysis andprotection, with awareness intousers, user history on everymachine, mobile devices, clientside applications, operatingsystems, virtual machine-tomachine communications,vulnerabilities, threats, and URLs.User awareness only.LimitedNext-genNGIPSSignature-basedIoCs are based upon threatseverity, not behavior.IoCs are based upon threatseverity, not behavior.LimitedLimitedUser awareness only unlessseparate endpoint software isused.User awareness only unlessseparate endpoint software on IPS with realtime contextual awareness andnetwork mapping.Integrated advancedthreat protectionLimitedLimitedLimitedBuilt-in, dynamic sandboxingcapabilities (AMP-ThreatGrid),detects evasive and sandboxaware malware, actionable eventcorrelations, 1000 behavioralIoCs, billions of malware artifacts,and easy-to-understand threatscores.Sandbox available as cloudsubscription or ent automation from CiscoAMP for Networks allows you toquickly understand, scope, andcontain an active attack evenafter it happens.No root cause or trajectory resultsin an unknown threat scope.Remediation is a manual processduring post-breach incidentresponse.No root cause or trajectory resultsin an unknown threat scope.Remediation is a manual processduring post-breach incidentresponse.No root cause or trajectory resultsin an unknown threat scope.Remediation is a manual processduring post-breach incidentresponse.Malware remediationSandbox available as cloudsubscription or on-premisesappliance.Sandbox available as cloudsubscription or on-premisesappliance.DID YOU KNOW?More than 23% of organizations have vulnerabilitiesdating back to 2011.Don’t be one of them(Source: 2016 Midyear Cybersecurity Report)2
CiscoPalo Alto NetworksFortinetCheck Point SoftwareTechnologiesUnique malwaresamples per day1.5 million10s of thousands10s of thousands10s of thousandsThreats blocked perday19.7 billionNot reportedNot reportedNot reportedNot reported6 millionNot reportedNot reported35 millionNot reportedThreat Intelligence (Talos)Email messagesscanned per dayWeb requestsmonitored per dayAutomatedintelligence feedsExcludes email600 billionOf the 600B scanned, more than85% are spam.16 billionWeb requests monitored by WSA/CWS per day. For perspective,Google processes 3.5 billionsearches per day.Security intelligence feeds areupdated every 2 hours, adjustableto 5-minute intervals.DID YOU KNOW?Cisco Talos consists of over 250 researchers,making it one of the largest threat intelligenceorganizations in the world.See what they doCiscoPalo Alto NetworksFortinetCheck Point SoftwareTechnologiesOptiFlowTMSingle passASICMultipassOperational CapabilitiesScanning architectureSoftware-definedsegmentationAutomatic threatcontainmentOperations andmanagementCisco TrustSec and ACI provisionsecurity services separatedfrom workload and deployment(physical, virtual, cloud). Securitygroup tags (SGTs) segmentsoftware in the network.Cisco Rapid Threat Containmentautomates quarantine actionsby the Cisco Identity bined security and networkoperations. One console or HApair of consoles provides allupdates, patching, reporting, andthreat information.Single UI for NGFW management.Additional UIs for malware,endpoint, or any other platformfeatures.Single UI for NGFW management.Additional product and UI forlogging and events. Additionalproduct and UI for sandboxing.Single manager of managers foreach individual function of NGFW,ATP, etc.3
Palo Alto NetworksFortinetCheck Point pliance, virtual instance(VMware), and public cloud (AWSand Azure)Appliance, virtual instance(VMware), and public cloud (AWSand Azure)Appliance, virtual instance(VMware), and public cloud (AWSand Azure)Appliance, virtual instance(VMware), and public cloud (AWSand Azure)CiscoOperational Capabilities (continued)Deployment modelseStreamer APICisco Firepower can stream eventdata and host-profile informationto client applications, SIEM andSOC platforms, enhancing youractionable intelligence.Remediation APICisco Firepower can work inconjunction with third-partyproducts. It can change anasset’s VLAN or access controls,or even open a ticket with thehelp desk.Host APIOther systems such as inventory,vulnerability & asset management,and Nmap can feed data into theCisco Firepower platform.DID YOU KNOW?The average cost of a breach is 1.57 millionCiscoLearn morePalo Alto NetworksFortinetCheck Point SoftwareTechnologiesNGFW onlyNGFW onlyNGFW onlyCritical Infrastructure (ICS/SCADA)Hardened andruggedized versionsavailableBase feature setNGFW, AMP,NGIPS, threatintelligenceNGFW includes applicationvisibility, URL filtering, IPS,antivirus, user identity. Firepoweralso includes all key securityenhancements mentioned above,such as NGIPS, AdvancedMalware Protection (AMP),retrospection, impact analysis,etc.4
CiscoPalo Alto NetworksFortinetCheck Point SoftwareTechnologies 300 180Critical Infrastructure (ICS/SCADA) (continued)SCADA rules 250 100 250 rules based on Snort. Talosprovides rules geared towardICS industry. Third-party rulescan be imported. Customers canbuild rules.Modbus, DNP, CIPpre-processorsModbus, DNP3, and BACnet.SCADA protocols are availablethrough the Firepower system.Modbus, DNP3, OPC, ICCP, IEC61850Modbus, DNP3, BACNet,MMS, OPC, Profinet, ICCP,IEC.60870.5.104, IEC.61850Modbus, DNP3, BACNet,MMS, OPC, Profinet, ICCP,IEC.60870.5.104, IEC.61850Service ProviderCarrier-classcertificationNEBS Level 3NEBS Level 3GTP v2, CG-NAT, Diameter,SCTP, SIP-signaling firewallGTP v2, CG-NAT, Diameter,SCTP, SIP-signaling firewallCarrier-class featuresThird-party servicesstitchingGTP v2, CG-NAT, Diameter,SCTP, SIP-signaling firewallThird-party and native containerscan be seamlessly stitchedtogether to run with FirepowerThreat Defense.LimitedTrue DDoSRadware DefensePro vDOScontainer is integrated directlyinto the NGFW system (CiscoFirepower 9300).Requires separate product.LimitedRequires separate product. 2018 Cisco and/or its affiliates. All rights reserved. Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company.5
Compare Industry Next-Generation Firewalls (NGFWs) Continuous analysis and retrospective detection Cisco Firepower employs continuous analysis, beyond the event horizon (point-in-time) and can retrospectively detect, alert, track, analyze, and remediate advanced malware that may at first appear clean or that evades initial defenses and is later