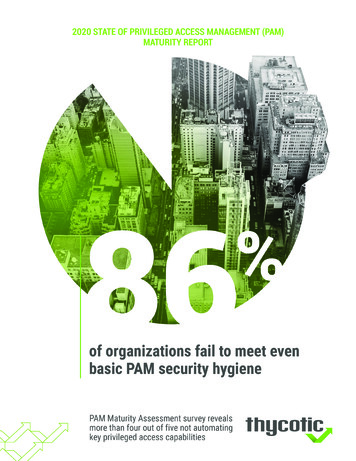
Transcription
Solution BriefPrivileged ActivityDetect and respond tounusual behavior by privilegedaccounts, critical assets, andprivileged processesA top target for bad actorsPrivileged accounts pose one of the largest securityrisks for organizations. According to a Ponemonreport, 14% of incidents involved the abuse ofprivileged users’ access, costing organizations,on average, 2.79 million annually1. Compared tostandard users, privileged accounts like admin orexecutive accounts have extensive control overaccess to sensitive data and IT systems, such asdomain controllers or Active Directory.Having unrestricted access to critical IT systemsand other valuable assets makes privilegedaccounts a top target for attackers. If an attackercan compromise a privileged account, the attackergains access that could be used to disrupt corporateoperations, or exfiltrate large amounts ofsensitive data.Bad guys are going after privilegedusers. Privileged users have accessto your sensitive data, and they haveaccess to the keys to your kingdom.And that’s what you really wantto protect.David MadhiGartner Security RiskManagement Summit, 202012020 Global Cost of Insider Threats; Ponemon Institute
Solution BriefPrivileged ActivityExabeam and privileged activityExabeam helps security teams outsmart adversariescompromising privileged accounts with the supportof automation and pre-packaged use case contentacross the full analyst workflow, from detectionto response. First, we prescribe the data sourcesto collect and analyze which provide the greatestvisibility over privileged activity. Our user and entitybehavior analytics (UEBA) then develops a baseline ofnormal activity for every privileged account and assetin an organization. As an adversary begins to movewithin a network, abnormal activity is identified usingpre-packaged detection rules and models, includingMITRE techniques associated with privileged activity.This activity is flagged and added to the user orentity’s risk score. Risk scores and watchlists helpsecurity teams focus on the riskiest incidents, whileExabeam Smart Timelines automatically display thefull attack chain to dramatically accelerate incidentinvestigations. A guided investigation checklist andautomated response playbooks enable analyststo quickly and effectively remediate incidents andreduce mean time to respond (MTTR).Key capabilitiesPrivileged accounts are also associated with assets,providing the context needed to identify whetherthe asset is a laptop or server, and if it belongs to anexecutive. Understanding context enables analyststo identify privileged activity, like a non-executiveuser accessing an executive asset or a user who hasbeen given mailbox permissions for an executiveuser. Since privileged users pose a great risk to anorganization, Exabeam enables analysts to discernwhether the privileged account or asset is behavingsuspiciously and detect privileged activity.BenefitStrengthen your security posture with the ability todetect adversary activity on privileged accountsor assets.Figure 1 – Exabeam provides context within a user or asset profile.From the user’s profile, an analyst can quickly understand if theasset or user has privileged access, in this case, Rob Koch hasbeen tagged as a privileged user.Challenge 1: Collection and DetectionWithout the ability to automatically identifyprivileged accounts and assets, traditional securitytools struggle to detect attacks involvingprivileged activity.SolutionExabeam ingests context from directory servicesplatforms and other systems to identify and classifyprivileged accounts such as domain controllers,admins, and executives. Through behavioralmodeling of users and assets, Exabeam automaticallybaselines normal activity, assigns a risk score tosuspicious events, and intelligently prioritizes themfor further evaluation. Identifying privileged accounts,such as an executive or IT admin, allows the system tomodel privileged users and assets and add additionalrisk to anomalous behaviors associated with them.exabeam.com02
Solution BriefPrivileged ActivityChallenge 2: Visibility and InvestigationChallenge 3: ResponseSecurity teams do not have visibility into privilegedactivity, or the ability to continuously monitorprivileged users for privileged activity.Security teams responding to privileged activityinvestigations spend hours or days coordinating aresponse across multiple security tools.SolutionSolutionExabeam gives complete visibility into privilegedactivity attacks by aggregating security alertsand events together into a user or entity timeline.Timelines leverage patented host-IP-user mappingto automatically assemble a user or entity’s activity,anomalous and normal, into clear, readable events,all without an analyst needing to write a single query(figure 2). Analysts can access the timelines from acurated watchlist that centralizes privileged usersand assets for continuous monitoring. For furtherinvestigation, Exabeam provides a behavior-basedthreat hunting tool capable of honing in on theabnormal activity associated with privilege activitythreats, for example, an analyst can search fornon-executive users accessing executive assetsor disabled users showing activity. Each step of theway, analysts can reference our privileged activitychecklist to ensure their investigation is thoroughand complete.Exabeam orchestrates response to privileged activityincidents across your security stack (figure 3) usingresponse actions and playbooks. Pre-packagedintegrations with hundreds of popular securityand IT products and customizable actions enablesecurity teams to automate playbooks to respond toprivileged activity incidents, such as suspending auser or resetting a password.BenefitImprove operational efficiency and decrease MTTRwith security orchestration automation and response(SOAR) powered playbooks.BenefitQuickly and easily identify leading indicators ofcompromise across your entire security stack andimprove investigation quality and speed by enablinganalysts to quickly answer key questions like “Is thereactivity from a disabled user” or “Did a new or nonprivileged user access an executive asset?”Figure 3 – This privileged activity playbook characterizes andescalates the incident, adds the compromised user to a watchlistwhile disabling their account, and resets their password.Figure 2 – This Smart Timeline event shows compromisedinsider Rob Koch performing an anomalous remote login to theexecutive asset us-crm-srv1.exabeam.com03
Solution BriefPrivileged ActivityUse case contentIncident ChecklistTo provide coverage for privileged activity, Exabeamidentified key data sources and has built content forcollection, detection, investigation and response.Key Data Sources Asset logon and access Authentication and access management VPN and zero trust network access Application activity Privileged access management and activity File monitoring Remote logon activity DLP alerts Web activityFigure 4 – The privileged activity incident checklist promptsanalysts to answer specific investigation questions and takecontainment actions.Key Detection Rule Types Abnormal activity on domain controllers Executive account activity Privileged account activity Disabled account activity Privileged asset activity Privileged process executionMITRE Technique & Tactic Coverage T1078: Valid Accounts T1059: Command and Scripting Interpreter T1204: User Execution T1003: OS Credential Dumpingexabeam.com04
Solution BriefPrivileged ActivityResponse Actions Contact user/manager/HR department via email Add user or asset to a watchlist Block, suspend, or impose restrictions on usersinvolved in the incident Rotate credentials/expire/reset password Prompting for re-authentication via 2-factor/multifactor authentication Remove user from group Clear user session Get asset/user/process info Kill processAbout ExabeamExabeam helps security teams outsmartthe odds by adding intelligence to theirexisting security tools – including SIEMs,XDRs, cloud data lakes, and hundreds ofother business and security products. Outof-the-box use case coverage repeatedlydelivers successful outcomes. Behavioralanalytics allows security teams to detectcompromised and malicious users thatwere previously difficult, or impossible,to find. Automation helps overcome staffshortages by minimizing false positives anddramatically reducing the time it takes todetect, triage, investigate and respond. Formore information, visit exabeam.com.To learn more about how Exabeam can helpyou visit exabeam.com today.EXA-Privileged-Activity-SB rev 4/23/21
model privileged users and assets and add additional risk to anomalous behaviors associated with them. Figure 1 - Exabeam provides context within a user or asset profile. From the user's profile, an analyst can quickly understand if the asset or user has privileged access, in this case, Rob Koch has been tagged as a privileged user.