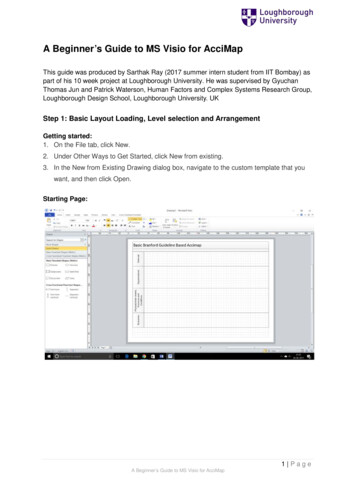
Transcription
A Beginner’s Guide toNetwork SecurityAn Introduction to the Key Security Issues for the E-Business EconomyWith the explosion of the public Internet and e-commerce, private computers, and computer networks, if notadequately secured, are increasingly vulnerable to damaging attacks. Hackers, viruses, vindictive employeesand even human error all represent clear and present dangers to networks. And all computer users, from themost casual Internet surfers to large enterprises, could be affected by network security breaches. However,security breaches can often be easily prevented. How? This guide provides you with a general overview of themost common network security threats and the steps you and your organization can take to protectyourselves from threats and ensure that the data traveling across your networks is safe.Cisco SystemsCopyright 2001 Cisco Systems, Inc. All Rights Reserved.Page 1 of 9
Importance of SecurityThe Internet has undoubtedly become the largest publicdata network, enabling and facilitating both personal andbusiness communications worldwide. The volume oftraffic moving over the Internet, as well as corporatenetworks, is expanding exponentially every day. Moreand more communication is taking place via e-mail;mobile workers, telecommuters, and branch offices areusing the Internet to remotely connect to their corporatenetworks; and commercial transactions completed overthe Internet, via the World Wide Web, now account forlarge portions of corporate revenue.While the Internet has transformed and greatly improvedthe way we do business, this vast network and its associatedtechnologies have opened the door to an increasing numberof security threats from which corporations must protectthemselves. Although network attacks are presumably moreserious when they are inflicted upon businesses that storesensitive data, such as personal medical or financial records,the consequences of attacks on any entity range from mildlyinconvenient to completely debilitating—important datacan be lost, privacy can be violated, and several hours,or even days, of network downtime can ensue.Despite the costly risks of potential security breaches, theInternet can be one of the safest means by which toconduct business. For example, giving credit cardinformation to a telemarketer over the phone or a waiterin a restaurant can be more risky than submitting theinformation via a Web site, because electronic commercetransactions are usually protected by security technology.Waiters and telemarketers are not always monitored ortrustworthy. Yet the fear of security problems can be justas harmful to businesses as actual security breaches.General fear and suspicion of computers still exists andwith that comes a distrust of the Internet. This distrust canlimit the business opportunities for companies, especiallythose that are completely Web based. Thus, companiesmust enact security policies and instate safeguards thatnot only are effective, but are also perceived as effective.Organizations must be able to adequately communicatehow they plan to protect their customers.In addition to protecting their customers, corporationsmust protect their employees and partners from securitybreaches. The Internet, intranets, and extranets enablefast and effective communication between employees andpartners. However, such communication and efficiencycan of course be impeded by the effects of a networkattack. An attack may directly cause several hours ofdowntime for employees, and networks must be takendown in order for damage to be repaired or data to berestored. Clearly, loss of precious time and data cangreatly impact employee efficiency and morale.Legislation is another force that drives the need fornetwork security. Governments recognize both theimportance of the Internet and the fact that substantialportions of the world’s economic output are dependenton it. However, they also recognize that opening up theworld’s economic infrastructure to abuse by criminalscould cause major economic damage. Nationalgovernments are therefore developing laws intendedto regulate the vast flow of electronic information.Furthermore, to accommodate the regulations enactedby governments, the computer industry has developed aportfolio of security standards to help to secure data andto prove that it is secure. Businesses that do not havedemonstrable security policies to protect their data will bein breach of these standards and penalized accordingly.“I have found that inadequate network security isusually caused by a failure to implement securitypolicies and make use of security tools that arereadily available. It's vital that companies completeprofessional risk assessments and developcomprehensive security plans and infrastructuresthat are publicly supported by upper management.”—Mark Carter, COO, CoreFacts, LLC, Data Recovery andAnalysis FirmCisco SystemsCopyright 2001 Cisco Systems, Inc. All Rights Reserved.Page 2 of 9
Threats to DataAs with any type of crime, the threats to the privacyand integrity of data come from a very small minorityof vandals. However, while one car thief can steal onlyone car at a time, a single hacker working from a basiccomputer can generate damage to a large number ofcomputer networks that wreaks havoc around the world.Perhaps even more worrisome is the fact that the threatscan come from people we know. In fact, most networksecurity experts claim that the majority of networkattacks are initiated by employees who work inside thecorporations where breaches have occurred. Employees,through mischief, malice, or mistake, often manage todamage their own companies’ networks and destroy data.Furthermore, with the recent pervasiveness of remoteconnectivity technologies, businesses are expanding toinclude larger numbers of telecommuters, branch offices,and business partners. These remote employees andpartners pose the same threats as internal employees,as well as the risk of security breaches if their remotenetworking assets are not properly secured and monitored.Whether you want to secure a car, a home, a nation, ora computer network, a general knowledge of who thepotential enemies are and how they work is essential.Who are the enemies?HackersThis generic and often over-romanticized term applies tocomputer enthusiasts who take pleasure in gaining accessto other people’s computers or networks. Many hackersare content with simply breaking in and leaving their“footprints,” which are joke applications or messages oncomputer desktops. Other hackers, often referred to as“crackers,” are more malicious, crashing entire computersystems, stealing or damaging confidential data, defacingWeb pages, and ultimately disrupting business. Someamateur hackers merely locate hacking tools online anddeploy them without much understanding of how theywork or their effects.Unaware StaffAs employees focus on their specific job duties, they oftenoverlook standard network security rules. For example,they might choose passwords that are very simple toremember so that they can log on to their networks easily.However, such passwords might be easy to guess or crackby hackers using simple common sense or a widelyavailable password cracking software utility. Employeescan unconsciously cause other security breaches includingthe accidental contraction and spreading of computerviruses. One of the most common ways to pick up a virusis from a floppy disk or by downloading files from theInternet. Employees who transport data via floppy diskscan unwittingly infect their corporate networks withviruses they picked up from computers in copy centers orlibraries. They might not even know if viruses are residenton their PCs. Corporations also face the risk of infectionwhen employees download files, such as PowerPointpresentations, from the Internet. Surprisingly, companiesmust also be wary of human error. Employees, whetherthey are computer novices or computer savvy, can makesuch mistakes as erroneously installing virus protectionsoftware or accidentally overlooking warnings regardingsecurity threats.“Ninety-one percent of respondents detected employeeabuse of Internet access privileges.”—Annual Computer Security Institute and FBI Survey, 2001Disgruntled StaffFar more unsettling than the prospect of employee errorcausing harm to a network is the potential for an angry orvengeful staff member to inflict damage. Angry employees,often those who have been reprimanded, fired, or laid off,might vindictively infect their corporate networks withviruses or intentionally delete crucial files. This group isespecially dangerous because it is usually far more awareof the network, the value of the information within it,where high-priority information is located, and thesafeguards protecting it.SnoopsWhether content or disgruntled, some employees mightalso be curious or mischievous. Employees known as“snoops” partake in corporate espionage, gainingunauthorized access to confidential data in order toprovide competitors with otherwise inaccessibleinformation. Others are simply satisfying their personalcuriosities by accessing private information, such asfinancial data, a romantic e-mail correspondence betweencoworkers, or the salary of a colleague. Some of theseactivities might be relatively harmless, but others, such asCisco SystemsCopyright 2001 Cisco Systems, Inc. All Rights Reserved.Page 3 of 9
previewing private financial, patient, or human resourcesdata, are far more serious, can be damaging to reputations,and can cause financial liability for a company.What can these enemies do?VirusesViruses are the most widely known security threats,because they often garner extensive press coverage.Viruses are computer programs that are written bydevious programmers and are designed to replicatethemselves and infect computers when triggered by aspecific event. For example, viruses called macro virusesattach themselves to files that contain macro instructions(routines that can be repeated automatically, such as mailmerges) and are then activated every time the macro runs.The effects of some viruses are relatively benign and causeannoying interruptions such as displaying a comicalmessage when striking a certain letter on the keyboard.Other viruses are more destructive and cause suchproblems as deleting files from a hard drive or slowingdown a system.A network can be infected by a virus only if the virusenters the network through an outside source—mostoften through an infected floppy disk or a file downloadedfrom the Internet. When one computer on the networkbecomes infected, the other computers on the network arehighly susceptible to contracting the virus.“85 percent of respondents detected computer securitybreaches within the last 12 months, up 42% from 1996.”—Annual Computer Security Institute and FBI Survey, 2001Trojan Horse ProgramsTrojan horse programs, or trojans, are delivery vehiclesfor destructive code. Trojans appear to be harmless oruseful software programs, such as computer games, butthey are actually enemies in disguise. Trojans can deletedata, mail copies of themselves to e-mail address lists, andopen up computers to additional attacks. Trojans can becontracted only by copying the trojan horse program toa system, via a disk, downloading from the Internet, oropening an e-mail attachment. Neither trojans nor virusescan be spread through an e-mail message itself—they arespread only through e-mail attachments.VandalsWeb sites have come alive through the development ofsuch software applications as ActiveX and Java Applets.These devices enable animation and other special effectsto run, making Web sites more attractive and interactive.However, the ease with which these applications can bedownloaded and run has provided a new vehicle forinflicting damage. A vandal is a software application orapplet that causes destruction of varying degrees. Avandal can destroy just a single file or a major portionof a computer system.AttacksInnumerable types of network attacks have beendocumented, and they are commonly classified in threegeneral categories: reconnaissance attacks, access attacks,and denial of service (DoS) attacks. Reconnaissance attacks are essentially informationgathering activities by which hackers collect data that isused to later compromise networks. Usually, softwaretools, such as sniffers and scanners, are used to map outnetwork resources and exploit potential weaknesses inthe targeted networks, hosts, and applications. Forexample, software exists that is specifically designed tocrack passwords. Such software was created fornetwork administrators to assist employees who haveforgotten their passwords or to determine the passwordsof employees who have left the company without tellinganyone what their passwords were. Placed in the wronghands, however, this software can become a verydangerous weapon. Access attacks are conducted to exploit vulnerabilities insuch network areas as authentication services and FileTransfer Protocol (FTP) functionality in order to gainentry to e-mail accounts, databases, and otherconfidential information. DoS attacks prevent access to part or all of a computersystem. They are usually achieved by sending largeamounts of jumbled or otherwise unmanageable data toa machine that is connected to a corporate network orthe Internet, blocking legitimate traffic from gettingthrough. Even more malicious is a Distributed Denial ofService attack (DDoS) in which the attackercompromises multiple machines or hosts.Cisco SystemsCopyright 2001 Cisco Systems, Inc. All Rights Reserved.Page 4 of 9
Data InterceptionData transmitted via any type of network can be subjectto interception by unauthorized parties. The perpetratorsmight eavesdrop on communications or even alter thedata packets being transmitted. Perpetrators can usevarious methods to intercept the data. IP spoofing, forexample, entails posing as an authorized party in the datatransmission by using the Internet Protocol (IP) address ofone of the data recipients.Social EngineeringSocial engineering is the increasingly prevalent act ofobtaining confidential network security informationthrough non-technical means. For example, a socialengineer might pose as a technical support representativeand make calls to employees to gather passwordinformation. Other examples of social engineering includebribing a coworker to gain access to a server or searchinga colleague’s office to find a password that has beenwritten in a hidden spot.SpamSpam is the commonly used term for unsolicited electronicmail or the action of broadcasting unsolicited advertisingmessages via e-mail. Spam is usually harmless, but it canbe a nuisance, taking up the recipient’s time and storagespace.Like a building, a network requires multiple layers of protectionto be truly secure.After such solutions are instated, tools can be deployedthat periodically detect security vulnerabilities in thenetwork providing ongoing, proactive security. Inaddition, professional network security consultants canbe engaged to help design the proper security solution forthe network or to ensure that the existing security solutionis up to date and safe. With all of the options currentlyavailable, it is possible to implement a securityinfrastructure that allows sufficient protection withoutseverely compromising the need for quick and easy accessto information.Top Ten Security TipsSecurity ToolsAfter the potential sources of threats and the types ofdamage that can occur have been identified, putting theproper security policies and safeguards in place becomesmuch easier. Organizations have an extensive choice oftechnologies, ranging from anti-virus software packagesto dedicated network security hardware, such as firewallsand intrusion detection systems, to provide protection forall areas of the network.1.Encourage or require employees to choosepasswords that are not obvious.2. Require employees to change passwords every90 days.3. Make sure your virus protection subscriptionis current.4. Educate employees about the security risks ofe-mail attachments.5. Implement a complete and comprehensivenetwork security solution.6. Assess your security posture regularly.7. When an employee leaves a company, removethat employee’s network access immediately.8. If you allow people to work from home, providea secure, centrally managed server for remotetraffic.9. Update your Web server software regularly.10. Do not run any unnecessary network services.Cisco SystemsCopyright 2001 Cisco Systems, Inc. All Rights Reserved.Page 5 of 9
Anti-virus PackagesVirus protection software is packaged with mostcomputers and can counter most virus threats if thesoftware is regularly updated and correctly maintained.The anti-virus industry relies on a vast network of users toprovide early warnings of new viruses, so that antidotescan be developed and distributed quickly. With thousandsof new viruses being generated every month, it is essentialthat the virus database is kept up to date. The virusdatabase is the record held by the anti-virus package thathelps it to identify known viruses when they attempt tostrike. Reputable anti-virus software vendors will publishthe latest antidotes on their Web sites, and the softwarecan prompt users to periodically collect new data.Network security policy should stipulate that allcomputers on the network are kept up to date and, ideally,are all protected by the same anti-virus package—if onlyto keep maintenance and update costs to a minimum. It isalso essential to update the software itself on a regularbasis. Virus authors often make getting past the anti-viruspackages their first priority.Security PoliciesWhen setting up a network, whether it is a local areanetwork (LAN), virtual LAN (VLAN), or wide areanetwork (WAN), it is important to initially set thefundamental security policies. Security policies are rulesthat are electronically programmed and stored withinsecurity equipment to control such areas as accessprivileges. Of course, security policies are also written orverbal regulations by which an organization operates. Inaddition, companies must decide who is responsible forenforcing and managing these policies and determine howemployees are informed of the rules and watch guards.Security Policy, Device, and Multidevice Managementfunctions as a central security control room where securitypersonnel monitor building or campus security, initiatepatrols, and activate alarms.What are the policies?The policies that are implemented should control whohas access to which areas of the network and howunauthorized users are going to be prevented from enteringrestricted areas. For example, generally only members ofthe human resources department should have access toemployee salary histories. Passwords usually preventemployees from entering restricted areas, but only if thepasswords remain private. Written policies as basic as towarn employees against posting their passwords in workareas can often preempt security breaches. Customers orsuppliers with access to certain parts of the network, mustbe adequately regulated by the policies as well.Who will enforce and manage the policies?The individual or group of people who police andmaintain the network and its security must have access toevery area of the network. Therefore, the security policymanagement function should be assigned to people whoare extremely trustworthy and have the technicalcompetence required. As noted earlier, the majority ofnetwork security breaches come from within, so thisperson or group must not be a potential threat. Onceassigned, network managers may take advantage ofsophisticated software tools that can help define,distribute, enforce, and audit security policies throughbrowser-based interfaces.Cisco SystemsCopyright 2001 Cisco Systems, Inc. All Rights Reserved.Page 6 of 9
How will you communicate the policies?Policies are essentially useless if all of the involved partiesdo not know and understand them. It is vital to haveeffective mechanisms in place for communicating theexisting policies, policy changes, new policies, andsecurity alerts regarding impending viruses or attacks.IdentityOnce your policies are set, identity methods andtechnologies must be employed to help positivelyauthenticate and verify users and their access privileges.In the future, some passwords may be replaced bybiometrics, which is technology that identifies users basedon physical characteristics, such as fingerprints, eyeprints, or voice prints.Digital CertificatesDigital certificates or public key certificates are theelectronic equivalents of driver’s licenses or passports, andare issued by designated Certificate Authorities (CAs).Digital certificates are most often used for identificationwhen establishing secure tunnels through the Internet,such as in virtual private networking (VPN).Access ControlBefore a user gains access to the network with hispassword, the network must evaluate if the password isvalid. Access control servers validate the user’s identityand determine which areas or information the user canaccess based on stored user profiles. In the physicalsecurity analogy, access control servers are equivalent tothe gatekeeper who oversees the use of the access card.Access Control Servers function like door access cards and thegatekeeper that oversees site security, providing centralizedauthorization, authentication and accounting (AAA) for trafficand users.PasswordsMaking sure that certain areas of the network are“password protected”—only accessible by those withparticular passwords—is the simplest and most commonway to ensure that only those who have permission canenter a particular part of the network. In the physicalsecurity analogy above, passwords are analogous tobadge access cards. However, the most powerful networksecurity infrastructures are virtually ineffective if peopledo not protect their passwords. Many users choose easilyremembered numbers or words as passwords, such asbirthdays, phone numbers, or pets’ names, and othersnever change their passwords and are not very carefulabout keeping them secret. The golden rules, or policies,for passwords are: Change passwords regularly Make passwords as meaningless as possible Never divulge passwords to anyone until leaving thecompanyAccess Control Lists and Firewalls are analogous to door lockson building perimeters that allow only authorized users (thosewith keys or badges) access in or out.FirewallsA firewall is a hardware or software solution implementedwithin the network infrastructure to enforce anorganization’s security policies by restricting access tospecific network resources. In the physical securityanalogy, a firewall is the equivalent to a door lock on aperimeter door or on a door to a room inside of thebuilding—it permits only authorized users, such as thosewith a key or access card, to enter. Firewall technology isCisco SystemsCopyright 2001 Cisco Systems, Inc. All Rights Reserved.Page 7 of 9
even available in versions suitable for home use. Thefirewall creates a protective layer between the networkand the outside world. In effect, the firewall replicates thenetwork at the point of entry so that it can receive andtransmit authorized data without significant delay.However, it has built-in filters that can disallowunauthorized or potentially dangerous material fromentering the real system. It also logs an attemptedintrusion and reports it to the network administrators.EncryptionEncryption technology ensures that messages cannot beintercepted or read by anyone other than the authorizedrecipient. Encryption is usually deployed to protect datathat is transported over a public network and usesadvanced mathematical algorithms to “scramble”messages and their attachments. Several types ofencryption algorithms exist, but some are more securethan others. Encryption provides the security necessary tosustain the increasingly popular VPN technology. VPNsare private connections, or tunnels, over public networkssuch as the Internet. They are deployed to connecttelecommuters, mobile workers, branch offices, andbusiness partners to corporate networks or each other. AllVPN hardware and software devices support advancedencryption technology to provide the utmost protectionfor the data that they transport.Intrusion DetectionOrganizations continue to deploy firewalls as their centralgatekeepers to prevent unauthorized users from enteringtheir networks. However, network security is in manyways similar to physical security in that no one technologyserves all needs—rather, a layered defense provides thebest results. Organizations are increasingly looking toadditional security technologies to counter risk andvulnerability that firewalls alone cannot address. Anetwork-based intrusion detection system (IDS) providesaround-the-clock network surveillance. An IDS analyzespacket data streams within a network, searching forunauthorized activity, such as attacks by hackers, andenabling users to respond to security breaches beforesystems are compromised. When unauthorized activity isdetected, the IDS can send alarms to a managementconsole with details of the activity and can often orderother systems, such as routers, to cut off the unauthorizedsessions. In the physical analogy, an IDS is equivalent to avideo camera and motion sensor; detecting unauthorized orsuspicious activity and working with automated responsesystems, such as watch guards, to stop the activity.Intrusion Detection is analogous to a surveillance cameraand motion sensor detecting activity, triggering alerts, andgenerating an armed response. Scanning is like a securityguard that checks and closes open doors or windows beforethey can be breached.Virtual Private Networks (VPNs) are analogous to armoredcars that carry precious cargo to an assigned drop-off pointto ensure secure and confidential passage.Cisco SystemsCopyright 2001 Cisco Systems, Inc. All Rights Reserved.Page 8 of 9
Network ScanningThe ResultNetwork scanners conduct detailed analyses ofnetworked systems to compile an electronic inventory ofthe assets and detect vulnerabilities that could result in asecurity compromise. This technology allows networkmanagers to identify and fix security weaknesses beforeintruders can exploit them. In the physical securityanalogy, scanning is like conducting a periodic buildingwalk-through to ensure that doors are locked andwindows are closed. It helps to evaluate and understandrisk, thereby allowing corrective action to be taken.As time goes on, more and more new technology will bedeveloped to further improve the efficiency of businessand communications. At the same time, breakthroughs intechnology will provide even greater network security,therefore, greater piece of mind to operate in cutting edgebusiness environments. Provided that enterprises stay ontop of this emerging technology, as well as the latestsecurity threats and dangers, the benefits of networkswill most certainly outweigh the risks.ExpertiseWhile electronic scanning tools can be very thorough indetecting network security vulnerabilities, they may becomplemented with a security assessment by professionalsecurity consultants. A security assessment is aconcentrated analysis of the security posture of a network,highlighting security weaknesses or vulnerabilities thatneed to be improved. Periodic assessments are helpful inensuring that, in the midst of frequent changes in anetwork, the security posture of the network is notweakened. In the physical security analogy, a periodicsecurity assessment such as scanning is like a guardperiodically patrolling the entire secured area, checkinglocks on doors and windows, reporting any irregularitiesthat might exist, and providing guidance for correction.Corporate HeadquartersCisco Systems, Inc.170 West Tasman DriveSan Jose, CA 95134-1706USAwww.cisco.comTel: 408 526-4000800 553-NETS (6387)Fax: 408 526-4100European HeadquartersCisco Systems Europe11, Rue Camille Desmoulins92782 Issy-les-MoulineauxCedex 9Francewww.cisco.comTel: 33 1 58 04 60 00Fax: 33 1 58 04 61 00Want to know more?For further information on network security and howCisco Systems products and technologies help addresssecurity problems and take advantage of the manybenefits networks have to provide, please visit the CiscoSystems Web site at http://www.cisco.com/go/security.Americas HeadquartersCisco Systems, Inc.170 West Tasman DriveSan Jose, CA 95134-1706USAwww.cisco.comTel: 408 526-7660Fax: 408 527-0883Asia Pacific HeadquartersCisco Systems Australia, Pty., LtdLevel 9, 80 Pacific HighwayP.O. Box 469North SydneyNSW 2060 Australiawww.cisco.comTel: 61 2 8448 7100Fax: 61 2 9957 4350Cisco Systems has more than 200 offices in the following countries and regions. Addresses, phone numbers, and fax numbers are listed on theCisco.com Web site at www.cisco.com/go/offices.Argentina Australia Austria Belgium Brazil Bulgaria Canada Chile China PRC Colombia Costa Rica Croatia Czech RepublicDenmark Dubai, UAE Finland France Germany Greece Hong Kong SAR Hungary India Indonesia Ireland IsraelItaly Japan Korea Luxembourg Malaysia Mexico The Netherlands New Zealand Norway Peru Philippines Poland PortugalPuerto Rico Romania Russia Saudi Arabia Scotland Singapore Slovakia Slovenia South Africa Spain SwedenSwitzerland Taiwan Thailand Turkey Ukraine United Kingdom United States Venezuela Vietnam ZimbabweCopyright 2001, Cisco Systems, Inc. All rights reserved. Printed in the USA. Cisco, Cisco IOS, Cisco Systems, and the Cisco Systems logo are registered trademarks of Cisco Systems, Inc. or its affiliates in the U.S.and certain other countries. All other brands, names, or trademarks mentioned in this document or Web site are the property of their respective owners. The use of the word partner does not imply a partnershiprelationship between Cisco and any other company (0012R)03/01 BW
A Beginner’s Guide to Network Security An Introduction to the Key Security Issues for the E-Business Economy With the explosion of the public Internet and e-commerce, private computers, and computer networks, if not adequately secured, are increasingly vulnerable to