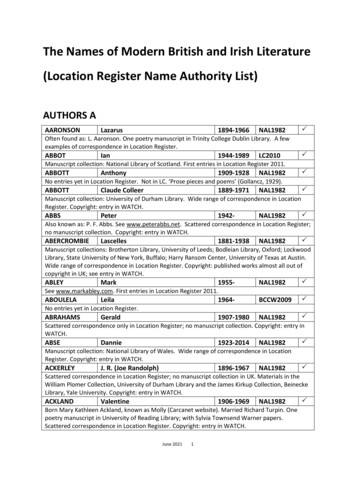
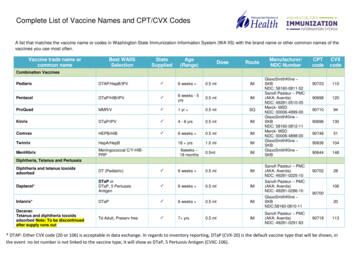
Transcription
FileMaker User GroupAccount Names andPrivilege SetsPaul DzusOctober 6, 2006
Just the basics . Discussing:––––Why you need to secure your databasesSecurity differences between versionsWhat happens during conversion?How to create/edit/delete account names Privilege sets––––– How to secure files & tablesHow to secure scripts & /value listsHow to secure layoutsHow to secure fieldsHow to secure recordsNot discussing:– Web Publishing security– Extended Privileges– External Authentication (LDAP)
Why secure your databases? Remember Tim McGovern’s talk on “sensitive data” in ker/fmug/Top10.pdf–Personally identifying information (PII): if a person's Social Security Number, along withname, is exposed, it could be exploited by identity thieves. Some states have passed lawsrequiring notification.–Protected health information (PHI): if a person’s medical history or status are exposed, itviolates an individual’s fundamental right to privacy. It violates Federal HIPAA law.–Education records: if a student’s information is disclosed, it violates their privacy as definedunder the Family Educational Records and Privacy Act (FERPA).–Other –Faculty surveysSalary informationTelephone Directory informationMIT ID #'sJust a best practice!
Differences betweenpre-7 & post-6 versions “User-based” versus “Role-based”– What a particular person can do versus whata type of user can do Easier Management– Make changes while hosting on server!– Modifications to security schema simplified
The old way
Migrating previous versions to 7 and aboveWhat happens when converted? If no passwords:– Account Name Admin; blank password passwords case-sensitive; account names are not! If passwords:– Account Name password You’ll obviously need to edit these! If Groups:– Privilege Sets created; “duplicates” combined Conversion.log– 10/2/2006 2:12:43 PM, FMUG Oct6th.fp7, 0, 5 access privileges wereconverted.
A new way!
Account names Identify the user and assign privilege set
Privilege sets Built-in:– [Full Access] File Options, Define Database, Accounts/Privileges, File References– [Data Entry Only] Can Create/Edit/Delete Records & value lists but not layouts/scripts– [Read-Only Access] View only! But you can create and customize (very granular!)
How to secure records
How to secure fields
How to secure layouts
How to secure scripts
How to secure scripts #2 Beware!
How to secure value lists
Further Information Upgrading to FileMaker 7: How to employ the new,advanced security system– http://filemaker.com/downloads/pdf/techbrief security.pdf FileMaker 8 Security– http://filemaker.com/downloads/documentation/fm8 security.pdf FileMaker 8.5 User’s Guide– Chapter 5: Protecting databases with accounts and privilege sets– http://filemaker.com/downloads/pdf/fmp85 users guide.pdf FileMaker and HIPAA—A Tool of Compliance– http://www.filemaker.com/downloads/pdf/filemaker and hipaa.pdf
8.5 Release Effort Announced last week:– http://web.mit.edu/swrt/releases/filemaker/ann underway.html Volunteer testers are needed! Contact Cecilia Marra [DCAD] (cmarra@mit.edu;x3-7210), if interested For more information:– http://web.mit.edu/swrt/releases/filemaker/
Thank you! Next meeting:– Friday, November 3rd @ Noon; N42 Demo Center– Guest Speaker! Kevin Cunningham– Consolidating multiple tables into a single file Training @ W92-206 [http://web.mit.edu/sapwebss/PS1/training home.shtml]– CPF0250c-A: FileMaker Pro: Basics October 17th ; 9am-Noon Class FULL / Waitlist– CPF0260c-A: FileMaker Pro: Designing Layouts October 26th & 27th; 9am-Noon– CPF0270c-A: FileMaker Pro: Database Design November 16th & 17th; 9am-Noon
– Make changes while hosting on server! – Modifications to security schema simplified. . Care and Feeding of FileMaker Server