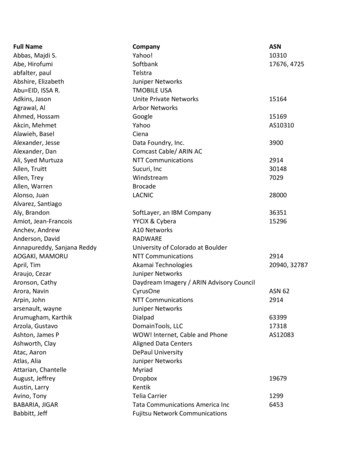
Transcription
https://www.certbus.com/SSCP.html2022 Latest certbus SSCP PDF and VCE dumps DownloadSSCPQ&AsSystem Security Certified Practitioner (SSCP)Pass ISC SSCP Exam with 100% GuaranteeFree Download Real Questions & Answers PDF and VCE file from:https://www.certbus.com/SSCP.html100% Passing Guarantee100% Money Back AssuranceFollowing Questions and Answers are all new published by ISC OfficialExam CenterSSCP PDF Dumps SSCP VCE Dumps SSCP Study Guide1/8
https://www.certbus.com/SSCP.html2022 Latest certbus SSCP PDF and VCE dumps DownloadQUESTION 1Which of the following is NOT an administrative control?A. Logical access control mechanismsB. Screening of personnelC. Development of policies, standards, procedures and guidelinesD. Change control proceduresCorrect Answer: AIt is considered to be a technical control.Logical is synonymous with Technical Control. That was the easy answer. There are three broad categories of accesscontrol: Administrative, Technical, and Physical.Each category has different access control mechanisms that can be carried out manually or automatically. All of theseaccess control mechanisms should work in concert with each other to protect an infrastructure and its data.Each category of access control has several components that fall within it, as shown here:Administrative ControlsPolicy and proceduresPersonnel controlsSupervisory structureSecurity-awareness trainingTestingPhysical Controls Network segregation Perimeter security Computer controls Work area separation Data backupsTechnical ControlsSystem access Network architecture Network access Encryption and protocols Control zone Auditing The followinganswers are incorrect : Screening of personnel is considered to be an administrative control Development of policies,standards, procedures and guidelines is considered to be an administrative control Change control procedures isconsidered to be an administrative control. Reference : Shon Harris AIO v3 , Chapter - 3 : Security ManagementPractices , Page : 52-54QUESTION 2Which of the following statements pertaining to stream ciphers is correct?A. A stream cipher is a type of asymmetric encryption algorithm.B. A stream cipher generates what is called a keystream.SSCP PDF Dumps SSCP VCE Dumps SSCP Study Guide2/8
https://www.certbus.com/SSCP.html2022 Latest certbus SSCP PDF and VCE dumps DownloadC. A stream cipher is slower than a block cipher.D. A stream cipher is not appropriate for hardware-based encryption.Correct Answer: BA stream cipher is a type of symmetric encryption algorithm that operates on continuous streams of plain text and isappropriate for hardware-based encryption.Stream ciphers can be designed to be exceptionally fast, much faster than any block cipher. A stream cipher generateswhat is called a keystream (a sequence of bits used as a key).Stream ciphers can be viewed as approximating the action of a proven unbreakable cipher, the one-time pad (OTP),sometimes known as the Vernam cipher. A one-time pad uses a keystream of completely random digits. The keystreamiscombined with the plaintext digits one at a time to form the ciphertext. This system was proved to be secure by ClaudeShannon in 1949. However, the keystream must be (at least) the same length as the plaintext, and generatedcompletelyat random. This makes the system very cumbersome to implement in practice, and as a result the one-time pad has notbeen widely used, except for the most critical applications.A stream cipher makes use of a much smaller and more convenient key -- 128 bits, for example. Based on this key, itgenerates a pseudorandom keystream which can be combined with the plaintext digits in a similar fashion to the onetimepad. However, this comes at a cost: because the keystream is now pseudorandom, and not truly random, the proof ofsecurity associated with the one-time pad no longer holds: it is quite possible for a stream cipher to be completelyinsecureif it is not implemented properly as we have seen with the Wired Equivalent Privacy (WEP) protocol.Encryption is accomplished by combining the keystream with the plaintext, usually with the bitwise XOR operation.Source: DUPUIS, Clement, CISSP Open Study Guide on domain 5, cryptography, April 1999.More details can be obtained on Stream Ciphers in RSA Security\\'s FAQ on Stream Ciphers.QUESTION 3Which type of control is concerned with avoiding occurrences of risks?A. Deterrent controlsB. Detective controlsC. Preventive controlsD. Compensating controlsCorrect Answer: CPreventive controls are concerned with avoiding occurrences of risks while deterrent controls are concerned withdiscouraging violations. Detecting controls identify occurrences and compensating controls are alternative controls,SSCP PDF Dumps SSCP VCE Dumps SSCP Study Guide3/8
https://www.certbus.com/SSCP.html2022 Latest certbus SSCP PDF and VCE dumps Downloadused tocompensate weaknesses in other controls.Supervision is an example of compensating control.Source: TIPTON, Hal, (ISC)2, Introduction to the CISSP Exam presentation.QUESTION 4At what stage of the applications development process should the security department become involved?A. Prior to the implementationB. Prior to systems testingC. During unit testingD. During requirements developmentCorrect Answer: DSource: TIPTON, Hal, (ISC)2, Introduction to the CISSP Exam presentation.QUESTION 5The International Standards Organization / Open Systems Interconnection (ISO/OSI) Layers does NOT have which ofthe following characteristics?A. Standard model for network communicationsB. Used to gain information from network devices such as count of packets received and routing tablesC. Enables dissimilar networks to communicateD. Defines 7 protocol layers (a.k.a. protocol stack)Correct Answer: BThe International Standards Organization / Open Systems Interconnection (ISO/OSI) Layers and CharacteristicsStandard model for network communications enables dissimilar networks to communicate, Defines 7 protocol layers(a.k.a.protocol stack) Each layer on one workstation communicates with its respective layer on another workstation usingprotocols (i.e. agreed-upon communication formats) "Mapping" each protocol to the model is useful for comparingprotocols.Mnemonics: Please Do Not Throw Sausage Pizza Away (bottom to top layer)All People Seem To Need Data Processing (top to bottom layer).Source: STEINER, Kurt, Telecommunications and Network Security, Version 1, May 2002, CISSP Open Study Group(Domain Leader: skottikus), Page 12.SSCP PDF Dumps SSCP VCE Dumps SSCP Study Guide4/8
https://www.certbus.com/SSCP.html2022 Latest certbus SSCP PDF and VCE dumps DownloadQUESTION 6What refers to legitimate users accessing networked services that would normally be restricted to them?A. SpoofingB. PiggybackingC. EavesdroppingD. Logon abuseCorrect Answer: DUnauthorized access of restricted network services by the circumvention of security access controls is known as logonabuse. This type of abuse refers to users who may be internal to the network but access resources they would notnormally be allowed.Source: KRUTZ, Ronald L. and VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of ComputerSecurity, John Wiley and Sons, 2001, Chapter 3: Telecommunications and Network Security (page 74).QUESTION 7Which of the following statements pertaining to using Kerberos without any extension is false?A. A client can be impersonated by password-guessing.B. Kerberos is mostly a third-party authentication protocol.C. Kerberos uses public key cryptography.D. Kerberos provides robust authentication.Correct Answer: CKerberos is a trusted, credential-based, third-party authentication protocol that uses symmetric (secret) keycryptography to provide robust authentication to clients accessing services on a network.Because a client\\'s password is used in the initiation of the Kerberos request for the service protocol, passwordguessing can be used to impersonate a client.Here is a nice overview of HOW Kerberos is implement as described in RFC 4556:1. Introduction The Kerberos V5 protocol [RFC4120] involves use of a trusted third party known as the Key DistributionCenter (KDC) to negotiate shared session keys between clients and services and provide mutual authenticationbetween them. The corner-stones of Kerberos V5 are the Ticket and the Authenticator. A Ticket encapsulates asymmetric key (the ticket session key) in an envelope (a public message) intended for a specific service. The contentsof the Ticket are encrypted with a symmetric key shared between the service principal and the issuing KDC. Theencrypted part of the Ticket contains the client principal name, among other items. An Authenticator is a record that canbe shown to have been recently generated using the ticket session key in the associated Ticket. The ticket session keyis known by the clientwho requested the ticket. The contents of the Authenticator are encrypted with the associated ticket session key. TheSSCP PDF Dumps SSCP VCE Dumps SSCP Study Guide5/8
https://www.certbus.com/SSCP.html2022 Latest certbus SSCP PDF and VCE dumps Downloadencrypted partof an Authenticator contains a timestamp and the client principalname, among other items.As shown in Figure 1, below, the Kerberos V5 protocol consists of thefollowing message exchanges between the client and the KDC, and the client and the application service:The Authentication Service (AS) ExchangeThe client obtains an "initial" ticket from the Kerberosauthentication server (AS), typically a Ticket Granting Ticket(TGT). The AS-REQ message and the AS-REP message are the requestand the reply message, respectively, between the client and theAS.The Ticket Granting Service (TGS) ExchangeThe client subsequently uses the TGT to authenticate and request aservice ticket for a particular service, from the Kerberosticket-granting server (TGS). The TGS-REQ message and the TGS-REPmessage are the request and the reply message respectively betweenthe client and the TGS.The Client/Server Authentication Protocol (AP) ExchangeThe client then makes a request with an AP-REQ message, consistingof a service ticket and an authenticator that certifies theclient\\'s possession of the ticket session key. The server mayoptionally reply with an AP-REP message. AP exchanges typicallynegotiate session-specific symmetric keys.Usually, the AS and TGS are integrated in a single device also knownas the KDC. -------------- --------- KDC AS-REQ / ------- / / -------------- SSCP PDF Dumps SSCP VCE Dumps SSCP Study Guide6/8
https://www.certbus.com/SSCP.html2022 Latest certbus SSCP PDF and VCE dumps Download// / AS-REP / / TGS-REQ TGS-REP // // / --------- // // // v/v ------- ------ ----------------- Client ------------ Application AP-REQ Server SSCP PDF Dumps SSCP VCE Dumps SSCP Study Guide7/8
https://www.certbus.com/SSCP.html2022 Latest certbus SSCP PDF and VCE dumps DownloadTo Read the Whole Q&As, please purchase the Complete Version from Our website.Try our product !100% Guaranteed Success100% Money Back Guarantee365 Days Free UpdateInstant Download After Purchase24x7 Customer SupportAverage 99.9% Success RateMore than 800,000 Satisfied Customers WorldwideMulti-Platform capabilities - Windows, Mac, Android, iPhone, iPod, iPad, KindleWe provide exam PDF and VCE of Cisco, Microsoft, IBM, CompTIA, Oracle and other IT Certifications.You can view Vendor list of All Certification Exams offered:https://www.certbus.com/allproductsNeed HelpPlease provide as much detail as possible so we can best assist you.To update a previously submitted ticket:Any charges made through this site will appear as Global Simulators Limited.All trademarks are the property of their respective owners.Copyright certbus, All Rights Reserved.SSCP PDF Dumps SSCP VCE Dumps SSCP Study GuidePowered by TCPDF (www.tcpdf.org)8/8
2022 Latest certbus SSCP PDF and VCE dumps Download QUESTION 6 What refers to legitimate users accessing networked services that would normally be restricted to them?