Transcription
ISO/IEC 27701Privacy Information ManagementYour implementation guide
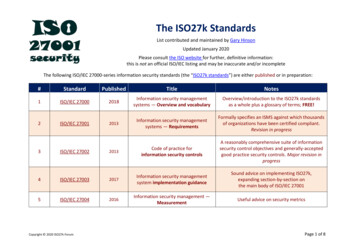
What is ISO/IEC 27701?ISO/IEC 27701 is the international standard for a Privacy Information Management System (PIMS). It’sa privacy extension to ISO/IEC 27001 Information Security Management and ISO/IEC 27002 SecurityControls.It provides guidance and requirements on the protection of privacy, helping both personally identifiableinformation (PII) processors and PII controllers to put robust data processes and controls in place.This means you can demonstrate accountability for managing PII, instil trust and build strong businessrelationships.Contents B enefits ISO/IEC 27701 clause by clause BSI Training Academy BSI BusinessImprovement Software2
What kind of organizations can benefitfrom ISO/IEC 27701?ISO/IEC 27701 is ideal for all types and sizes of organizations who want to demonstrate that they takeprotecting personal information seriously.Whether you’re a public or private company, government entity or not-for-profit organization, if yourorganization is responsible for processing PII within an information security management system thenISO/IEC 27701 is for you.Specific organizational roles include: PII controllers (including those who are joint PII controllers) PII processorsBenefits of ISO/IEC 27701Supportscompliancewith privacyregulationsBuilds trust inmanaging scomplexity byintegrating withISO/IEC 27001Clarifiesroles andresponsibilities
The key requirements ofISO/IEC 27701Clause 1: ScopeClause 3: Terms and definitionsThis sets out the requirements for the managementsystem and its intended application.This section provides a couple of additional definitionsfor important terms used throughout the standard thatare not included in ISO/IEC 27000 and ISO/IEC 29100ISO/IEC 27701 is aimed at providing requirementsand guidance to establish, implement, maintain andimprove a privacy information management systemin the form of an extension to ISO/IEC 27001 andISO/IEC 27002. Focused on both PII controllers and PIIprocessors who hold responsibility and accountabilityfor processing PII.Clause 4: GeneralThis clause ‘sets the scene’ for ISO/IEC 27701. Itprovides an overview of the documents structureand indicates, at a high-level, the location of PIMSspecific requirements in relation to ISO/IEC 27001 andISO/IEC 27002Clause 2: Normative referencesNormative references are documents referred tothroughout a standard. For ISO/IEC 27701 theseinclude:ISO/IEC 27000 Information security managementsystems – overview and vocabularyISO/IEC 27001 Information security managementsystems – requirementsISO/IEC 27002 Code of practice for informationsecurity controlsISO/IEC 29100 Privacy framework4Clause 5: PIMS specific requirementsrelated to ISO/IEC 27001This clause is all about extending information securityrequirements from ISO/IEC 27001 to incorporate theprotection of privacy.As part of the context of the organization, you need todetermine your role as a processor and/or controllerand consider the impact of internal and externalfactors such as privacy specific regulations andcontractual requirements. Depending on your role,relevant controls from Annexes A and/or B need to beimplemented and applied to your existing statement ofapplicability.
You must also consider interested parties associatedwith processing PII, the scope of your PIMS and howyou’ll effectively implement, maintain and continuallyimprove the system.Requirements for leadership, planning, support,operation, performance evaluation and improvementfrom ISO/IEC 27001 must be considered and extendedas appropriate to ensure the protection of privacy. Inparticular, risks to information and processing of PIImust now be assessed and treated appropriately.Clause 6: PIMS specific guidancerelated to ISO/IEC 27002This clause is all about extending information securityguidance from ISO/IEC 27002 to incorporate theprotection of privacy.For example, organizations need to considerthe additional implementation guidance aroundinformation security policies to incorporate relevantprivacy statements, based on compliance, contractualand stakeholder requirements.Clearer guidance is provided on roles andresponsibilities in relation to PII processing. Thisincludes awareness of incident reporting and theconsequences of a privacy breach.Guidance to ensure consideration of PII within yourinformation classification is provided. You mustunderstand the PII your organization processes, whereit is stored and the systems it flows through. Peoplemust also be aware of what PII is and how to recognizeit.More detailed implementation guidance is includedon incident management, removable media, useraccess on systems and services that process PII,cryptographic protection, re-assigning storage spacethat previously stored PII, back-up and recovery of PII,event log reviews, information transfer policies andconfidentiality agreements.Plus, guidance in this clause encourages you toconsider PII up front before data transmission onpublic networks, and as part of system developmentand design.Importantly, supplier relationships, expectations andresponsibilities need addressing.Clause 7: Additional guidance for PIIcontrollersThis clause covers PIMS specific implementationguidance for PII controllers. It relates to controls listedin Annex A.For example, you need to identify the specific purposesfor the PII you process and have a legal basis forprocessing it to comply with relevant laws. Updatesshould be made if the purpose for processing PIIchanges or extends.Guidance also outlines considerations of specialcategory data and consent requirements, privacyimpact assessment requirements to minimize risk toPII principals, contracts with PII processors and clearroles and responsibilities with any joint controllers.You should make it clear to individuals whose PII youprocess why and how you process it, with a contactpoint for any requests. Detailed guidance is includedon consent, withdrawals and PII access, correction orerasure. Third party obligations, handling requests andautomated decision-making guidance is also provided.Finally, privacy by design for processes and systemsshould consider minimum requirements forcollection and processing, the accuracy and qualityof PII, limitations on the amount collected based onthe purpose of processing and end of processingrequirements.Importantly, PII sharing, transfer and disclosureguidance is outlined to help you transfer betweenjurisdictions with supporting records.
Clause 8: Additional guidancefor PII ProcessorsThis clause covers PIMS specific implementationguidance for PII processors. It relates to controls listedin Annex B.For example, customer contracts should address yourorganization's role as a PII Processor to assist withcustomer obligations, including those of PII principals.Prior consent must be made to use PII data formarketing and advertising purposes.Detailed guidance on helping your customer respondto individual requests, managing temporary filescreated during processing, returning, transferring ordisposing PII securely and appropriate transmissioncontrols are included.Finally, PII sharing, transfer and disclosure guidance isdetailed to address jurisdictional transfers, third-partyand sub-contractor requirements and management oflegally binding PII disclosures.Guidance is outlined to identify and maintain thenecessary records to help demonstrate compliancewith agreed PII processing you conduct.AnnexesA number of Annexes are included in ISO/IEC 27701. Annexes A and B are for controllers and processorsrespectively, whilst annexes C – F provide additional knowledge that can support with setting up andoperating an effective PIMS.Annex AAnnex BA list of controls for PII controllers.A list of controls for PII processors.Not all controls will be required, however a justificationfor excluding any control is required in the statement ofapplicabilityNot all controls will be required, however a justificationfor excluding any control is required in the statement ofapplicabilityAnnex CAnnex DMapping of controls for PII controllers to theISO/IEC 2900 privacy principals.Mapping of ISO/IEC 27701 clauses to GDPR articles 5 to49 (except 43).This shows an indication of how compliance torequirements and controls of ISO/IEC 27701 relate to theprivacy principals in ISO/IEC 29100This shows how compliance to requirements and controlsof ISO/IEC 27701 can be relevant to fulfil obligations ofGDPRAnnex EAnnex FMapping of ISO/IEC 27701 clauses to:Details how to apply ISO/IEC 27701 to ISO/IEC 27001 andISO/IEC 27002. 6ISO/IEC 27018 requirements for PII processors inpublic cloudsISO/IEC 29151 for additional controls and guidancefor PII controllers.It clearly maps the extension of information securityterms to incorporate privacy and includes some examplesfor application
Train with BSIBSI is a world leader in helping clients develop the knowledge and skills they need to embed excellencein their organizations. Whether your organization is going to certify or is simply looking to implement aprivacy information management system, our training courses will help you embed the knowledge andmaximize your ISO/IEC 27701 performance.ISO/IEC 27701 courses include:ISO/IEC 27701 RequirementsISO/IEC 27701 Internal auditor One day One day Learn what a PIMS is and understand theISO/IEC 27701 requirements As an existing ISO/IEC 27001 auditor, learn how toconduct audits against ISO/IEC 27701ISO/IEC 27701 Implementation Two days Get the skills to implement an ISO/IEC 27701privacy information management systemBSI Business Improvement SoftwareGain insight and deliver continual improvementsEnsure you get the most from your ISO/IEC 27701 investment with our Business Improvement Software – asolution that can help you effectively manage your privacy information management system. With preconfigured ISO content, it gives you the tools and information necessary to manage essential elements ofyour PIMS.The start of your ISO/IEC 27701 journey is an ideal time to implement BSI BusinessImprovement Software and benefit from: Effective document control Visibility of site and certificate performance Ability to log, track and manage actions related to audits, incidents/events, risk and performance I nsight into trends that help you make business decisions to drive improvement through itscustomizable dashboards and reporting tools7
Why BSI?For over a century BSI has championed what good looks like and driven best practicein organizations around the world. This includes the production of BS 7799, nowISO/IEC 27001, the world’s most popular information security standard. And we haven’tstopped there, addressing the new emerging issues such as cyber, cloud security and nowprivacy with ISO/IEC 27701. That’s why we’re best placed to help you.With the technical know-how and network of industry experts, academics andprofessional bodies, we are committed to drive the privacy agenda for both organizationsand society.To learn more, please visit: bsigroup.comFind out moreCall: 44 (0)345 080 9000Visit: bsigroup.comCopyright 2019, The British Standards Institution. All rights reserved.BSI is the business improvement company that enables organizations to turn standards of bestpractice into habits of excellence. Working with over 86,000 clients across 193 countries, it isa truly international business with skills and experience across a number of sectors includingautomotive, aerospace, built environment, food, and healthcare. Through its expertise inStandards Development and Knowledge Solutions, Assurance and Professional Services, BSIimproves business performance to help clients grow sustainably, manage risk and ultimately bemore resilient.BSI/UK/1651/SC/1119/EN/GRPAbout BSI
a privacy extension to ISO/IEC 27001 Information Security Management and ISO/IEC 27002 Security Controls. It provides guidance and requirements on the protection of privacy, helping both personally identifiable information (PII) processors and PII contro