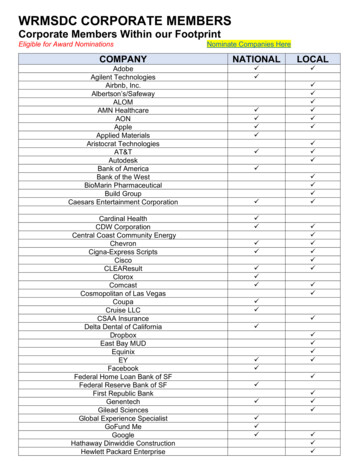
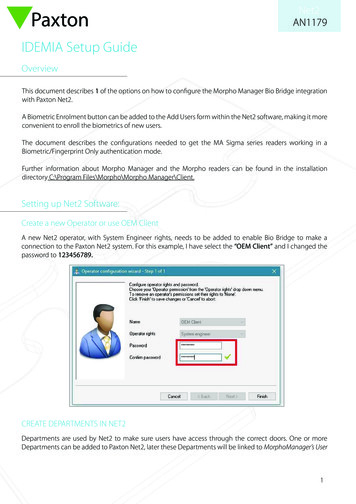
Transcription
WHITE PAPER5G NetworkSlicingA set of logical networks ontop of a shared infrastructure
2
Contents›Executive summary .41. 5G promise .62. Network slicing.83. SIM role .10› Conclusion . 12›Abbreviations .12
4ExecutivesummaryThe promise of 5G is to serve a wide range ofuse cases with three pillars: Mobile Broadband,Critical Communication, and Massive Internet ofThings (IoT). The first release of 5G is clearly focusingon broadband communication to serve the needsof smartphone evolution to offer subscribers morethroughput and a better reactivity of the network. Thesubsequent releases of 5G are now evolving to servemassive IoT, and critical communciation use cases.Another trend in the industry is the virtualizationof network resources. Instead of having one pieceof hardware dedicated and optimized to onenetwork function, the network functions couldbe offered on a commercial off-the-shelf (COTS)hardware or even cloud resources. This enablescost effective and flexible network deployment.Combining the need to address specific use casesand leveraging network virtualization capabilitiesleads to the natural network slicing approach.Rather than having a single network serving differentuse cases, we have network slices that can operate inparallel for specific use cases: broadband, IoT, or criticalcommunication. This leads to additional opportunitiesto allocate network resources to a specific entity; a privatenetwork as a slice dedicated to a factory, for example.In this paper, we will go into more details on networkslicing and then focus on the role of the SIM and itsevolution in this area.
5G NETWORK SLICING615G promiseThe promise of 5G when 3GPP (the standardization body of thecellular world) started to work on it was to address use casesthat may sound contradictory: Massive IoT, Mission CriticalControl, and Enhanced Mobile Broadband. These objectives mayseem incompatible as Massive IoT would require a solution (networkand devices) that consumes very low power for devices running onbattery in order to operate for more than 10 years, whereas EnhancedMobile Broadband requires offering very high bandwidth.Ultra-low complexity10s of bits per secondUltra-high density1 million nodes per km2Ultra-low energy10 years of battery lifeMassive Internetof ThingsDeep coverageTo reach challenginglocationsStrong securitye.g. Health / government /financial trustedExtreme capacity10 Tbps per treme data ratesMulti-Gbps peak rates;100 Mbps userexperienced ratesUltra-low latencyAs low as 1 millisecondDeep awarenessDiscovery and optimizationFigure 1: 3 5G pillarsUltra-high reliability 10-5 per 1 millisecondExterme user mobilityUp to 500 km/h
5G NETWORK SLICING7The first focus of 5G standardization anddeployment was to be able to address one ofthe three pillars, the one that Mobile NetworkOperators are comfortable with and the mostprofitable segment at the time: EnhancedMobile Broadband. This is fully inline with themobile broadband evolution from 2G to 3Gto 4G — offering more and more throughputand better reactivity to the network.This leaves the other two pillars needing tobe better addressed to fulfill the 5G promise:Massive IoT (ex. smart meters) and MissionCritical Control (ex. public safety networks).In addition to the 5G evolution to addressMassive IoT and Mission Critical Control, thereis another trend in the IT industry that isbecoming a reality: network virtualization. Inthe past, a specific hardware was designedfor a specific network function and linked toits dedicated software. Today, there is a needto virtualize these network functions with asoftware that can run on Commercial off-theshelf hardware or even in the cloud. This bringsmore cost efficiency, higher reliability, andmore flexibility in the design of the network.Figure 2: Network virtualizationConflicting network requirements andthe trends towards network virtualizationnaturally lead to the concept of networkslicing and thus the implementation in 5G.
5G NETWORK SLICING82Network slicingIn the past, cellular networks were split into two networkstypes: the Circuit Switch (CS) network managing voice andSMS and the Packet Switch (PS) network dedicated to data.The rationale at the time was that voice cannot wait and datadid not have the same constraints ( jitter, delay ). This was thecase with 3G networks. With 4G came the unif ication of the twoworlds (voice and data) on data network with Voice over IMSover IP. Of course, this merge of networks has been transparentfor the end user that is still able to make phone calls over IPand more data services.In the current context, the two trends mentioned above (contradictorynetwork requirements and network virtualization) have created newchallenges. To cope with contradictory constraints, the network can be splitagain, but virtually, with slices dedicated to one use case.Slice 1:Optimized for low latencySlice 2:Optimized for highbandwidthSlice 3:Optimized for low-powerdevicesCommon infrastructureFigure 3: Network slicingSlice n:Optimized for
5G NETWORK SLICING9A common infrastructure can be virtually split to dedicate resources for aspecific use case. A network slice can be seen as a virtual network that isdedicated to a certain type of service or application (e.g. automotive, IoT, orclassic mobile broadband) with specific requirements: on functionality (e.g.,priority, policy control), in performance (e.g., latency, mobility and data rates),for specific types of users (e.g. public Safety, corporate customers, roamers).For instance, let us imagine a common infrastructure split into three virtualnetworks: one network slice could be dedicated to the Massive IoT usecase — requiring support for a massive number of devices with low powerconsumption but with very limited throughput. This could be the case forsmart meters, for example. Another network slice could be dedicated tocritical communication — use case examples include monitoring factoryrobots or for firefighters. This network slice would have an extremely lowlatency service with very high reliability. While the final network slice couldbe dedicated to mobile broadband to serve smartphones requiring very highthroughput.This opens up additional possibilities for Mobile Network Operators to offera slice of their network and allocate it to a specific factory. Essentially, thisallows MNOs to offer network services to a company that operates a factorywhich requires dedicated network resources for its robots and equipment toensure high reliability of its machines’ connections.Figure 4: Private Network Slice
5G NETWORK SLICING103SIM roleTh e SIM — whether in its traditional, embedded or integratedform — plays a key role in the evolution of network slicing. Forthe sake of brevity, when referring to the SIM throughout thispaper, we are using the umbrella term to cover the SIM in its plasticForm Factor and soldered Form Factor as well as the reprogrammableSIM (eUICC) —where the Mobile Subscription can be changed, andthe iUICC — where the SIM functionality is integrated within thebaseband of the cellular device.The basic functionality of the SIM is to authenticate the usersubscription to the Mobile Network Operator’s network but it can also domuch more. It can pre-configure the device with preferred configurationsloaded by the Mobile Operator into the SIM. This is the case for the networkslicing configuration. The Mobile Operator can configure the SIM withrules to indicate which network slice the traffic of the device applicationwill be directed to and to which a particular charging policy may apply.This is the URSP (UE Route Selection Policy).The URSP is used by the connected devices to determine how to routeapplications traffic to the network slicing. This configuration (file) has beenintroduced with the 3GPP Release 16. 3GPP R16 is the second 5G release,after 3GPP R15 where 5G was first specified by this standard.
5G NETWORK SLICING11High PriorityLow LatencyCorporate customersRoamers, data rateFigure 4: Directing the device application to the right sliceThis URSP file with the SIM requires a specificmemory format call BER-TLV. In simplerterms, that means that the Operating System(OS) of the SIM needs to support this specificway to manage memory in order to load theformat required for this configuration file.The SIM and its evolution needs tosupport the right format of memorymanagement for the Mobile Operator to beable to configure the appropriated routing ofthe User equipment for Policy and Chargingcontrol.
5G NETWORK SLICING12 ConclusionNetwork Slicing is a way for Mobile Network Operators to address specificuse cases and potentially private network use cases. The SIM is playing akey role by hosting the device and application routing policy to one or theother slice. The Operating System of the SIM needs to be able to cope witha specific memory management format called BER-TLV. Mobile NetworkOperators shall then consider this feature in their SIM that has beenintroduced in 3GPP R16 to be able to cope with Network Slicing. Abbreviations3GPP3rd Generation Partnership ProjectBER-TLVBasic Encoding Rules - Type-Length-ValueCS Circuit SwitcheUICC embedded Universal Integrated Circuit CardIMS IP Multimedia SubsystemIP Internet ProtocoleiUICC integrated Universal Integrated Circuit CardOS Operating SystemPS Packet SwitchSIM Subscriber Identity ModuleURSPUser Equipment Route Selection Policy
Copyright 2022. All rights reserved. IDEMIA EN - 05/22 Photo: IDEMIA - Adobe Stock, iStock, IDEMIAAll rights reserved. Specifications and information subject to change without notice.The products described in this document are subject to continuous development and improvement.All trademarks and service marks referred to herein, whether registered or not in specificcountries, are the property of their respective owners.
network function, the network functions could be offered on a commercial off-the-shelf (COTS) hardware or even cloud resources. This enables cost effective and flexible network deployment. Combining the need to address specific use cases and leveraging network virtualization capabilities leads to the natural network slicing approach. Rather than having a single network serving different use .