Transcription
Tech Note--ConfiguringMirror Gateway for Office365 with OktaSymantec CloudSOC Tech Note
Tech Note--Configuring Mirror Gateway for Office 365 with OktaCopyright statementBroadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks ofBroadcom.The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information,please visit www.broadcom.com.Broadcom reserves the right to make changes without further notice to any products or dataherein to improve reliability, function, or design. Information furnished by Broadcom is believedto be accurate and reliable. However, Broadcom does not assume any liability arising out of theapplication or use of this information, nor the application or use of any product or circuitdescribed herein, neither does it convey any license under its patent rights nor the rights ofothers.Copyright 2020 Symantec Corp.2
Tech Note--Configuring Mirror Gateway for Office 365 with OktaTable of ContentsIntroductionPrerequisitesGather information in CloudSOCConfigure Mirror Gateway in OktaCreate a custom attribute and assign it to the Okta user profileCreate a custom SAML app in OktaFederate Okta with CloudSOC and Office 365Configure IDP metadata in CloudSOCMirror Gateway HybrMirror Gateway Hybrid Modeid ModeRevision historyCopyright 2020 Symantec Corp.3
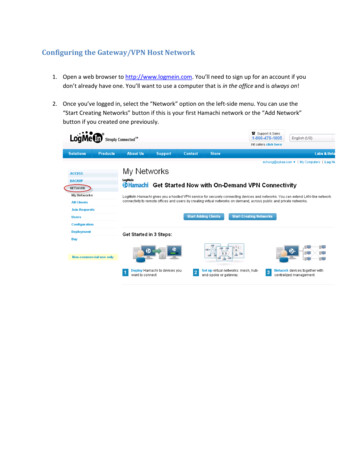
Tech Note--Configuring Mirror Gateway for Office 365 with OktaIntroductionThis Tech Note describes how to configure the Office 365 Gatelet Mirror Gateway featuresusing Okta as an IDP.Mirror Gateway forwards all traffic tracked by the CloudSOC Office 365 Gatelet to theCloudSOC Gateway for monitoring, even traffic originating from devices that do not haveeither Reach agent or the CloudSOC PAC file installed.PrerequisitesYou must already have configured: Okta as your identity provider (IDP) AD server as your directory source Okta - AD sync on the AD server to sync directory with Okta. Azure AD Connect to sync your AD to Microsoft Azure AD (Office 365) SpanVA to sync AD users to CloudSOC as described in the CloudSOC Tech NoteConfiguring DSS Directory Sync An onmicrosoft account for admin accessGather information in CloudSOC1.In CloudSOC, select Store.2. In the Gatelets area of the Store page, click See all.3. Hover over the Office 365 tile and select Activate with Mirror Gateway.Copyright 2020 Symantec Corp.4
Tech Note--Configuring Mirror Gateway for Office 365 with Okta4. On the Configure SAML Federation box, copy the following URLs and paste theminto a text document: SSO Post URL Issuer URL (Entity ID)5. Proceed to the procedures in Configure Mirror Gateway in Okta.Configure Mirror Gateway in OktaPerform the steps in the following sections after you download the necessary metadatafrom the CloudSOC Store.Create a custom attribute and assign it to the Okta user profile1.In Okta, if you are using the Developer Console, open the Classic UI as shown in thefollowing. Some of the tools you use to configure CloudSOC Mirror Gateway areabsent or difficult to find in the Developer Console.2. Choose Directory, and then select Profile Editor to open the Profile Editor.3. Next to the Okta user, click Profile as shown in the following.4. At the top of the Attributes list, click Add Attribute and create a new attribute withthe following variable name:Copyright 2020 Symantec Corp.5
Tech Note--Configuring Mirror Gateway for Office 365 with Oktaoffice365 immutableIdGive the new attribute a description if you want, but leave all other attribute settingsat their defaults.5. Click Save to create the new attribute.6. Choose Directory, and then select Directory Integrations to Navigate to DirectoryIntegrations.7. Click the entry for your Active Directory as shown in the following.8. Click the Settings tab as shown in the following.Copyright 2020 Symantec Corp.6
Tech Note--Configuring Mirror Gateway for Office 365 with Okta9. Scroll down to the Profile Attributes and Mappings area near the bottom of thepage, and in the Attribute Mappings area, click Edit Mappings as shown in thefollowing.10. For Active Directory to Okta, create the following mapping as shown in thefollowing:appuser.externalIdoffice365 immutableId11. Scroll to the top of the page and click Directory, and then select DirectoryIntegrations and click Active Directory.12. Click the Import tab, then click Import Now as shown in the following.Copyright 2020 Symantec Corp.7
Tech Note--Configuring Mirror Gateway for Office 365 with Okta13. Choose Incremental or Full import at your discretion, then click Import as shown inthe following.14. Scroll to the top of the page and click the People tab.15. Click any active user, then click the Profile tab.16. Scroll to the bottom of the Attributes table and check that theoffice365 immutableId attribute is populated with a value as shown in thefollowing.17. Scroll down to the Additional Active Directory Attributes area, and check that theObject GUID is populated with the same value as the office365 immutableIdattribute, as shown in the following.Copyright 2020 Symantec Corp.8
Tech Note--Configuring Mirror Gateway for Office 365 with OktaCreate a custom SAML app in Okta1.Navigate to Applications, and then select Applications, then click Add Applicationas shown in the following.2. Click Create New App as shown in the following.3. For Platform, click Web, mark the SAML2.0 radio button, then click Create.4. Configure the following General Settings, as shown in the following:App NameAny convenient name, such as "Office 365 RP."App LogoLeave blankDo not display applicationicon to usersMarkDo not display applicationicon in the Okta Mobile appClear (unchecked)Copyright 2020 Symantec Corp.9
Tech Note--Configuring Mirror Gateway for Office 365 with Okta5. Click Next.6. Configure the following SAML settings, as shown in the following. Leave all othersettings in their default states:Single sign on URLPaste the SSO Post URL you got from the CloudSOC ActivateMirror Gateway box.Audience URIPaste the Issuer URL (Entity ID) you got from the CloudSOCActivate Mirror Gateway box.7. In the Attribute Statements (Optional) area, add the following statement, as shown inthe following:Copyright 2020 Symantec Corp.10
Tech Note--Configuring Mirror Gateway for Office 365 with OktaNameName 65 immutableId8. Click the Add Another button and add another attribute with the name 'EmailID' andin the value option select user.email:9. Click Next.10. On the Feedback page, mark the following buttons as shown in the following: I'm an Okta customer adding an internal app This is an internal app that we have createdCopyright 2020 Symantec Corp.11
Tech Note--Configuring Mirror Gateway for Office 365 with Okta11. Click Finish.Okta redirects you to the Sign On tab for the app as shown in the following.12. Right-click the link for Identity Provider metadata and select Copy Link Address, asshown in the following.13. Paste the metadata URL into the text file you use to record URLs.Copyright 2020 Symantec Corp.12
Tech Note--Configuring Mirror Gateway for Office 365 with Okta14. Click the Assignments tab and assign the app to your users and groups.Federate Okta with CloudSOC and Office 365At an Azure PowerShell command prompt, use the commands in the following to federateOkta with CloudSOC and Office 365:1.Declare your credentials: UserCredential Get-CredentialWhen prompted, enter the Office 365 credentials for the domain you want tofederate.2. Login with your credentials:Connect-MsolService -Credential UserCredential3. Determine the SLO URL from the SSO Post URL by finding and removing"/bcsamlpost". For example, if the SSO Post URL you copied from the CloudSOCStep 1 box is:https://saml-proxy.edgemycompany.co/saml/casb rp samlrealm/bcsamlpost/proxy/5c5fb4 The SLO URL would be:https://saml-proxy.edgemycompany.co/saml/casb rp samlrealm/proxy/5c5fb4 4. Declare the following variables: domain yourdomain .com issuer Paste the Issuer URL (Entity ID) you copied from the CloudSOC Step 1 box ssoUrl Paste the SSO Post URL you copied from the Step 1 box sloUrl Paste the SLO URL you determined from the SSO Post URL certificateFile Enter the location of the Federation Certificate file youdownloaded from the Step 1 box in the format "C:\rp\prod-cert.pem" certificate [IO.File]::ReadAllText( certificateFile) certificate certificate.replace("-----BEGIN CERTIFICATE-----", "") certificate certificate.replace("-----END CERTIFICATE-----", "")Copyright 2020 Symantec Corp.13
Tech Note--Configuring Mirror Gateway for Office 365 with Okta certificate certificate.replace(" r", "") certificate certificate.replace(" n", "")5. Federate OneLogin with CloudSOC and Office 365 using the declared variables:Set-MsolDomainAuthentication -FederationBrandName domain DomainName domain -Authentication federated PreferredAuthenticationProtocol SAMLP -IssuerUri issuer SigningCertificate certificate -PassiveLogOnUri ssoUrl LogOffUri sloUrl6. Verify domain federation settings:Get-MsolDomainFederationSettings -Domain domainPowerShell responds with the federation details as shown in the following example.PS C:\Users\Administrator Get-MsolDomainFederationSettings LogOnUriSigningCertificateSupportsMfa::: tryelasticarpqa2.com: casb rp samlrealm/5c5fb480d0034c56ac952ee889501560 tryelasticarpqa2com: casb rp samlrealm/proxy/5c5fb480d0034c56ac952ee889501560 tryelasticarpqa2com:::: casb rp samlrealm/bcsamlpost/proxy/5c5fb480d003 4c56ac952ee889501560tryelasticarpqa2com: AiBgNVBAMUGyouZWRnZS1lb2UuZWxhc3RpY2Eta.:Configure IDP metadata in CloudSOC1.In CloudSOC, navigate back to Store, and then select Gatelets, and then selectOffice 365.2. Click Activate with Mirror Gateway.Copyright 2020 Symantec Corp.14
Tech Note--Configuring Mirror Gateway for Office 365 with Okta3. Click Next: Provide SSO Provider Metadata.4. In the Metadata from your SSO Provider area, click Metadata URL.5. Paste the link address for the identity provider metadata you copied from Okta inthe section Create a custom SAML App in Okta as shown in the following.6. Click Complete Activation.7. Wait a few minutes, then check the Office 365 Gatelet tile in the store to make sureMirror Gateway is enabled as shown in the following.Mirror Gateway Hybrid ModeBe advised that if you have the Mirror Gateway activated and the Reach agent isauthenticated with “Mirror Gateway Hybrid Mode” enabled, then the Reach agent willcontinue to work in Hybrid Mode. Once you log out of Office 365 and log back in the MirrorGateway will be activated.Copyright 2020 Symantec Corp.15
Tech Note--Configuring Mirror Gateway for Office 365 with OktaRevision historyDateVersionDescription17 June 20191.0Initial release9 July 20191.1Added “Mirror Gateway HybridMode” section.29 july 20191.2Added step 8 to “Create a customSAML app in Okta”Copyright 2020 Symantec Corp.16
either Reach agent or the CloudSOC PAC file installed. Prerequisites You must already have configured: Okta as your identity provider (IDP) AD server as your directory source Okta - AD sync on the AD server to sync directory with Okta. Azure AD Connect to sync your AD