Transcription
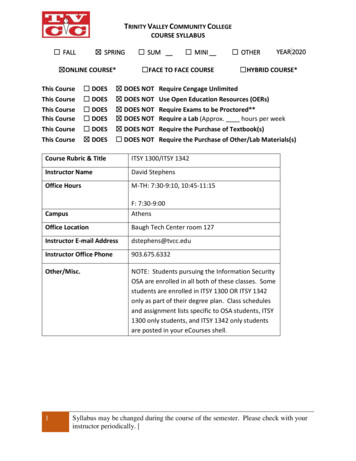
TRINITY VALLEY COMMUNITY COLLEGECOURSE SYLLABUS FALL SPRING ONLINE COURSE*This CourseThis CourseThis CourseThis CourseThis CourseThis Course DOES DOES DOES DOES DOES DOES SUM MINI FACE TO FACE COURSE DOES NOT DOES NOT DOES NOT DOES NOT DOES NOT DOES NOT OTHER HYBRID COURSE*Require Cengage UnlimitedUse Open Education Resources (OERs)Require Exams to be Proctored**Require a Lab (Approx. hours per weekRequire the Purchase of Textbook(s)Require the Purchase of Other/Lab Materials(s)Course Rubric & TitleITSY 1300/ITSY 1342Instructor NameDavid StephensOffice HoursM-TH: 7:30-9:10, 10:45-11:15CampusF: 7:30-9:00AthensOffice LocationBaugh Tech Center room 127Instructor E-mail Addressdstephens@tvcc.eduInstructor Office Phone903.675.6332Other/Misc.NOTE: Students pursuing the Information SecurityOSA are enrolled in all both of these classes. Somestudents are enrolled in ITSY 1300 OR ITSY 1342only as part of their degree plan. Class schedulesand assignment lists specific to OSA students, ITSY1300 only students, and ITSY 1342 only studentsare posted in your eCourses shell.1YEAR 2020Syllabus may be changed during the course of the semester. Please check with yourinstructor periodically.
TRINITY VALLEY COMMUNITY COLLEGECOURSE SYLLABUSCourse Description:ITSY 1300. Fundamentals of Information Security.An introduction to information securing including vocabulary and terminology, ethics, the legalenvironment and risk management. Identification of exposures and vulnerabilities andappropriate countermeasures are addresses. The importance of appropriate planning, policiesand controls are also discussed.ITSY 1342. Information Technology Security.Instruction in security for network hardware, software, and data, including physical security;backup procedures; relevant tools, encryption; and protection from viruses.NOTE: Students pursuing the Information Security OSA are enrolled in all both of these classes.Some students are enrolled in ITSY 1300 OR ITSY 1342 only as part of their degree plan. Classschedules and assignment lists specific to OSA students, ITSY 1300 only students, and ITSY 1342only students are posted in your eCourses shell.Course Co- or Pre-Requisites: None although previous computer experience is helpful.Textbook(s) & ISBN: Please visit the TVCC bookstore onlineRequired/Recommended Reading(s): Please visit the TVCC bookstore onlineRequired Materials: Please visit the TVCC bookstore onlineLearning Outcomes: Upon completion of this course, the student should demonstrate a masteryof the following learning outcomes: 2Access Control and Identity ManagementCryptographyPolicies, Procedures, and AwarenessPhysical SecurityPerimeter DefensesNetwork DefensesHost DefensesSyllabus may be changed during the course of the semester. Please check with yourinstructor periodically.
TRINITY VALLEY COMMUNITY COLLEGECOURSE SYLLABUS Application DefensesData DefensesAssessments and AuditsCourse Requirements: Course content consists of video lectures, interactive lab simulations, printablefact sheets, and traditional online 5-20 question module examsEvaluation/GradingLetter grades will be determined according to the following scale:A 90-100B 80-89C 70-79D 60-69F below 60The LabSim end-of-course Security Pro exam counts as 10% of the final grade for OSA studentswho are enrolled in both ITSY 1300 and 1342.Expected Time Requirement for this Course: Approximately 3-5 hours for students enrolled inITSY 1300 OR ITSY 1342 ONLY; 10-15 hours for OSA (students enrolled in ITSY 1395 and ITSY 1342- expect to spend at least as much time in this course as you would in the traditional, face-to-faceclass) hours per week of time spent reading, reviewing, and completing assignments isrecommended to complete this course.Expected Instructor Response Time Mon-Fri: Students should expect responses to studentinquiries from the instructor within 24 hours Monday-Friday.Expected Instructor Response Time Sat-Sun and holidays: Students should expect responses tostudent inquiries within 72 hours if submitted over the weekend or student holiday. HYBRID AND ONLINE*: Non-Attendance and Financial Aid: If you are receiving financial aid,federal regulations require you to have begun attending the courses for which you are enrolledon or before the census date (e.g., 12th day of each fall and spring semester and 6th day of classeach abbreviated semester). Attendance in an online course is verified by substantialparticipation in the course on or before the census date. TVCC defines substantial participation3Syllabus may be changed during the course of the semester. Please check with yourinstructor periodically.
TRINITY VALLEY COMMUNITY COLLEGECOURSE SYLLABUSin online courses as logging in to the online course AND completing/participating in at least onerequirement of the course. NOTE: Logging in to your online course does not warrant“attending”. For this course, you will be required to complete all of LabSim module 1 beforethe census (12th class for fall/spring or 6th class day for abbreviated semesters) date in order tobe marked as “attending” for purposes of financial aid. Students documented as “not attending”a course upon the census date are assumed (for financial aid purposes) to have NOT begunattendance for that course, negatively affecting their financial aid disbursements. FACE TO FACE: Non-Attendance and Financial Aid: If you are receiving financial aid, federalregulations require you to have begun attending the courses for which you are enrolled on orbefore the census date (e.g., 12th day of each fall and spring semester and 6th day of class eachabbreviated semester). Students documented as “not attending” a course upon the census dateare assumed (for financial aid purposes) to have NOT begun attendance for that course,negatively affecting their financial aid disbursement.Attendance in online course at TVCC is verified by students logging in to the course andsubstantially participating in the course on or before the census date. Students documented as“not attending” an online course upon the census date are assumed (for financial aid purposes)to have NOT begun attendance for that course, and this may negatively affect financial aiddisbursements.***PROCTORED TESTING INFORMATION DOES DOES NOT APPLY TO THIS COURSE Proctored Testing Information: All course work can be completed on your home computer.You MUST have reliable internet access to complete this course.) 4Athens – The Testing Center, located in the Administration Building, is open during regular business hours.In the event that the testing center is closed (visit http://www.tvcc.edu/testing/ for scheduled closings),you can test at the LRC. Please visit the Athens testing site to determine the LRC hours of operation andclosures due to class instruction.Palestine – Students are allowed to test at the LRC of the respective satellite campuses. Please visit thePalestine testing site to determine their hours of operation. NOTE: You MUST arrive at the testing center(s)at least 1 hour prior to closing so that you COMPLETE your testing before they close.Syllabus may be changed during the course of the semester. Please check with yourinstructor periodically.
TRINITY VALLEY COMMUNITY COLLEGECOURSE SYLLABUS Terrell – Students are allowed to test at the A101computer lab during designated hours. Please visit theTerrell testing site to determine their hours of operation. NOTE: You MUST arrive at the testing center(s)at least 1 hour prior to closing so that you COMPLETE your testing before they close.Outline of Course Schedule: There are 3 schedules listed below.1. OSA Schedule for students enrolled in BOTH ITSY 1300 and ITSY 1342.2. ITSY 1300 ONLY for students enrolled in ITSY 1300 ONLY.3. ITSY 1342 ONLY for students enrolled in ITSY 1342 ONLY.This schedule is for OSA students enrolled in both ITSY 1300and ITSY 1342 concurrently.If you are not enrolled in both classes, please see the schedule in eCourses for ITSY 1300 or ITSY1342 ONLY as appropriate.This is an approximate schedule. It is intended to give you an approximate idea of how fast youneed to progress through the course. I strongly suggest you print this schedule and refer to itDAILY to keep from getting behind.It is in your best interest to get ahead of this schedule!1.0 INTRODUCTION1.1 Security Overview1.1.1 The Security Landscape (3:50)1.1.2 Security Concepts (4:14)1.1.3 Security Introduction1.1.4 Practice Questions1.2 Using the Simulator1.2.1 Using the Simulator (5:28)1.2.2 Configure a Security Appliance1.2.3 Install a Security Appliance2.0 SECURITY BASICS2.1 Understanding Attacks2.1.1 Threat Actor Types (10:15)2.1.2 Threat Agents Overview2.1.3 General Attack Strategy (6:06)2.1.4 General Defense Strategy (7:50)2.1.5 Attack and Defense Strategy Overview2.1.6 Practice Questions2.2 Defense /291/291/291/291/301/301/301/301/30Syllabus may be changed during the course of the semester. Please check with yourinstructor periodically.
TRINITY VALLEY COMMUNITY COLLEGECOURSE SYLLABUS2.2.1 The Layered Security Model (5:47)2.2.2 User Education (2:33)2.2.3 Defense Planning Facts2.2.4 Practice Questions2.3 Access Control2.3.1 Identity and Access Management (5:52)2.3.2 Authentication, Authorization, and Accounting (4:29)2.3.3 Access Control Best Practices2.3.4 Practice Questions2.4 Cryptography Basics2.4.1 Cryptography Concepts (5:22)2.4.2 Cryptography Facts2.4.3 Practice Questions2.5 Network Monitoring2.5.1 Network Monitoring (2:40)2.5.2 Network Monitoring Facts2.5.3 Viewing Event Logs (9:39)2.5.4 Practice Questions2.6 Incident Response2.6.1 First Responder (5:22)2.6.2 Basic Forensic Procedures (10:56)2.6.3 Using Forensic Tools (17:05)2.6.4 Creating a Forensic Drive Image (10:02)2.6.5 Incident Response Facts2.6.6 Forensic Investigation Facts2.6.7 Practice Questions3.0 POLICIES, PROCEDURES, AND AWARENESS3.1 Security Policies3.1.1 Security Policies (11:50)3.1.2 Data Privacy Laws (6:32)3.1.3 Security Policy Facts3.1.4 Security Documentation Facts3.1.5 Security Management Facts3.1.6 Data Retention Policies (4:54)3.1.7 Data Retention Facts3.1.8 Practice Questions3.2 Risk Management3.2.1 Risk Management (3:05)3.2.2 Security Controls (2:41)3.2.3 Risk Management Facts3.2.4 Practice /32/42/42/42/42/42/42/52/52/52/52/52/52/5Syllabus may be changed during the course of the semester. Please check with yourinstructor periodically.
TRINITY VALLEY COMMUNITY COLLEGECOURSE SYLLABUS3.3 Business Continuity3.3.1 Business Continuity Planning (2:29)3.3.2 Business Continuity Facts3.3.3 Practice Questions3.4 Manageable Network Plan3.4.1 Manageable Network Plan (8:40)3.4.2 Manageable Network Plan 2 (6:54)3.4.3 Manageable Network Plan Facts3.4.4 Practice Questions3.5 Social Engineering3.5.1 Social Engineering (10:13)3.5.2 Phishing Variations (7:01)3.5.3 Social Engineering Facts3.5.4 Investigating a Social Engineering Attack (8:07)3.5.5 Respond to Social Engineering3.5.6 Practice Questions3.6 App Development and Deployment3.6.1 Development Life Cycle (5:10)3.6.2 SDLC Facts3.6.3 Software Development Models3.6.4 Version Control Management (4:14)3.6.5 Practice Questions3.7 Employee Management3.7.1 Employment Practices (8:12)3.7.2 Employee Management Facts3.7.3 Employee Documents Facts3.7.4 Ethics Facts3.7.5 Practice Questions3.8 Mobile Devices3.8.1 Mobile Device Management (10:20)3.8.2 Mobile Device Security Facts3.8.3 Practice Questions3.9 Third-Party Integration3.9.1 Third-Party Integration Security Issues (7:47)3.9.2 Third-Party Integration Security Facts3.9.3 Practice Questions4.0 PHYSICAL4.1 Physical Threats4.1.1 Physical Security (11:25)4.1.2 Tailgating and Piggybacking (2:37)4.1.3 Physical Security s may be changed during the course of the semester. Please check with yourinstructor periodically.
TRINITY VALLEY COMMUNITY COLLEGECOURSE SYLLABUS4.1.4 Implement Physical Security4.1.5 Practice Questions4.2 Device Protection4.2.1 Hardware Security Guidelines (3:25)4.2.2 Breaking into a System (4:55)4.2.3 Hardware Security Facts4.2.4 Practice Questions4.3 Network Infrastructure Protection4.3.1 Physical Network Protection (4:29)4.3.2 Physical Network Protection Facts4.3.3 Practice Questions4.4 Environmental Controls4.4.1 Environmental Controls (5:01)4.4.2 Securing Environmental Systems (4:03)4.4.3 Environmental Control Facts4.4.4 Fire Protection Facts4.4.5 Practice Questions5.0 PERIMETER5.1 Recon and Denial5.1.1 Reconnaissance (6:41)5.1.2 Performing Reconnaissance (9:09)5.1.3 Reconnaissance Facts5.1.4 Denial of Service (DoS) (4:45)5.1.5 DoS Attack Facts5.1.6 Performing a UDP Flood Attack (4:09)5.1.7 Practice Questions5.2 Spoofing and Poisoning5.2.1 Session and Spoofing Attacks (4:30)5.2.2 Session-Based Attack Facts5.2.3 Performing ARP Poisoning (7:42)5.2.4 Spoofing Facts5.2.5 DNS Attacks (6:09)5.2.6 DNS Attack Facts5.2.7 Examining DNS Attacks (13:48)5.2.8 Prevent Zone Transfers5.2.9 Practice Questions5.3 Security Appliances5.3.1 Security Solutions (4:46)5.3.2 Security Zones (4:34)5.3.3 Security Zone Facts5.3.4 All-In-One Security Appliances 72/172/172/172/182/18Syllabus may be changed during the course of the semester. Please check with yourinstructor periodically.
TRINITY VALLEY COMMUNITY COLLEGECOURSE SYLLABUS5.3.5 Security Solution Facts5.3.6 Configuring Network Security Appliance Access (5:40)5.3.7 Configure Network Security Appliance Access5.3.8 Practice Questions5.4 Demilitarized Zones (DMZ)5.4.1 Demilitarized Zones (6:49)5.4.2 Configuring a DMZ (3:50)5.4.3 Configure a DMZ5.4.4 DMZ Facts5.4.5 Practice Questions5.5 Firewalls5.5.1 Firewalls (6:24)5.5.2 Firewall Facts5.5.3 Configuring a Perimeter Firewall (7:54)5.5.4 Configure a Perimeter Firewall5.5.5 Practice Questions5.6 Network Address Translation (NAT)5.6.1 Network Address Translation (9:54)5.6.2 Configuring NAT from the CLI (6:55)5.6.3 Configuring NAT on an NSA (4:13)5.6.4 NAT Facts5.6.5 Practice Questions5.7 Virtual Private Networks (VPN)5.7.1 Virtual Private Networks (VPNs) (7:03)5.7.2 Configuring a VPN (2:34)5.7.3 Configuring a VPN Client (10:36)5.7.4 Configure a Remote Access VPN5.7.5 Configure a VPN Connection iPad5.7.6 VPN Facts5.7.7 VPN Protocol Facts5.7.8 Practice Questions5.8 Web Threat Protection5.8.1 Web Threat Protection (7:03)5.8.2 Configuring Web Threat Protection (4:26)5.8.3 Configure Web Threat Protection5.8.4 Web Threat Protection Facts5.8.5 Practice Questions5.9 Network Access Protection5.9.1 Network Access Protection (6:34)5.9.2 Implementing NAC with DHCP Enforcement (14:04)5.9.3 NAP 2/232/242/242/242/24Syllabus may be changed during the course of the semester. Please check with yourinstructor periodically.
TRINITY VALLEY COMMUNITY COLLEGECOURSE SYLLABUS5.9.4 Practice Questions5.10 Wireless Overview5.10.1 Wireless Networking Overview (5:58)5.10.2 Wireless Antenna Types (5:01)5.10.3 Wireless Networking Facts5.10.4 Wireless Encryption (5:52)5.10.5 Wireless Encryption Facts5.10.6 Configuring a Wireless Connection (6:47)5.10.7 Configure a Wireless Network5.10.8 Practice Questions5.11 Wireless Attacks5.11.1 Wireless Attacks (6:21)5.11.2 Wireless Attack Facts5.11.3 Using Wireless Attack Tools (7:56)5.11.4 Detecting Rogue Hosts (4:36)5.11.5 Configure Rogue Host Protection5.11.6 Practice Questions5.12 Wireless Defenses5.12.1 Wireless Security Considerations (7:45)5.12.2 Wireless Authentication (5:23)5.12.3 Wireless Authentication Facts5.12.4 Hardening a Wireless Access Point (6:39)5.12.5 Harden a Wireless Network5.12.6 Configure WIPS5.12.7 Configuring a Captive Portal (4:15)5.12.8 Wireless Security Facts5.12.9 Practice Questions6.0 NETWORK6.1 Network Threats6.1.1 Network Threats Overview (8:34)6.1.2 Network Threats Facts6.1.3 Practice Questions6.2 Network Device Vulnerabilities6.2.1 Device Vulnerabilities (6:55)6.2.2 Device Vulnerability Facts6.2.3 Searching defaultpasswords.com (2:18)6.2.4 Securing a Switch (2:56)6.2.5 Secure a Switch6.2.6 Practice Questions6.3 Network Applications6.3.1 Network Application Security 23/23/23/2Syllabus may be changed during the course of the semester. Please check with yourinstructor periodically.
TRINITY VALLEY COMMUNITY COLLEGECOURSE SYLLABUS6.3.2 Configuring Application Control Software (7:46)6.3.3 Network Application Facts6.3.4 Practice Questions6.4 Switch Attacks6.4.1 Switch Attacks (5:42)6.4.2 Switch Attack Facts6.4.3 Practice Questions6.5 Switch Security6.5.1 Switch Features (6:53)6.5.2 Securing Network Switches (6:34)6.5.3 Switch Security Facts6.5.4 Hardening a Switch (10:37)6.5.5 Harden a Switch6.5.6 Secure Access to a Switch6.5.7 Secure Access to a Switch 26.5.8 Practice Questions6.6 Using VLANs6.6.1 VLAN Overview (4:07)6.6.2 Configuring VLANs from the CLI (4:39)6.6.3 VLAN Facts6.6.4 Explore VLANs from the CLI6.6.5 Configuring VLANs (3:09)6.6.6 Explore VLANs6.6.7 Practice Questions6.7 Router Security6.7.1 Router Security (7:03)6.7.2 Router ACLs (2:48)6.7.3 Router Security Facts6.7.4 Configuring ACLs (7:10)6.7.5 Restrict Telnet and SSH Access6.7.6 Permit Traffic6.7.7 Block Source Hosts6.7.8 Practice Questions6.8 Intrusion Detection and Prevention6.8.1 Intrusion Detection (6:30)6.8.2 Detection vs. Prevention Controls (5:36)6.8.3 IDS Facts6.8.4 Implementing Intrusion Monitoring (9:17)6.8.5 Implementing Intrusion Prevention (5:58)6.8.6 Implement Intrusion Prevention6.8.7 Practice 73/73/73/73/73/73/83/83/83/83/83/8Syllabus may be changed during the course of the semester. Please check with yourinstructor periodically.
TRINITY VALLEY COMMUNITY COLLEGECOURSE SYLLABUS6.9 Vulnerability Assessment6.9.1 Vulnerability Assessment (4:23)6.9.2 Vulnerability Assessment Facts6.9.3 Scanning a Network with Nessus (7:26)6.9.4 Scanning a Network with Retina (7:16)6.9.5 Scan for Vulnerabilities 16.9.6 Scan for Vulnerabilities 26.9.7 Scan for Vulnerabilities 36.9.8 Scan for Vulnerabilities 46.9.9 Performing Port and Ping Scans (4:57)6.9.10 Practice Questions6.10 Protocol Analyzers6.10.1 Protocol Analyzers (2:37)6.10.2 Protocol Analyzer Facts6.10.3 Analyzing Network Traffic (13:19)6.10.4 Practice Questions6.11 Remote Access6.11.1 Remote Access (15:04)6.11.2 Remote Access Facts6.11.3 Configuring a RADIUS Solution (9:46)6.11.4 RADIUS and TACACS Facts6.11.5 Practice Questions6.12 Network Authentication6.12.1 Network Authentication Protocols (9:45)6.12.2 Network Authentication Facts6.12.3 LDAP Authentication (5:53)6.12.4 Kerberos Authentication (5:04)6.12.5 Controlling the Authentication Method (6:45)6.12.6 Configure Kerberos Policy Settings6.12.7 Credential Management (4:26)6.12.8 Credential Management Facts6.12.9 Practice Questions6.13 Penetration Testing6.13.1 Penetration Testing (2:38)6.13.2 Penetration Testing Facts6.13.3 Exploring Penetration Testing Tools (11:47)6.13.4 Practice Questions6.14 Virtual Networking6.14.1 Virtual Networking Overview (6:04)6.14.2 Virtual Network Devices (4:13)6.14.3 Configuring Virtual Network Devices /143/143/143/15Syllabus may be changed during the course of the semester. Please check with yourinstructor peri
Instructor E-mail Address dstephens@tvcc.edu Instructor Office Phone 903.675.6332 Other/Misc. NOTE: Students pursuing the Information Security OSA are enrolled in all both of these classes. Some students are enrolled in ITSY 1300 OR ITSY 1342 only as part of their degree plan. Class sche