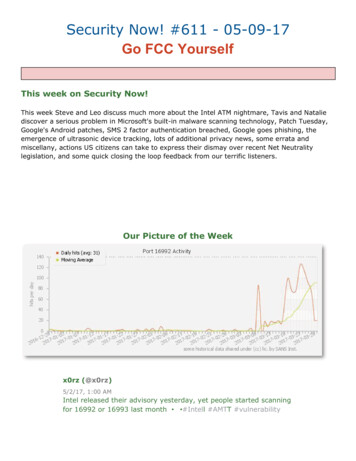
Transcription
GRC 10.0 - Risk Managementfor Mining and MetalPaul Petraschk, SAPSeptember 2012
The Risk Management process starts always with knowingyour businessYour business? 2012 SAP AG. All rights reserved.2
Do You Really Know Your Business?What risks currently impactyour ability to perform?What is the actual status ofyour planned responses?Do some of your activitiesor projects deliver anyindications for higher risks?What will be the overallimpact if multiple risksoccur and how will theyinfluence each other? 2012 SAP AG. All rights reserved.3
Top 5 Requirements12345Holistic overview about the overall risk situation into alloperationsProactively identify and control risks to reduce likelihood andimpactFast and easy way to involve the operational business asknowledge key persons into risk assessmentsEasily maintained risk structure to fulfill the requirements ofcorporate reporting and operational risk managementClear defined accountabilities and responsibilities for risks andresponses 2012 SAP AG. All rights reserved.4
Risk Management OverviewDescription:Reporting and analytic capabilities are essential for management in order to obtain a real time overview of businesscritical risk information.The overview introduces these important features along the Risk Management process which are implemented withSAP GRC Risk ManagementRisk Management ProcessRisk PlanningRisk IdentificationRisk Analysis Strategic Objective Setting Identify risks and Analyse risk usingopportunitiesquantitative or qualitative Align strategic objectivesmethodsto organizational entities Identify risk drivers andimpacts (condition and Document risk Define risk classificationconsequences)relationships(types) Assign Key Risk Indicators Built risk scenarios and Define risk relevant(KRIs – out of scope forand determine riskbusiness activitiespilot)exposure Perform Monte Carlosimulations Prioritize risks based onrisk levelDefine the risk structurefor corporate reportingand operational riskmanagement 2012 SAP AG. All rights reserved.Proactively identificationof risksInvolve operationalbusiness as knowledgekey personsRisk ResponseRisk Monitoring Document preventiveresponses for risks Analyze company’s risksituation Assign responseownership and actions Monitor Key RiskIndicators (KRIs) Perform controlassessments and tests Monitor responseeffectiveness andcompleteness Plan re-assessments andapproval cycles Update risk exposure forstrategic objectives andrisksHolistic overview aboutoverall risk and incident Document occurredsituationincidents and lossesClear definedaccountabilities andresponsibilities for takingactionsHolistic overview aboutoverall risk and incidentsituation5
Risk Planning – Define Risk Management FrameworkGroupRisk PlanningRiskIdentificationRisk Analysis1. Establish Risk Management Goals Define Risk Management ProcessStructure and views Align organizational goals and strategicobjectives Identify risk management process usersEMEAAPJAMERICANorthSouth2. Develop Risk Taxonomy Identify risk activities and businessprocesses Define hierarchal risk classifications Document risk templatesRisk ResponseRiskMonitoring3. Document Risk Criteria Document risk appetite Document risk thresholds Define user roles and authorizations 2012 SAP AG. All rights reserved.6
Risk Identification – Detect operational risksRisk PlanningRiskIdentificationRisk Analysis1. Collect new Risks Propose new risks with only view clicks Report incidents Receive alerts if key risk indicators hitdefined thresholds2. Increase visibility of Risks Use incidents for risk detection Document known risks1Board risks10Documented risks30Known risks100Unknown risks600(Near) incidentsRisk Response3. Improve effective learning process Connect organizations, people, systems and applications Involve all employeesRiskMonitoring 2012 SAP AG. All rights reserved.7
Risk Analysis – Single and collaborative AnalysisRisk PlanningRiskIdentificationRisk Analysis1. Analyze Risks Assess risks with quantitative, qualitative orscore based Methods Perform single or collaborative risk analysis Collect data for risk analysis in the SAP GRCapplication or offline via Adobe InteractiveForms Schedule risk assessments via workflow Receive alerts if key risk indicators hitdefined thresholdsCollaborative Risk AssessmentRisk ResponseDetermine risksin scopeRiskMonitoringTriggerworkflow torecipientMonitorCollaborativeRisk AssessmentSteps performed by Risk Management 2012 SAP AG. All rights reserved.CollaborativeAssessmentRecipient 1CollaborativeAssessmentRecipient laborativeAssessmentRecipient Steps performed by workflow Recipient8
Risk Response – clear defined status and responsibilitiesRisk PlanningRiskIdentificationRisk AnalysisRisk ResponseRiskMonitoring1. Aggregate Risks View aggregated risks by risk classification, activities and business processes Identify risk dependencies2. Scenario (what-if and Monte Carlo) Analysis Create business scenarios and run simulations to visualize impacts and totalloss for different probabilities3. Assign Responses andControls Document responses andownership Assign Controls fromInternal Control System Define Effectiveness andCompleteness Monitor response planprogress 2012 SAP AG. All rights reserved.9
Risk Monitoring – Report on overall risk statusRisk PlanningRiskIdentification1. Flexible Reporting Interactive Dashboards like Risk Heatmap which easily allows to filter and drilldown into risks details as required Add customized static Reports in Crystal Reports and provide Reports forCorporate Level, Management Level and Operational Level Integrate Risk Management data into BI Reports Analyze companies risk situation and monitor mitigation statusRisk AnalysisRisk ResponseRiskMonitoring 2012 SAP AG. All rights reserved.10
Risk Management CycleThe Risk Management Process is not ending with Monitoring. It is more like a continuous RiskManagement Cycle. Enhanced requirements for Monitoring and Reporting as well as organizationalchanges lead to changes in Risk Structure, Organizational and Activity Hierarchy. These are addresses inrisk planning phase where the Risk Management Cycle starts from the beginning.RiskRisk PlanningPlanningRisk IdentificationRisk Monitoring Risk MonitoringRisk IdentificationRisk AnalysisRisk ResponseRisk Response 2012 SAP AG. All rights reserved.Risk Analysis11
DemonstrationOperational Risk Management Overview
Proactively Balance Risk and OpportunitySAP GRC Risk ManagementMANAGE BETTER 2012 SAP AG. All rights reserved.PROTECT BETTERPERFORM BETTER13
Proactively Balance Risk and OpportunitySAP GRC Risk ManagementMANAGE BETTERPROTECT BETTERPERFORM BETTERAutomate manual tasksAutomate monitoringAlign with strategy and planningEmploy best practicesReal-time analysisEmbed analyticsReduce effort and costIndustry-specific solutionsScenario modeling 2012 SAP AG. All rights reserved.14
SAP GRC Risk ManagementAlign enterprise risks with business valueProtect the fundamentalbusiness value driversInsight into themanagement of riskVisibility into catastrophicvalue destroying risks 2012 SAP AG. All rights reserved.15
Thank youPaul PetraschkGRC Senior ConsultantKM Champion - GRC Process ControlSAP Deutschland AG & Co. KGPhone 49/ 6227/ 7-56751Mobil 49/ 160/ 470 33 52Paul.Petraschk@sap.comhttp://www.sap.com/grc
2012 SAP AG. All rights reserved.No part of this publication may be reproduced or transmitted in any form or for any purposewithout the express permission of SAP AG. The information contained herein may bechanged without prior notice.Some software products marketed by SAP AG and its distributors contain proprietarysoftware components of other software vendors.Microsoft, Windows, Excel, Outlook, PowerPoint, Silverlight, and Visual Studio areregistered trademarks of Microsoft Corporation.IBM, DB2, DB2 Universal Database, System i, System i5, System p, System p5, System x,System z, System z10, z10, z/VM, z/OS, OS/390, zEnterprise, PowerVM, PowerArchitecture, Power Systems, POWER7, POWER6 , POWER6, POWER, PowerHA,pureScale, PowerPC, BladeCenter, System Storage, Storwize, XIV, GPFS, HACMP,RETAIN, DB2 Connect, RACF, Redbooks, OS/2, AIX, Intelligent Miner, WebSphere, Tivoli,Informix, and Smarter Planet are trademarks or registered trademarks of IBM Corporation.Linux is the registered trademark of Linus Torvalds in the United States and other countries.Adobe, the Adobe logo, Acrobat, PostScript, and Reader are trademarks or registeredtrademarks of Adobe Systems Incorporated in the United States and other countries.Oracle and Java are registered trademarks of Oracle and its affiliates.UNIX, X/Open, OSF/1, and Motif are registered trademarks of the Open Group.Google App Engine, Google Apps, Google Checkout, Google Data API, Google Maps,Google Mobile Ads, Google Mobile Updater, Google Mobile, Google Store, Google Sync,Google Updater, Google Voice, Google Mail, Gmail, YouTube, Dalvik and Android aretrademarks or registered trademarks of Google Inc.INTERMEC is a registered trademark of Intermec Technologies Corporation.Wi-Fi is a registered trademark of Wi-Fi Alliance.Bluetooth is a registered trademark of Bluetooth SIG Inc.Motorola is a registered trademark of Motorola Trademark Holdings LLC.Computop is a registered trademark of Computop Wirtschaftsinformatik GmbH.SAP, R/3, SAP NetWeaver, Duet, PartnerEdge, ByDesign, SAP BusinessObjects Explorer,StreamWork, SAP HANA, and other SAP products and services mentioned herein as wellas their respective logos are trademarks or registered trademarks of SAP AG in Germanyand other countries.Business Objects and the Business Objects logo, BusinessObjects, Crystal Reports, CrystalDecisions, Web Intelligence, Xcelsius, and other Business Objects products and servicesmentioned herein as well as their respective logos are trademarks or registered trademarksof Business Objects Software Ltd. Business Objects is an SAP company.Citrix, ICA, Program Neighborhood, MetaFrame, WinFrame, VideoFrame, and MultiWinare trademarks or registered trademarks of Citrix Systems Inc.Sybase and Adaptive Server, iAnywhere, Sybase 365, SQL Anywhere, and other Sybaseproducts and services mentioned herein as well as their respective logos are trademarks orregistered trademarks of Sybase Inc. Sybase is an SAP company.HTML, XML, XHTML, and W3C are trademarks or registered trademarks of W3C ,World Wide Web Consortium, Massachusetts Institute of Technology.Crossgate, m@gic EDDY, B2B 360 , and B2B 360 Services are registered trademarksof Crossgate AG in Germany and other countries. Crossgate is an SAP company.Apple, App Store, iBooks, iPad, iPhone, iPhoto, iPod, iTunes, Multi-Touch, Objective-C,Retina, Safari, Siri, and Xcode are trademarks or registered trademarks of Apple Inc.All other product and service names mentioned are the trademarks of their respectivecompanies. Data contained in this document serves informational purposes only. Nationalproduct specifications may vary.IOS is a registered trademark of Cisco Systems Inc.RIM, BlackBerry, BBM, BlackBerry Curve, BlackBerry Bold, BlackBerry Pearl, BlackBerryTorch, BlackBerry Storm, BlackBerry Storm2, BlackBerry PlayBook, and BlackBerry AppWorld are trademarks or registered trademarks of Research in Motion Limited. 2012 SAP AG. All rights reserved.The information in this document is proprietary to SAP. No part of this document may bereproduced, copied, or transmitted in any form or for any purpose without the express priorwritten permission of SAP AG.17
SAP GRC Risk Management Risk Management Process Risk Planning Strategic Objective Setting Align strategic objectives to organizational entities Define risk classification (types) Define risk relevant business activities Identify risks and opportunities quantitative or qualitative Identify risk drivers and impacts (condition and consequences) Assign Key Risk Indicators (KRIs – and determine .