Transcription
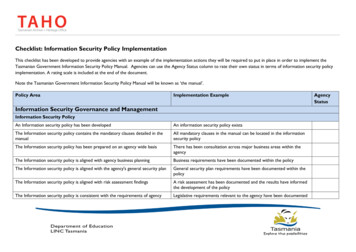
Checklist: Information Security Policy ImplementationThis checklist has been developed to provide agencies with an example of the implementation actions they will be required to put in place in order to implement theTasmanian Government Information Security Policy Manual. Agencies can use the Agency Status column to rate their own status in terms of information security policyimplementation. A rating scale is included at the end of the document.Note the Tasmanian Government Information Security Policy Manual will be known as ‘the manual’.Policy AreaImplementation ExampleInformation Security Governance and ManagementInformation Security PolicyAn Information security policy has been developedAn information security policy existsThe Information security policy contains the mandatory clauses detailed in themanualAll mandatory clauses in the manual can be located in the informationsecurity policyThe Information security policy has been prepared on an agency wide basisThere has been consultation across major business areas within theagencyThe Information security policy is aligned with agency business planningBusiness requirements have been documented within the policyThe Information security policy is aligned with the agency's general security planGeneral security plan requirements have been documented within thepolicyThe Information security policy is aligned with risk assessment findingsA risk assessment has been documented and the results have informedthe development of the policyThe Information security policy is consistent with the requirements of agencyLegislative requirements relevant to the agency have been documentedAgencyStatus
Checklist: Information Security Policy Implementationrelevant legislationwithin the policyThe information security policy is consistent with the requirements of otherrelevant policiesAgency and W-o-G policies relevant to the agency have beendocumented within the policyThe information security policy is communicated to all employees on an ongoingbasisStaff are aware of and trained in the use of the policy with refreshercourses availableThe information security policy is accessible to all employeesThe policy can be easily accessed by all employeesApproval for the information security policy has been obtained from the relevantsenior executivesSenior Executive signoff/endorsement can be located within the policyor briefEndorsement for the information security policy has been obtained from therelevant governance bodyGovernance body signoff/endorsement can be located within the policyor briefThe information security policy is reviewed at least on an annual basisThe date of the policy's last review is no more than 12 months oldThe next review for the information security policy has been scheduledThe date for the policy's next review is documented within the policy,and appropriate review mechanisms in placeThe information security policy is reviewed and evaluated in line with changes tobusiness and information security risks, to reflect the current agency risk profileInformation Security PlanAn Information security plan has been developedIf changes to business or new risks have occurred within the 12 monthreview period, has the policy been updated to reflect these changes?Information security planning is aligned with agency business planningThere has been consultation across major business areas within theagency and business requirements have been documented within theplanInformation security planning is aligned with the agency's general security planGeneral security plan requirements have been documented within theplanInformation security planning is aligned with risk assessment findingsA risk assessment has been documented and the results have informedthe development of the planEndorsement for the information security plan has been obtained from therelevant senior executivesSenior Executive signoff/endorsement can be located within the plan orbriefEndorsement for the information security plan has been obtained from therelevant governance bodyGovernance body signoff/endorsement can be located within the planor briefThe information security plan is reviewed at least on an annual basisThe date of the plan's last review is no more than 12 months oldA threat and risk assessment has been conducted for all ICT assets that create,A threat and risk assessment has been conducted and documented forAn information security plan existsPage 2 of 19
Checklist: Information Security Policy Implementationstore, process or transmit security classified information at least annually or afterany significant change has occurred, such as machinery of GovernmentGovernanceAgency management recognizes the importance of, and demonstrates acommitment to, maintaining a robust agency information security environmentall ICT assets that create, store, process or transmit security classifiedinformation. The date of the last assessment is no more than 12months oldSenior executive management group agenda/minutes includeinformation security mattersInformation Security internal governance arrangements have been establishedInformation security governance body is in operation (e.g. Informationsecurity governance body is meeting as documented in minutes)Information Security internal governance arrangements have been documentedInformation security governance body's terms of reference approved bysenior executive management group/CEOInformation security roles and responsibilities documented andapproved by senior executive managementEmployees with information security roles and responsibilities havesigned a document stating that they understand their roles andresponsibilitiesInformation Security Roles and Responsibilities have been documentedInformation Security Roles and Responsibilities have been establishedEndorsement for the internal governance arrangements has been obtained fromthe relevant senior executivesSign off obtained from senior executive management group/CEO for allinformation security internal governance arrangementsEndorsement for the internal governance arrangements has been obtained fromthe relevant governance bodySign off obtained from relevant governance body (e.g. InformationSteering Committee) has been obtained for information securityinternal governance arrangementsExternal Party GovernanceInformation Security external governance arrangements have been establishedExternal governance arrangements are in operationInformation Security external governance arrangements have been documentedExternal governance arrangements have been documented andapproved by the senior executive management group/CEOAll third party service level agreements, operational level agreements, hostingagreements or similar contracts clearly articulate the level of security requiredStandard templates for service level agreement and operational levelagreements include clauses dealing with information securityrequirementsAll third party service level agreements and operational level agreements areregularly monitoredMinutes of Information security governance body meetings includeoutcomes of routine checks on inclusion of information securityrequirements in SLAs, and audits to ensure third party adherence tothese agreementsPage 3 of 19
Checklist: Information Security Policy ImplementationEndorsement for the external governance arrangements has been obtained fromthe relevant senior executivesEndorsement for the external governance arrangements has been obtained fromthe information security governance bodyInformation Security Risk ManagementRisk Analysis of agencies Information Security Risks has been completedRisk analysis against the agencies information Asset register has been completedSign off obtained from senior executive management group/CEO for allinformation security external governance arrangementsSign off obtained from the information security governance body hasbeen obtained for information security external governancearrangementsRisk management plan has been put in place that includes identification,qualification and prioritisation of risks against acceptance criteria andidentifies appropriate controls to protect against risks.Risk management plan has been put in place for agencies informationassetsResource ManagementRecord SecurityEach agency must have an active Records Management ProgramAgency Records Management Program in Place. Agency has anInformation Management Policy outlining governance arrangements,roles and responsibilities of all staff for the management of informationEach agency must have an identified Records ManagerRecords Manager appointed with up to date statement of dutiesEach agency must have an information asset register that contains the details ofall of the agencies assets regardless of format. This register must identify theinformation asset owner & custodian and all assets must have a disposal categoryand information classification assigned.Information asset register in place, Information Owners and Custodiansare identified on the register. Agency has security classified each asset.Agency has worked with TAHO to determine the disposal classappropriate to the information contained in the asset.Each agency must have an approved disposal scheduleInformation Asset RegisterProcedures for the protective control of information assets (regardless offormat) have been implementedAgency has up to date schedule in place and an active disposal programAll ICT assets that create, store, process or transmit security classifiedinformation are assigned appropriate controls in accordance with the TasmanianGovernment Information Security Classification FrameworkProcedures for the protective control of information assets have beendocumented and approved by the Information security governancebodyAn ICT asset register exists, that documents the security classificationof application and technology assets (in accordance with the policy andthe manual or in the case of national security information relevantnational arrangements) and the corresponding controls that are appliedto that asset (actual controls may be documented elsewhere)Page 4 of 19
Checklist: Information Security Policy ImplementationAll ICT assets (including hardware, software and services) have been identifiedand documentedICT asset register has been completed and is updated at least annuallyAll ICT assets (including hardware, software and services) have been assignedICT asset custodiansICT asset register identifies the ICT asset custodian for all assetsAll ICT assets that provide underpinning and ancillary services must be protectedfrom internal and external threats (e.g. Mail gateways, domain name resolution,time, reverse proxies, remote access and web servers)Information Security ClassificationProcedures for the classification of information assets (regardless of format) havebeen implementedAll ICT assets that provide underpinning and ancillary services havebeen identified and documented. Adequate controls have beenimplemented for these servicesProcedures for the classification of information assets have beendocumented and approved by the Information security governancebodyAll information assets are assigned appropriate classification in accordance withthe Tasmania Government Information Security Classification Framework as aminimumAgency has a complete information asset register, where all informationassets are assigned a classification, or in the case of national securityinformation, as per national arrangementsClassification schemes do not limit the provision of relevant legislation underwhich the agency operatesThe information security classification policy and procedure documentstate that legislative obligations override the classification scheme. Forexample, the security classification of an information asset does notprevent it from being considered for release under the Right toInformation Act 2010Physical Environment SecurityBuilding controls and security areasThe requirements of the Tasmania Government Information SecurityClassification Framework have been implementedAll information assets have been evaluated against the manualBuilding and entry controls for areas used in the processing and storage ofsecurity classified information have been established and maintained in line withthe manualBuilding and entry controls for areas used in the processing and storageof security classified information have been documented approved andare subject to regular updating. Agency records demonstrate that theseare subject to routine checksPhysical security protection controls (commensurate with the securityclassification information levels) have been implemented for all offices, rooms,storage facilities and cabling infrastructure in line with the manualPhysical security protection controls (commensurate with securityclassification levels) have been documented, approved and are subjectto regular updating. Agency records indicate that these are subject toroutine checksControl policies (including clear desk/clear screen) has been implemented inControls for information processing areas have been documented,Page 5 of 19
Checklist: Information Security Policy Implementationinformation processing areas that deal with security classified informationAsset ManagementAll Information assets that store or process information are located in secureareas with access control mechanisms in place to restrict use to authorisedpersonnel onlyapproved and are subject to regular updating. Agency records indicatethat these are subject to routine checksAgency equipment is located in secure areas. Records of routine checksconfirm that these areas are accessible only to authorised personnelPolicies are implemented to monitor and protect the use and/or maintenance ofinformation assets and ICT assets away from premises as required by the manualAgency information security policies address the protection andmonitoring of ICT assets that are offsite. The relevant policy has beenapproved by the agency senio
The Information security policy has been prepared on an agency wide basis : There has been consultation across major business areas within the agency . The Information security policy is aligned with agency business planning : Business requirements have been documented within the policy . The Information security policy is aligned with the agency's general security planFile Size: 294KBPage Count: 19